This article originally appeared in edition 2/2020 of the German-language publication SIRIUS: The Journal for Strategic Analyses and is republished with permission. SIRIUS is edited by the foundation Stiftung Wissenschaft und Demoktrie based in Kiel, Germany. The article will be available online in its original German in the May-June timeframe. You can follow SIRIUS on Twitter (@JE_SIRIUS) and Facebook. You can find the most recent issues of SIRIUS online here: https://www.degruyter.
By Captain Sascha H. Rackwitz, German Navy
Introduction
Whether we like it or not, we live in an era of a fundamental reorientation of the international system. It doesn’t matter if you follow the American paradigm of “Great Power Competition”1 or the Chinese2 and Russian3 interpretation of a “multipolar world order.” Global stability is being threatened by hegemonic tendencies of power. The perceptions of the United States, China, and Russia are principally the same, but are viewed from very different vantage points. After the bipolar confrontation of the Cold War and a short time of American unipolarity, the international system has entered a new phase that will be defined by the inter-relations of these three actors.
In public discussions in Germany, and even amongst German “defense professionals,” this understanding does not seem to have been established very well. Russian aggression against Ukraine, and particularly the annexation of Crimea in 2014, was a watershed moment in German security and defense politics. However, Russia’s confrontational politics toward the West is still seen as a specific transatlantic and isolated phenomenon that can be reduced to questions of defense and deterrence at the northeastern borders of the NATO alliance, the “Northflank.”
No one in Germany will deny that China is posing a strategic challenge. This, however, is perceived to have above all economical relevance for Germany. And it is mostly seen as something totally unrelated to security issues on this side of the globe and more as an intensifying bilateral American-Chinese tussle. Illegal Chinese claims in the South China Sea will be met with open critique by German officials and diplomatic demarches. But China’s behavior is predominantly perceived as an economic threat to the freedom of navigation the German trade-oriented economy is dependent upon.
However, a self-centered perspective will not answer the challenges Germany is facing. For Germany, unlike most other countries, strengthening a rules-based order and the international organizations and structures that support it is not only – in the “end, ways, means” understanding of strategy – a way to achieve national interests. Derived from its geographic location, painful history, and ethical conviction, it is an end in itself. To safeguard this interest, political decision-makers rely on a military-strategic analysis that takes in the intensifying global rivalry in its entirety. Otherwise, Germany – and with it Europe – will face the Melian’s fate that Thucydides described over 2000 years ago, “The strong do what they can and the weak suffer what they must.”4 The lines of conflict of this great power struggle run, with little to no exception, through the maritime domain, including the Indo-Pacific, the North Atlantic, and the Mediterranean Sea. It is therefore particularly important for maritime professionals to take an active part in this strategy discussion and provide a maritime perspective. The following theses are intended to contribute to this debate and attempt to sketch practical conclusions from maritime strategic analysis.
Thesis 1: Nuclear Weapons Continue to determine Military and Naval Strategy
Nuclear strategy issues have increasingly become a matter of and for specialists, far removed from the political sphere, and this seems even more dangerous in military strategic thinking.5 In Germany it is conventional wisdom that there is nothing to be won by discussing nuclear strategy, not for politicians, not for journalists, not even for political scientists. Even within the German armed forces, the discussion of the subject is often subsumed exclusively under Germany’s role in NATO’s nuclear sharing arrangements, as if military thinking is suspended with the threat of using nuclear weapons. However, nuclear weapons remain a necessary starting point for a strategic analysis. They set the framework for the use of conventional military means in a confrontation between the great powers and, not only for their own (maritime) strategic derivations. The roles prescribed for nuclear weapons by the United States, Russia, and China are all the more relevant since their declaratory policies differ substantially.
The Chinese no-first-use policy, usually a position repeatedly demanded by anti-nuclear activists and, for western nuclear weapon states as well, particularly by German anti-nuclear weapons activists, is no reason for consolation. In the context of escalating antagonism with the United States, it has a rather destabilizing effect, since the declared waiver of initial use or use against a non-nuclear weapon state feeds the illusion that a major military conflict can be limited. Read this way, the effect of the Chinese nuclear weapons policy is not to prevent any armed conflict through deterrence; to the contrary, it instead is making a conventional armed conflict more possible.
China presents the U.S. with a dilemma. On one hand, the onus of exceeding the nuclear threshold is assigned solely to the U.S., while at the same time the prospective costs for conventional intervention are increased to forbidding levels. As a consequence, China presents the United States with a stark choice: admit that your reassurances to allies and partners in the western Pacific are worthless; accept that you will suffer a prohibitively high price in blood and treasure trying to meet your obligations conventionally; or risk an all-out nuclear war as a nuclear aggressor. The South China Sea is the cordon sanitaire prerequisite for this narrative. Only by attaining indisputable influence over the East and South China Seas can China hope to create the strategic depth necessary to prevent the United States from defending its own possessions or allies in the Western Pacific. As a result, the Western Pacific is strategically isolated, the U.S. loses its escalation dominance, and military conflict becomes an option for China to resolve disputes in its near-abroad without fear of American interference.
Russia’s “de-escalating nuclear strike” strategy pursues the same purpose on the opposite tack.6 It is based on the assumption that even though Russian conventional forces cannot match NATO’s military potential, Russia can achieve a locally and timely limited conventional superiority sufficient to create a fait accompli. This superior position is then protected by threatening the use of small yield, short-range nuclear weapons. The first-use of nuclear weapons is, therefore, not excluded. On the contrary, the first use policy is openly announced and, as part of major Russian exercises, is also regularly emphasized to the West as the potential opponent. The purpose of threatening to use nuclear weapons in this limited fashion is to strategically separate the east of the alliance area, especially the Baltic States, from the rest of the alliance. A strategic dilemma is presented to the nuclear weapon states of the west, in particular the United States, of either giving in to Russian aggression and consequently allowing the collapse of the alliance or, conversely, to risk an uncontrollable nuclear escalation. The strategic value of the medium-range weapons stationed by Russia in violation of the INF Treaty is precisely that these weapons can reach Poland and possibly Germany, but not the Alliance’s nuclear weapon states. Whether Russia would consider such a nuclear strike only if defeat in a conventional war loomed or early on in a conflict to pre-empt a conventional NATO reaction is beside the point. The strategic isolation of the eastern alliance area by limited nuclear strikes is the basis to shield a war with “limited object”7 and thus to use military force below the threshold of a global nuclear war.
The fact that both China and Russia, while confronted with comparable problems, assign such different roles to their nuclear arsenal is also due to the fact that China acts confidently from a position of strength. Russia, on the other hand, from the assumption that it was only possible to gain conventional superiority vis-à-vis NATO locally, and for a short period of time, plays a weaker hand.
Both approaches share the aim to gain freedom of action in the near-abroad, to be able to use conventional military means to pursue limited purposes, if necessary, and to reduce the risk of an escalation to an unlimited nuclear war. The control of maritime areas is of central importance for both China and Russia in these respects.
Thesis 2: “Anti-Access/Area Denial” has little to do with “Sea Denial” and a lot to do with “Sea Control”8
Undisputed sea control, or maritime supremacy as the U.S. Navy would call it, in the South and East China Seas is what China needs to keep conventional American armed forces at a distance from mainland China, to gain the freedom of movement for its own forces to threaten American forces in the Pacific, and eventually the continental United States with escalation. As a result, the United States will face the dilemma of either accepting high losses, nuclear escalation, or moral defeat – and all this for what amounts to an American perspective as only “limited political aims” – the commitments made to partners in the Western Pacific. China’s illegal land reclamation in the South China Sea9 has less to do with access to marine resources, but much more to do with the development of the military infrastructure to push its own sensor and weapons range so far into the Pacific that it becomes impossible for American forces to touch Chinese positions without risk to its fleet. Having gained freedom of action in order to build a credible military position to assert its own interests in its immediate neighborhood, particularly against Taiwan, China could theoretically reign supreme in the Western Pacific. The only contingency would then be a “distant blockade,”10 which China could attempt to counter by increasing self-reliance or the careful establishment of a string of strategic positions in peacetime. Both are already core elements of current Chinese policy, namely “China 2049” and the “Belt and Road Initiative.”
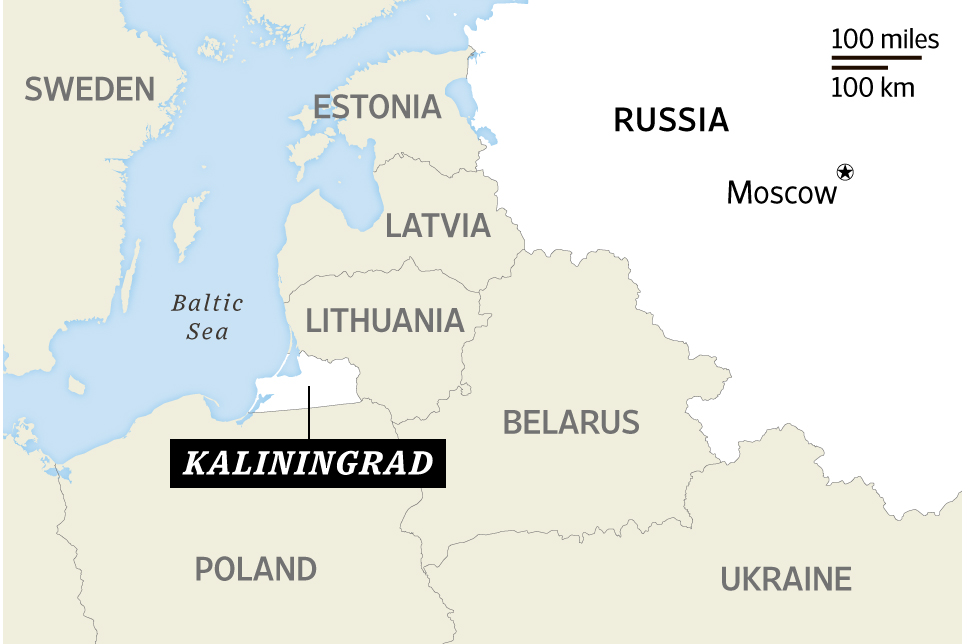
Compared to China, Russia has a similarly complex strategic position on its doorsteps. This position is aggravated by the fact that American partnerships in Europe are institutionalized in NATO. Particularly interesting is the situation in the Baltic Sea with respect to the Kaliningrad exclave. On one hand, Kaliningrad offers a strategic maritime position from which large parts of the eastern and central Baltic Sea can be affected. At the same time, Kaliningrad threatens the land lines of communication from Poland to the Baltic States through the so-called Suwalki Gap. However, Kaliningrad is dependent on supplies from the sea, and a possible Baltic area of operations is entirely within the range of regional allied naval forces. Moreover, maintaining superiority long enough for Russia to secure territorial gains depends on neutralizing the only two ways by which NATO could reinforce its members in the east in a timely fashion – by air or by sea.
In case of conflict, simply preventing western naval forces’ access to the central and eastern Baltic Sea would not meet Russian requirements. Russia must be able to positively control this sea area. In short, Russia must exercise sea control in order to obtain freedom of action to contribute to joint operations in the Baltic States, protect sea lines of communication to defend the Kaliningrad exclave, and cut off the Baltic States from their western allies. Even if the term “Anti-Access/Area Denial” (A2/AD) at first glance suggests otherwise, A2/AD is not just a question of denying the use of a maritime area. Rather, A2/AD is a concept for obtaining sea control in coastal and confined waters, which is primarily characterized by the use of land-based capabilities.
The U.S. Marine Corps has taken this understanding as their point of departure for the most fundamental realignment of the force since World War II. The Corps no longer sees its primary warfighting role in the Western Pacific as operating from the sea under the conditions of sea control won by the U.S. Navy. Rather, the Corps sees itself as an integral part of the naval force contributing to the fight for sea control with its specific capabilities, and thus to maintain escalation dominance.11 The Marine Corps no longer desires a dependence on Navy-won access for amphibious operations, but seeks to use its forward amphibious abilities to open access for the navy to project power. It is all about “contested sea control.”
Of course, all of these considerations are solely derived from the declaratory policies of China and Russia, a cursory analysis of the maritime areas in question, and the respective maritime military potentials fielded. Fortunately, it seems unlikely that Russia, for example, will raid one of the Baltic States as long as the Putin system remains stable. Indeed, the intensity of the actors’ motivation is a key factor in assessing the threat and, in turn, the required deterrent.12
The insinuated Russian stratagem is based on two assumptions. First, Russia gains conventional superiority for a short time. Second, and more importantly, that the motivation of western allies, and particularly the United States, does not suffice to risk a nuclear escalation in defense of their eastern allies. But Russian motivation to seek a systemic change in Europe by armed confrontation is perceived to be low, and justifies merely a “tripwire force” in Poland and the Baltic States – NATO’s Enhanced Forward Presence (eFP).13 Their multinational composition addresses the danger of a split of the alliance and the force creates a limited position of deterrence by denial.14 The small motivation of Russia is thus met by a small but sufficient tripwire, and is thus deterred. The message to Moscow is that invading the Baltic States would mean not only meeting with the Balts, but all major allies, and though NATO could be easily outnumbered, it would not be a walk in the park – so think twice.
What is the maritime dimension of this tripwire? Which specific opportunities does the maritime domain offer to strengthen and enhance the credibility of NATO’s deterrent position?
Thesis 3: Our most pressing operational problem in the Baltic Sea is not maintaining the sea lines of communication to Baltic States for reinforcing and supplying NATO forces
Following Russian aggression against Ukraine in 2014, NATO and Germany refocused on the ability to conduct a symmetrical war in Europe. By regaining and strengthening NATO’s ability to wage a symmetrical war on Europe’s eastern border, the conventional complement to nuclear deterrence is strengthened. For the German Army, this means above all returning to maneuver warfare and combined arms operations, strengthening armored units, and empowering them to quickly deploy heavy formations to the alliance’s eastern border. For the Navy, this means maintaining the sea lines of communication between the east coast of the United States to ports in Germany, Poland, and the Baltic States.
Of course, conflict between NATO and Russia would not happen out of thin air. There would most probably be times of heightening tensions and grey zone or hybrid activities. Arguably, Russia has for some time tested NATO’s preparedness and resolve, not only in the cyber domain,15 but also by incursions into the Baltic States.16 However, should tensions escalate to a level that would call for a decision of the North Atlantic Council to move larger formations from North America to Europe, deterrence would have already failed. Arguably, in such a situation, Russia would have stopped perceiving the price for taking on NATO in the east as still too high compared with the possible gains. To put it bluntly, if we are compelled to organize convoy operations across the Atlantic and through the Baltic Sea, NATO has already failed with its most important task – to send a message to Russia that the potential costs of aggression are always greater than the prospects of success.
A deterrence posture that basically rests on a tripwire activating over-the-horizon forces is opening a gap to an opposing strategy that is based on quick results and strategic isolation of the theatre of operations. Naval forces, however, in the Baltic Sea could provide an additional deterrent element that counteracts the Russian stratagem at a stage before a distant deployment of NATO formations to the Baltic States becomes necessary and must be protected on its journey. The double exclaves of Kaliningrad and the Baltic States provide the key to do just this. Understandably, due to the exposed location of the Baltic States, western observers perceive the theatre geometry in the Baltic Sea first and foremost as a vulnerability. However, Kaliningrad is even more exposed, lacking even the narrow and hard-to-defend land corridor that the Suwalki Gap is providing between Poland and Lithuania. The Russian position in the Baltic Sea is nowhere near as advantageous as the skillful Russian propaganda makes us believe. Kaliningrad’s geographical position is more tenuous given several considerations. Kaliningrad is essential for the enforcement of Russian sea control in the middle to eastern Baltic Sea and all of Kaliningrad is within weapon range from the sea. Access to Baltysk can easily be blocked, and sea lines of communication from Kaliningrad through the Gulf of Finland to St. Petersburg can easily be disrupted.
While the “Tripwire Forces” of the Enhanced Forward Presence represent an element of “Deterrence by Denial,” the maritime domain offers the possibility of adding an element of “Deterrence by Punishment” without the risk of escalation. As an aggressor, Russia would also have to lose something immediately before the NATO machinery starts up properly, adding a critical psychological effect.17 In the Baltic Sea, the role of naval forces is not merely the defensive protection of sea lines of communication to the Baltic States. In Corbett’s18 terms, already in peacetime and in order to contribute to a balanced deterrent posture and prevent a “limited war,” the role of naval forces in the Baltic Sea can be the “tactical offensive” as part of an overall “defensive strategy.”19 Like the Enhanced Forward Presence, this deterrence posture does not necessarily require great numbers of maritime forces. Those deployed, however, must be able to question the Russian claim to sea control and the sanctuary of the Kaliningrad exclave through land-attack and anti-ship-cruise missiles launched from small surface combatants, corvettes, submarines, and aircraft, as well as through mine-laying capabilities. Not all these forces have to be provided by one nation alone. In parallel to the Enhanced Forward Presence, multi-nationality would be an essential factor in preventing the strategic isolation of the eastern flank. And this is the second major advantage of the maritime domain – only at sea can Sweden and Finland be included in a credible deterrent posture without upsetting the complex balance of power by a motion for formal integration into NATO.
Conclusion
Russian appetite for serious mischief-making in the north is, thankfully, considered to be low. But it should prompt us to widen our peripheral vision – to the Mediterranean, the near east, the Indian Ocean, and the Pacific, where we do in fact see a lot more maritime activity. Maritime forces deployed to the Mediterranean or the Indian Ocean in constabulary force missions might actually be just as close to the mission set of “deterrence and defense” as those forces up in the north. Parallels and deviations in the approaches of Russia and China point to the fact that in a struggle involving nuclear-armed great powers there are no easily defined geographic limitations – and in fact, it is in our better interest as the Melians in the room not to allow any power to willfully separate strategic spaces. After all, we have to realize that the autocratic players in “Great Power Competition” try to widen and exploit geographic and political fault lines in the west. Let us not widen them intellectually ourselves.
Captain Sascha H. Rackwitz joined the German Navy in 1991. A submariner by background, he was captain of a submarine and commanding officer of the German Navy’s submarine squadron. After tours in the Ministry of Defence and the Ministry of Foreign Affairs, he until recently taught naval strategy and operational art at the German Armed Forces Command and Staff College before assuming his current responsibilities as deputy commander and chief of staff of Flotilla 1 of the German Navy, home to the German Navy’s corvettes, submarines, mine countermeasure forces, special operations, and naval infantry forces. The views expressed here are presented in a personal capacity. and do not necessarily reflect the views of any government or agency.
References
1. United States of America (2017): National Security Strategy of the United States of America.
2. Peoples Republic of China, State Council Information Office (2019): China’s Defence in the New Era.
3. Russian Federation (2015): National Security Strategy.
4. Thucydides, History of the Peleponnesian War, Chapter XVII, Melian Dialogue.
5. Gray, Colin S. (2018): Theory of Strategy, Oxford: Oxford University Press, p. 121f.
6. Gray, Colin S. (2018): Theory of Strategy, Oxford: Oxford University Press, p. 98.
7. Clausewitz, Carl (1832): On War, Berlin, Book VIII, Chapter V.
8. “Sea Control” is more of a process than a condition in which by constant effort freedom of action in a maritime area is obtained. Sea Control is regularly understood to be a prerequisite for protecting sea lines of communication and projecting power from the sea. „Sea Denial” on the other hand is the denial of the unhindered operational use of a maritime area to an opponent. Both sea control and sea denial have to be fought for, are therefore principally only applicable in times of conflict. They will only be achieved temporarily and locally to a certain extent depending on the effort invested – uncontested sea control is only theoretically possible.
9. Permanent Court of Arbitration, Philippines vs. China, 2016.
10. Corbett, Julian (1911): Some Principles of Maritime Strategy, London, p. 97.
11. United States Marine Corps (2019): Commandant’s Planning Guidance.
12. Morgan, Patrick (1983): Deterrence: A Conceptual Analysis, Beverly Hills: Sage Publications, p. 164f.
13. NATO Factsheet on eFP, https://www.nato.int/nato_static_fl2014/assets/pdf/pdf_2019_04/20190402_1904-factsheet_efp_en.pdf
14. Mazarr, Michael J./Chan, Arthur et al. (2018): What Deters and Why. Exploring Requirements for Effective Deterrence of Interstate Aggression, Santa Monica: RAND, p. 17ff.
15. Estonian Foreign Intelligence Service (2019) International Security and Estonia.
16. Republic of Estonia, Ministry of the Interior, Press about the kidnapping of an Estonian Internal Security Service officer, last updated 28 September 2015: https://www.siseministeerium.ee/en/eston-kohver
17. Snyder, Glen (1961): Deterrence and Defense: Toward a Theory of National Security. Westport: Greenwood Press.
18. Sir Julian Corbett, 1854-1922, British naval historian and strategic theorist is considered to be one of the most influential theorists of naval power next to the American Alfred Thayer Mahan.
19. Corbett, Julian (1911): Some Principles of Maritime Strategy, London, p. 73.
Featured Image: Russian Navy Baltic Fleet ships on parade. (ITAR-TASS/ Elena Nagornykh)




