By Henry Ziemer
The United States’ foundations as a global great power rest in no small part on its status as a regional hegemon. No single country in the Western Hemisphere can make a serious bid to balance Washington’s economic and military might, to say nothing of competing with the close but often-overlooked bonds of trade, culture, and family which constitute vital elements of U.S. strength in the region. Because they are so easily forgotten however, the United States has shown an alarming willingness to take its position in Latin America and the Caribbean (LAC) for granted. The 2022 National Security Strategy proudly proclaims that “No region impacts the United States more directly than the Western Hemisphere,” but the U.S. defense posture in LAC is at risk of being outflanked by extra-hemispheric competitors, the People’s Republic of China (PRC) first among them.
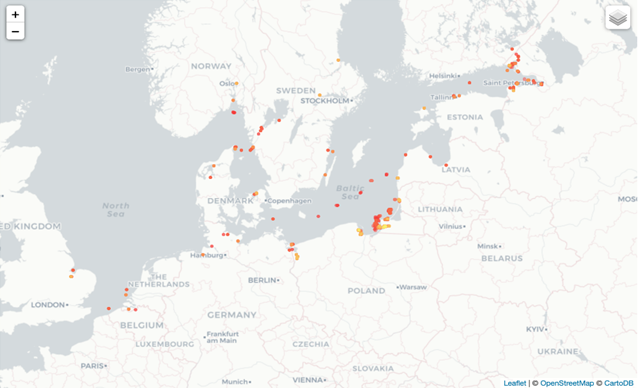
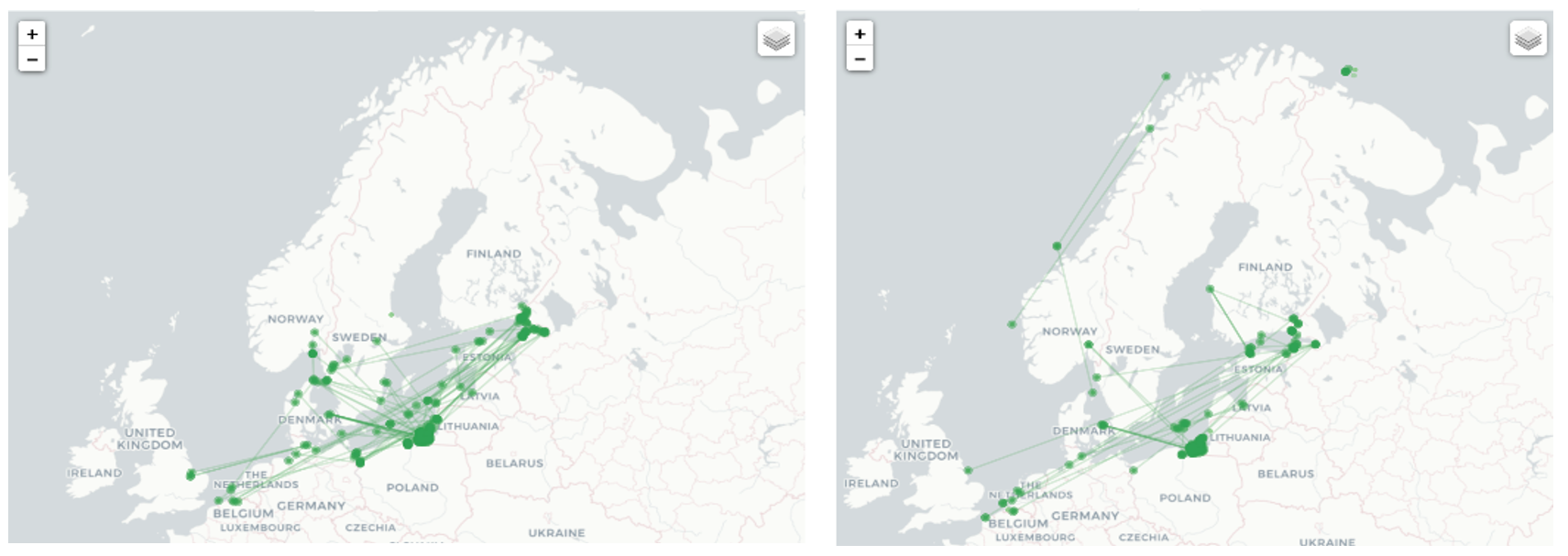
While the PRC has led with economic engagement in its approach to LAC countries, military considerations have not been far behind. China has funded dual-use civilian and military infrastructure, most notably ports and satellite ground stations throughout the region. Today, Chinese-owned or operated ports dot the coastlines of LAC countries, secretive satellite ground stations collect signals intelligence in Argentina, and potentially Cuba, and PRC-supplied weapons have made their way into the hands of dictatorial regimes like Venezuela. In the event of a Pacific War, these capabilities and more would likely be leveraged by China to collect intelligence on and disrupt U.S. operations within the Western Hemisphere, as well as leverage its soft power within the region to court influence and keep LAC governments neutral or even sway some towards overt support of Beijing’s position in the conflict. While it remains improbable that China would seek to contest the Western Hemisphere theater with the United States by 2027, the combination of these hybrid tactics could severely undermine the United States’ position in the very region most critical for U.S. physical security.
Fortunately, the next three years present a number of opportunities for the United States to meaningfully strengthen its southern flank. Specifically, the United States should prioritize better coordination between its Southern Command (SOUTHCOM) and Indo-Pacific Command (INDOPACOM) and strengthen ties with regional allies such as Colombia and Argentina. Finally, any strategy aimed at countering China’s expansion in LAC must incorporate a resource-backed counteroffer to PRC investment in strategic sectors like ports, telecommunications, and power generation.
Why LAC Matters to the PRC
China’s relations within its own “near abroad” understandably figure heavily in most analyses of potential Indo-Pacific conflicts and their outcomes. To a lesser extent, scholars have also looked to Africa and the Middle East as regions that would be critical to secure China’s energy imports during a conflict. Even less understood, however, is the importance that the Western Hemisphere holds for the PRC and its ability to wage war from an ocean away. This is a major blind spot, as LAC has emerged over the past two decades as a keystone region for China’s economy and industry, exemplified by Brazil’s longtime status as the single largest recipient of Chinese foreign direct investment.
LAC, and particularly South America, is a vital source of natural resources to China. While the Middle East is crucial for China’s energy supply, the Americas are a linchpin of China’s food and mineral imports. In 2022, Brazil alone accounted for nearly 23 percent of China’s food imports, and nearly 60 percent of its soybean imports in particular. Maintaining access to LAC’s rich agricultural industry will be critical for China to continue to feed its 1.4 billion inhabitants in the event of a major conflagration.
LAC is also a key supplier of critical minerals to China, especially copper and lithium. Chile and Peru together accounted for half of China’s copper imports in 2022, while as of May 2024 Chile and Argentina provided a staggering 97.7 percent of China’s lithium carbonate. These minerals are essential for China’s economy as a whole, but also its defense sector as they are instrumental in everything from high-capacity batteries used to sustain fleets of autonomous systems, to the wiring and interconnects needed for basic vehicles and communications systems. More high-end capabilities depend on a staggering variety of rare minerals and metals, such as niobium, a critical component in advanced aeronautics and hypersonic missiles. Brazil sits roughly 94 percent of global niobium reserves, leading the PRC to assiduously cultivate an ownership stake over roughly a quarter of Brazilian niobium production.
Finally, China, like Russia, has almost certainly realized the benefits that a presence within the Western Hemisphere can accrue in terms of capacity for horizontal escalation. Moscow, under the so-called Primakov Doctrine has practiced this frequently, pursuing military maneuvers in the Western Hemisphere as a tit-for-tat escalation in response to U.S. support for Ukraine. In July 2024 for instance, Russia dispatched two naval flotillas to Cuba and Venezuela in direct response to U.S. easing of restrictions on long-range strikes by Ukraine into Russian territory. For China, the cultivation of dual-use infrastructure, combined with support for anti-U.S. authoritarian regimes like Cuba, Nicaragua, and Venezuela, would surely prove an asset in the event of war in the Indo-Pacific.
Understanding the Risks
China’s current position in the Western Hemisphere presents three key wartime risks for the United States: (1) control over ports and maritime choke points, (2) dual use of space infrastructure to degrade U.S. space capabilities and threaten the homeland, and (3) disinformation and diplomatic pressure towards U.S. allies and partners.
The first risk is potentially the most proximate and decisive in the event of a major conflict in the Indo-Pacific. Chinese state-owned or based firms currently own or operate at least twelve ports across the LAC region. This includes the ports of Balboa and Cristobal, located on either side of the Panama Canal. The ports are leased and operated by Hutchison Ports, a Hong Kong-based private company which acquired the sites in 1997. While even at the time observers raised concerns over the potential for the Chinese government to exercise undue influence over Hutchison’s operations along this critical maritime artery, over the past decade the PRC’s steady erosion of Hong Kong’s independence only elevates this risk. Indeed, in 2017 a slew of laws, notably the National Intelligence Law, National Defense Mobilization Law, and National Defense Transportation Law, underscored that the Chinese government can enlist the services of any private company for the purpose of nebulously-defined national security interests. Two PRC state-owned companies, the China Communications Construction Company (CCCC) and China Harbor Engineering Company (CHEC), were also part of the winning bid to build the $1.3 billion fourth bridge over the canal, a major undertaking which (after serious delays) has at last begun to move forward.
The confluence of PRC infrastructure and China’s impressive soft power influence in Panama opens up a potential nightmare scenario for the United States in the event of an Indo-Pacific war. In such a scenario, China could either directly, or through a proxy, sabotage port infrastructure on either side of the canal, disrupting or entirely preventing transit through the choke point for a period of time. Not only would this serious impact U.S. trade and shipping, it would cripple the United States’ ability to quickly shift forces between Atlantic and Pacific theaters. With current wargames suggesting the first phases of a naval clash would result in major losses, the added weeks it would take for reinforcements to transit around the Strait of Magellan rather than through the Canal Zone could prove decisive.

While loss of the Panama Canal is one of the most clear-cut risks presented by China’s power position in LAC ports, it is by no means the only way China could leverage maritime infrastructure to its advantage. Ports by their nature collect massive amounts of data on the shape and flow of international trade. The PRC’s planned port and special economic zone in Antigua, together with other PRC-controlled ports, may grant Beijing a one-of-a-kind window into commerce moving throughout the eastern Caribbean and the sea lines of communication which run through it. In the case of ports directly owned or operated by PRC-based firms, like the Brazilian port of Paranaguá or the planned Peruvian megaport of Chancay, this intelligence-gathering capacity could be turned into an operational capability by strategically delaying or seizing key shipments to snarl supply chains for key goods and apply economic pressure on the United States and allies. Finally, presence in regional ports may allow the PRC to carry out more sensitive sabotage operations targeting associated maritime infrastructure, particularly the undersea cables which comprise the backbone of global internet communications. While perhaps not decisive in their own right, China’s position in LAC ports could accord it a host of benefits that are currently underappreciated in planning around a potential Pacific conflict.
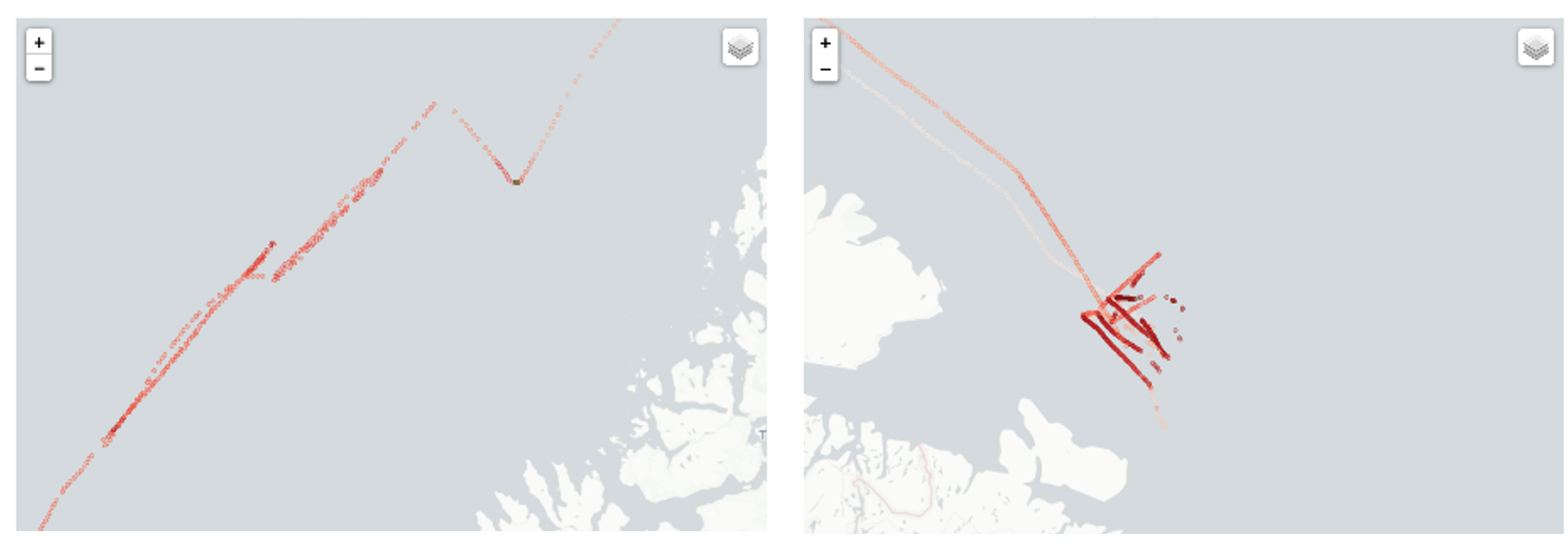
Ports are not the only dual-use infrastructure of note. In recent years, reports have highlighted a proliferation of PRC-operated space infrastructure stretching from the very tip of the Southern Cone through Venezuela, and potentially even into the Caribbean. Most notable among these is the Espacio Lejano Research Station operated by the People’s Liberation Army Strategic Support Force (PLASSF) and located in Neuquén, Argentina. Authorized in 2014 under the government of President Cristina Fernández de Kirchner, the site has become notorious as a “black box” which even Argentine government authorities struggle to gain access to. To date, two inspections have been conducted of the facility, one in 2019 and another more recently under the Milei administration in April 2024 – indicating that serious political will is needed to gain access. In both cases, the Argentine delegation coordinated with the Chinese embassy prior to arrival, and the overall inspection process was relatively perfunctory, doing little to assuage U.S. or Argentine concerns about the facility’s potential for military use.
Neuquén was notably also the first ground station operated by the PRC outside Chinese territory and capable of providing telemetry tracking and control (TT&C) which enables the maneuver and operation of satellites and other orbital vehicles. The facility’s strategic location in the southern hemisphere was also particularly important to supply TT&C capabilities for China’s Chang’e 4 and 5 lunar probes. Neuquén, and similar ground stations in turn compliment China’s growing space presence in Antarctica where in 2023 the PRC announced plans to begin construction of a new dual-use satellite ground station at its Zhongshan research base. TT&C is not just important for satellites and other scientific craft, it is vital for the operation of hypersonic glide vehicles, which conduct complex maneuvers that depend on ground data links for guidance and to better evade missile defenses. China, which according the Congressional Research Service, has conducted 20 times as many hypersonic weapon tests as the United States, could use this network of ground stations in the event of a conflict to strike at the United States from the south, in doing so evading U.S. missile defenses which are primarily concentrated on northern approaches. Chinese space infrastructure in LAC could furthermore help the PRC collect key data on the orbits and locations of satellites in doing so enabling PRC anti-satellite warfare capabilities during a Pacific war scenario.
The final risk involves PRC use of diplomatic influence alongside dis- or mis-information campaigns to shape the political environment in LAC to its favor in the event of a war with the United States. Key targets in such a scenario would likely be the seven LAC countries which still recognize Taiwan instead of the PRC. Beijing would undoubtedly seek to isolate and pressure these countries to shift their recognition prior to or even during a PRC invasion of the island. China could cooperate with other U.S. adversaries to magnify the effect of its disinformation campaigns. According to one report, in Argentina, Chinese and Russian media outlets work in concert with one another to produce “a virtuous cycle of disinformation.” Critically, these efforts would not need to actively sway countries into fully backing China’s campaign (with the exception of those regimes like Venezuela and Nicaragua likely predisposed to do so already), but would instead merely need to convince governments to remain on the sidelines.
China could also use its economic heft as the number one or two trading partner for a majority of LAC countries to ensure neutrality, if not support from countries in the region. Again, the case of Russia proves instructive of how an authoritarian regime can deploy messaging and economic pressure to compel LAC governments. Shortly after his inauguration, Ecuadorian President Daniel Noboa proposed selling $200 million in legacy Russian and Soviet weaponry to the United States in exchange for new equipment (the United States would presumably pass the weapons it received along to Ukraine). Moscow retaliated by threatening phytosanitary restrictions on Ecuadorian banana imports, while launching a media push to claim that if the deal moved forward, Ecuador would make itself a belligerent on the side of Ukraine. The pressure worked, Noboa relented, and Ecuador’s banana exports continued apace. China, which carries significantly more economic weight in the region than Russia could prove a frightening prospect indeed for any government considering taking a vocal stance against the PRC in wartime.
Taken together, the PRC has quietly amassed a host of capabilities within the Western Hemisphere to give it both tactical and strategic advantages against the United States in the event of a crisis or conflict in the Indo-Pacific. The United States, for its part, has been slow to react to the scope of this threat and adjust priorities in LAC accordingly.
Bolstering Readiness in the United States’ Shared Neighborhood
There are a number of steps the United States can and should take between now and 2027 to gird itself and its regional allies in preparation for potential conflict with China.
Better Integrate SOUTHCOM in Pacific War Planning: A lack of integration across U.S. combatant commands risks cultivating a myopic view of Pacific war. Given the PRC and PLA’s global ambitions, any future conflict with China is unlikely to be restricted solely to one theater. As the above sections have illustrated, there are a number of areas where China could pursue a horizontal escalation strategy to gain an edge against the United States. Fostering greater exchange and intelligence sharing across combatant commands should be a priority to ensure the United States is ready to fight and win a war on multiple fronts. One early step could be to create a designated role for SOUTHCOM in key Pacific exercises like the Rim of the Pacific maritime warfare exercise. LAC militaries such as Chile, Colombia, Ecuador, and Peru, already participate in this exercise. Carving out a greater role for SOUTHCOM could help bolster U.S. defense ties with regional militaries and build closer partnerships across combatant commands.
Another area for increased cooperation could be a cross-cutting effort across SOUTHCOM, INDOPACOM, and partner governments to tackle illegal, unreported, and unregulated fishing, a threat which plagues communities and ecosystems across the Pacific. While not directly applicable in a warfighting scenario, such an effort would serve to build greater partnership and information sharing between combatant commands, and build goodwill among partners throughout the Pacific domain.
Double Down on Defense Cooperation: While China has made headway in defense cooperation activities, the United States remains by far the preeminent security partner for the vast majority of LAC countries. However, more can be done to strengthen these ties and build partner capacity to respond to potential malign PRC activity in the hemisphere. One easy step would be to amend the Department of Defense’s Section 312 and 321 requirements that foreign military education training focus on “developing countries.” The Department of Defense’s current standards for designating a country as “developing” prevent partners like Chile, Panama, Uruguay, and most recently Guyana, from benefiting from U.S. training programs. Amending these to include a more nuanced standard would open the door to a much wider array of military-to-military engagement.
Furthermore, the United States should seek to rise to the occasion in cases where LAC governments have already expressed interest in a closer security partnership. Ecuador, which is currently contemplating reversing a constitutional prohibition on foreign military basing to allow for a reopening of the former U.S. naval base at Manta could be a key ally in this effort. Argentina, which is currently pursuing an ambitious military modernization effort, and has expressed a desire to rise to NATO Global Partner status, could be another.
Harden Allies Against Chinese Economic Coercion: China’s investments in critical infrastructure throughout the region pose risks not only for the United States, but its LAC allies and partners as well. For instance, two PRC based companies, China Three Gorges Corporation and China Southern Power Grid International, now collectively control the entirety of Lima, Peru’s power supply. Combined with the forthcoming port of Chancay, China has a number of vectors through which it can apply pressure against a Peruvian government seeking to pursue a policy against Beijing’s interests. The State Department could lead a regionwide effort with allies and partners to map and evaluate risks posted by Chinese investments in critical infrastructure. The findings of this review should also be passed along to the U.S. Development Finance Corporation for review and to help prioritize investments aimed at reducing the amount of influence China can wield over LAC government through its infrastructure projects and trade links.
Conclusion
Future conflicts will not be constrained to a single geographic region. In the event of a Pacific war between the PRC and United States, LAC will almost undoubtedly find itself a zone of contention, whether it wishes it or not. Failure to incorporate this understanding into U.S. contingency planning for such a conflict therefore creates risks not just for the United States itself, but also its regional allies and partners who may find themselves in the crosshairs of PRC coercive efforts. There is still time to patch key vulnerabilities in the region, but a recognition LAC’s important role in future global crises cannot come soon enough.
Henry Ziemer is an Associate Fellow with the Americas Program at the Center for Strategic and International Studies (CSIS). His research focuses on great power competition, transnational organized crime, as well as security and defense in the Western Hemisphere. His writing and commentary have been featured in CSIS, War on the Rocks, the Financial Times, and The Wall Street Journal.
Featured Image: The Panama Canal. (Photo via Wikimedia Commons)