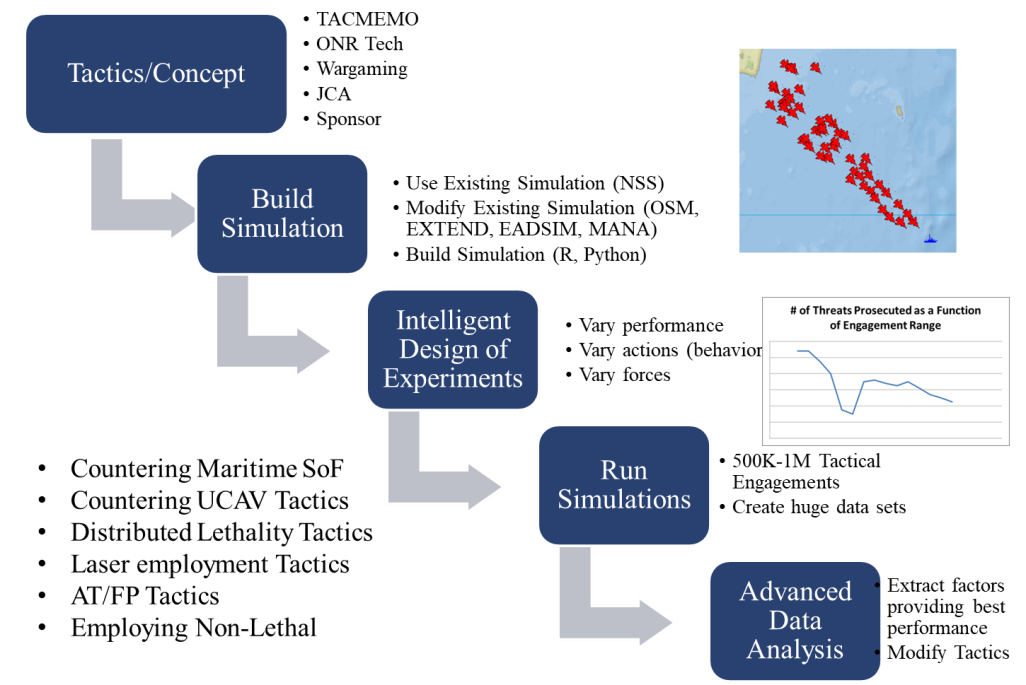
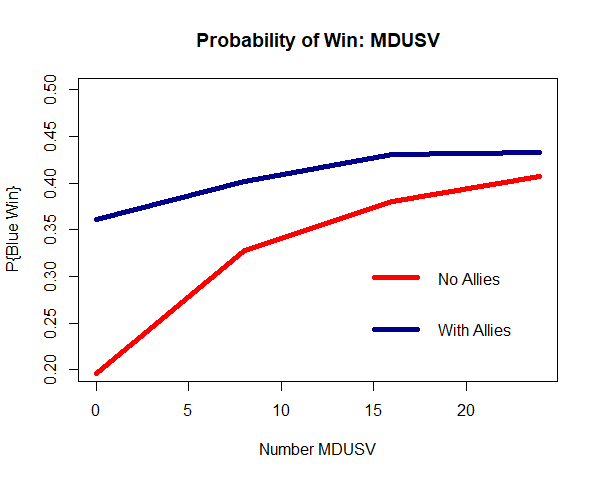
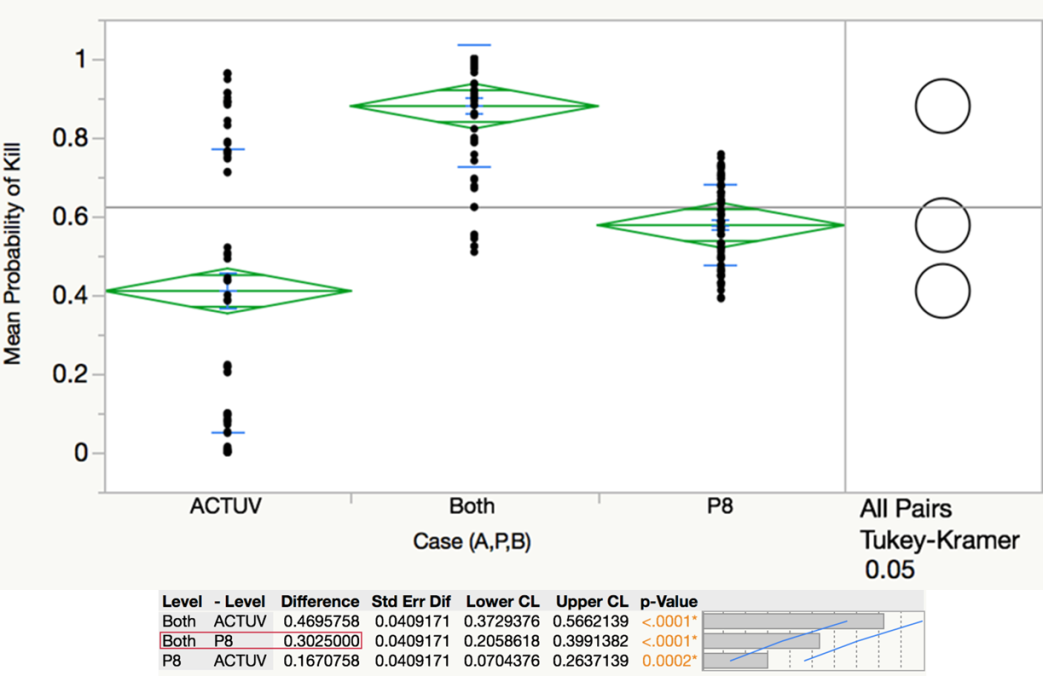
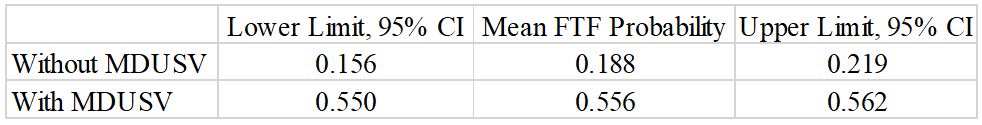
By VADM T.J. White, RDML Danelle Barrett, and LCDR Robert “Jake” Bebber
Imagine you are the Information Warfare Commander (IWC) of a coalition naval task force in the South China Sea in 2033. The task force’s mission is to deliver combat power in support of the Commander’s campaign objectives. As the IWC, you are simultaneously a “supporting” and “supported” commander. You execute multiple lines of operations across the full-spectrum of influence, information, and cyberspace. The other warfare commanders – strike, air defense, and sea combat – rely on you to understand their fight and fuel their decision-making with precision information, while simultaneously conducting an integrated high-end fight in and through the information domain leading to warfighting outcomes. The information domain is vast, it can be both localized and completely global, interweaving through all other domains of war.
Cyberspace and the Electromagnetic Spectrum are material realizations of the information domain, whether midpoint or endpoint, Internet Protocol or radio frequency, defense or attack, this is where you fight, for there is only one network separated in time. The arsenal of interoperable weapons and systems, manned and unmanned platforms, at the Commander’s disposal to execute and sustain a campaign requires all that you can bring to bear from across your composeable force to achieve unmatched distributed lethality. You have the authorities to execute full-spectrum information warfare to:
- Reach intended audiences and decision-makers to alter adversary courses of action to our advantage;
- Protect coalition decision-making;
- Seize and hold at risk adversary cyberspace;
- Defend our interests in and through cyberspace;
- Compete and Win.
Technological capabilities are advancing at an exponential rate while also converging with each other, creating new capabilities for both you and your adversary. When those are combined with people and processes, they provide significant operational advantages, enabling us to simultaneously contest adversary actions in cyberspace, land, sea, air, and space. Future warfighting, enabled by these emerging technologies, is necessary to adapt, develop, and execute new, more lethal operational methods. The future IWC must foster an intuitive ability in themselves and across their force to recognize these emergent opportunities, seize them with deliberate intent, and be comfortable with a battlespace changing at an unprecedented rate. As “maestro” of the Information Warfare afloat symphony, you understand the potential power of full-spectrum, integrated information warfare. You guide your force to realize that potential by opportunities seized and effects achieved.
This requires serious forethought and planning to make certain the force – human and platform – is prepared to orchestrate effects in this type of environment. It demands a certain mentality and type of thinker – agile, adaptive, innovative, willing to take calculated risks with speed; an aggressive change agent. Thinking like a futurist and being comfortable with being uncomfortable should be part of the IWC job description. As the IWC, you see the convergence of people, information, and machines as your domain and how the Navy makes that our warfighting gain.
The complex interactions within the information environment and ecosystem expose new vulnerabilities to pre-emptively close or seize. Space, cyberspace, and the electromagnetic spectrum must be protected from disruption by sophisticated and increasingly aggressive adversaries. These domains are contested ecosystems in which you as the IWC must align kinetic and non-kinetic fires, synchronized alongside other operations. At your disposal are surface, subsurface, air, and space autonomous vehicles that can reason, recommend actions, and execute within prescribed rules of engagement. Autonomous information warfare platforms are hyper-connected with manned units using both laser and radio frequency communications links, complicating an already congested spectrum. The ability to tie all these elements together into the fleet tactical grid, coupled with advanced data analytics and machine learning, are required to prevail in our highly contested battlespace.
Additionally, platforms are equipped with quantum computers networked across 24 time-zones. Secure cloud-networked afloat “information warfare vaults” at the tactical edge project combat power and provide the bandwidth, security, and resiliency needed to fight through information disruption and denial. Our peer adversaries have rapidly advanced their capabilities in parallel. Inexpensive and ubiquitous technology has eroded the qualitative operational advantages we once enjoyed. Our force must be postured to deny the information space to adversaries who wish to hold our national interests at risk. Resilience in your operations presents both sides of the coin; challenge and opportunity.
We observed a sea change in operational focus, due to the vastly different threat outlook outlined 17 years earlier in the 2018 National Defense Strategy (NDS). In 2033 we face new and emerging threats that were not imagined then. For example, miniaturized computing coupled with advanced robotics on autonomous Artificial Intelligence (AI) vehicles have fundamentally changed maritime warfare. The rules of engagement are different and include means for AI in those autonomous vehicles to even make ethical decisions about warfare. Our adversaries no longer conform to Geneva Convention rules having judged them anachronistic for the current fight. As IWC you have a keen sense of how these factors govern our own warfighting actions, how the adversaries don’t behave in accordance with traditionally accepted rules of warfare, and how to incorporate all of these factors for an information advantage that ensures our lethality.
Since 2000, the U.S. and China have been engaged in a fierce technological arms race, with AI at the forefront beginning 2018. Each amassed complicated autonomous combat platforms that can reason, recommend, and make decisions depending on their programming and their ability to learn. China made significant investments in people, processes, and technology (not always their own) to ensure dominance in AI and quantum computing. They have long held a strategic national objective to be the world leader in AI, working tirelessly to shape information interactions globally. What started in the early stages of Chinese and American research companies developing AI programming that defeated the world’s greatest chess and Go masters, has progressed to unprecedented computing capability far exceeding the capacity of the human brain.
Physical devices such as automobiles, appliances, phones, and homes were embedded with sensors, software, and actuators connected to share data and control actions across an “Internet of Things.” This similarly transformed maritime operations. Strategic competitors like Russia and China added disruptive tools to their information arsenal to achieve warfighting maritime effects like operational technology disruption in navigation, propulsion. and other control systems. As the IWC, you understand how to stay one step ahead of potential adversaries by leveraging those same technologies and capabilities, integrating them into the fight, and denying enemy use.
Your superior AI is a game changer enabling you to stay ahead. It correlates thousands of factors in real time yielding a tactical picture not disconnected from operational significance. Advanced modeling and simulation of possible enemy courses of action at the tactical edge provides you with recommended countermeasures. Real-time assessment of network conditions yields the means to communicate securely over vast distances to execute distributed operations. Because it processes vast quantities of data in fractions of a second, AI quickly learns, grows, and adapts within a rules framework such as command relationships, rules of engagement, campaign phasing, weight, level of effort, all covering multiple branches and sequels to operational plans. Your team provides the necessary “man in the loop” understanding and maintaining of Commander’s intent and strategic guidance. AI supports your maritime forces by providing courses of action based on analysis of massive amounts of sensor data and information from ashore and organic afloat sources. The key to this operator extended reality (clearer sight picture, farther reach, faster decision) is data veracity – a combination of data trustworthiness and core common data standards across and within the information kill chain. Warfighting decisions are made more quickly and reliably, even factoring ethical and moral elements into the calculus. Only in the most sensitive warfighting scenarios are humans used as the last deciding factor for weapons employment.
The Navy moved boldly to get here by 2033. The information race was not an easy lift. There were practical modernization, structural, and cultural challenges for the Navy to quickly integrate and adapt processes to leverage new technology on aging platforms, new ideas by old warriors, and to build the new platforms with the flexibility to insert emerging technology at a significantly accelerated rate. In 2018, the Navy’s acquisition and programmatic processes were slow, built for the industrial era. The Navy recognized this and changed. It forced creative solutions in how it imagined, researched, built, fielded, and sustained new technology. An example of this was their move to commercial cloud to more quickly deliver lethal technologies and advanced data analytics to the tactical edge of fleet operations. Continued reforms streamlined the traditional acquisition processes so that by 2033 new capabilities are continuously delivered in increments vice in their entirety over decades, ultimately yielding the agility we require for the fight.
More important than improved acquisition processes is flexibility in how our most important treasure – our people – are missioned. To protect platform networks and exploit information advantages in 2018, the Navy began deploying cyber development units, Sailors specially trained who came with their own “cyber kit,” able to build tools “on the fly” to meet emerging priorities. By 2033, training, education, and organic platform capability have resulted in full spectrum cyber and information operations from sea. As the IWC, you recognize processes and people are just as critical to excellence in the information domain as the technology. You deliberately combine these three elements for warfighting supremacy.
In 2033 you also have the authority to execute influence operations to shape the maritime and littoral battlespace. History from prior to 2018 demonstrated that peer adversaries like Russia and China quickly organized social media and public demonstrations around the world in support of their strategic objectives in the Ukraine, Southeast Asia, and America. In 2033, influence actions at the tactical and operational level are designed and executed by you and aligned to strategic objectives including targeted messaging on social media; suppressing, changing, or interfering with adversary maritime messaging to their audiences; or targeting dual-use entities that support adversary maritime sustainment.
So how is this all playing out operationally in the total fight in 2033? Back in the South China Sea, as IWC you are coordinating with our coalition partners as a task force quietly slips out of San Diego. Under the guise of a planned international naval exercise, this force would include a Japanese “helicopter-destroyer” with a mix of Japanese F-35s and older V-22s, as well as a French frigate. To keep the Chinese unaware, the carrier fleet remains in port. The command ship, a Zumwalt-class guided missile destroyer, and two of the newest unmanned guided missile frigates lead the force. An American cruise missile submarine, which departed two weeks prior from the U.S. mainland, avoids the extensive Chinese underwater sensor networks that stretch to Hawaii.
A key component to this lethal task force are those virtually undetectable unmanned surface and subsurface “sensor/shooter” vessels. These platforms use secure and resilient quantum-encrypted relays to massively powerful shipboard data clouds. This cloud ecosystem leverages advanced heuristics and machine-language algorithms correlating sensor production and dissemination of information in the context needed for action to humans and weapons systems. Task Force vessels spread across the Pacific, link land-and-space-based intelligence and surveillance collection and long-range ballistic missiles with Air Force B-52 “arsenal” planes loaded with hypersonic, anti-ship, and anti-air missiles. This powerful manned and unmanned naval force is part of a larger coalition response, sent as a bulwark between Vietnamese islands and the oncoming Chinese amphibious fleets. The Task Force Commander relies on you to execute denial and deception to confound the adversary and maintain tactical situational awareness (EMCON, counter-ISR and counter-targeting systems). You deftly impact adversary behavior through advanced influence operations executed against their maritime forces, partners, and logistics lines of communication. You and the converged human and machine team leverage the entire electromagnetic spectrum, from space to undersea and linked to assessment and intelligence nodes via tactical and operational level “cloud”-based quantum computing systems to proactively analyze, disseminate and act on information. Synchronized human-AI teams dynamically model, wargame, and execute pre-planned and improvised tactical actions and operational movements to prevent detection. Commander confidence is high in the human-augmented teams to quickly and accurately identify potential second and third order effects across an integrated battle space. You provide the Commander with the information warfare options needed to deter, and if necessary, defeat adversary forces. Your Commander has the highest levels of force readiness and uses technology to help maintain that state. The symbiotic relationship between machine and human extends down to the individual Sailor and platform as Sailor health and readiness are continuously monitored via implants and sensors, enabling your Commander to immediately recalibrate force distribution should you begin to take casualties.
Before a shot is fired, the Commander knows she will win the information war, enabling success in the overall campaign. You as the IWC will give her that tactical and operational win as the conductor orchestrating the elements together for mission success.
In a data-rich and knowledge-poor circumstance, challenged with sophisticated competitors, as IWC you will be more than just the conductor of this information orchestra; you will be the instrument builder and tuner, the composer, and the producer. You will rely on advanced technologies and computers to perform the heavy lifting so our forces can act dynamically with precision and purpose. Modern information warfare requires this nimble shift from orchestra to jazz, or to the raw power and disruption of punk rock.
If you are interested in joining, contact the iBoss.
Vice Adm. Timothy “T.J.” White currently serves as the Commander, U.S. Fleet Cyber Command and Commander, U.S. 10th Fleet at Fort Meade, MD. A leader in the Navy’s Information Warfare Community, White originally served as a surface warfare officer before being designated as a cryptologic warfare officer. He is a graduate of the U.S. Naval Academy and has postgraduate degrees from the Naval Postgraduate School and the National Defense University-Industrial College of the Armed Forces. He is also a Massachusetts Institute of Technology Seminar XXI fellow. He is a native of Spring, TX.
Rear Adm. Danelle Barrett is serving as the Navy Cyber Security Division Director on the staff of the Deputy Chief of Naval Operations for Information Warfare (N2N6) in the Pentagon. An Information Professional, she graduated from Boston University where she received her commission via the Naval Reserve Officers Training Corps program. She holds Masters of Arts degrees in Management, National Security/Strategic Studies, and Human Resources Development and a Master’s of Science in Information management. Barrett has published more than 29 professional articles.
Lieutenant Commander Robert “Jake” Bebber was commissioned through the Officer Candidate School program. An Information Warfare professional, Bebber holds a Ph.D. in Public Policy, a Master’s in Public Administration and a Master’s In National Security and Strategic Studies, as well as a BA in Political Science from Stetson University. He currently is assigned to the staff of Commander, Carrier Strike Group 12 on board USS Abraham Lincoln as the Cryptologic Resource Coordinator.
Featured Image: PHILIPPINE SEA (JUNE 21, 2016) Sonar Technician (Surface) 3rd Class Michael E. Dysthe stands watch in the combat information center during a anti-submarine warfare exercise aboard the Ticonderoga-class guided-missile cruiser USS Chancellorsville (CG 62). (U.S. Navy photo by Mass Communication Specialist 2nd Class Andrew Schneider/Released)