This has been adapted from a blog post that first appeared on Strat.Buzz and was pulled from our friends at ASPI’s The Strategist.
In the last two weeks, there have been a number of articles circulating (including here, here, here and here) that Indonesia has formally recognised a territorial dispute with China in the South China Sea.
This discussion has originated from statements (see here, and here for example) attributed to Indonesian Navy Commodore Fahru Zaini, an assistant to the first deputy of the Coordinating Minister for Political, Legal, and Security Affairs (Menkopolhukam):
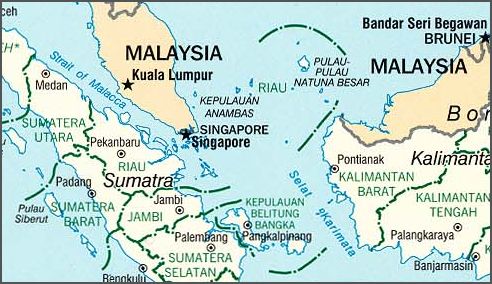
China has claimed Natuna waters as their territorial waters. This arbitrary claim is related to the dispute over Spratly and Paracel Islands between China and the Philippines. This dispute will have a large impact on the security of Natuna waters.
Commodore Zaini is also quoted as saying ‘…we have come to Natuna to see firsthand the strategic position of the TNI, especially in its ability, strength and its deployment of troops, just in case anything should happen in this region’.
 This might give the overall impression that Indonesia’s defence modernisation and deployment plans are driven by China’s recent assertiveness in the South China Sea, and that now Jakarta has officially staked out its policy to challenge Beijing.
This might give the overall impression that Indonesia’s defence modernisation and deployment plans are driven by China’s recent assertiveness in the South China Sea, and that now Jakarta has officially staked out its policy to challenge Beijing.
This impression is false for several reasons.
First, officially, there’s no maritime ‘dispute’ between Indonesia and China. Following the statement by Commodore Zaini, Indonesian foreign ministry spokesman Michael Tene said that ‘Indonesia has no maritime border with China’ and that Indonesia isn’t a claimant state to the South China Sea dispute. Indeed, Foreign Minister Marty Natalegawa clarified further on March 19,
We have to be absolutely clear about this…There are three seemingly related but separate issues. Firstly, there is no territorial dispute between Indonesia and China, especially about the Natunas. In fact, we are cooperating with China in possibly bringing about foreign direct investment plans in the Natunas. Second, we are not a claimant state in the South China Sea. Third, on the nine-dash line, it is true that we do not accept that. This is why we have asked for a formal explanation from China regarding their claims’ legal basis and background.
This policy is of course not new. Jakarta lodged a complaint with the UN in 2010 regarding the nine-dash line. In fact, Indonesia has consistently argued for the importance of the Natunas and how it should handle the South China Sea since the mid-1990s. I’ve described Jakarta’s key interests in the Natunas elsewhere.
Daniel Novotny’s book also has a long list of quotations from various Indonesian policymakers since the 1990s that basically echoed Commodore Zaini’s sentiments: Indonesia is concerned that the Natunas and its EEZs could be endangered by China’s nine-dash line, but it will never officially admit a dispute with China because that would give credence to Beijing’s claims. Former Foreign Minister Ali Alatas perhaps said it best, ‘the repetition of an untruth will eventually make it appear as truth’.
We can debate the merits of this position, but ultimately, there’s no significant policy shift on the matter. I would add a caveat however that the status quo between China and Indonesia over the Natunas might remain until the day Beijing publicly challenges Indonesia’s rights to explore the natural resources within the Natunas and its EEZs.
Second, on the military build-up, the Natunas area has been a central feature in Indonesia’s external defence thinking since the 1990s. The largest ever tri-service military exercise under Suharto’s tenure in 1996 was based on a scenario in the Natuna islands. This has been the pattern for subsequent exercises since; though there’s an additional ‘Ambalat component’ to it recently.
The statements that the TNI leadership has been making lately about ‘flashpoint defense’ and how its latest military assets would be deployed in the Natunas should be taken with a grain of salt.
For one thing, the ‘flashpoint defense’ (and the role of the Natunas in it) and the military modernisation plans have been on the books since the mid-2000s and publicly described in 2010.
For another, the procurement of advanced platforms like the Sukhois and Leopard MBTs and others is part of the Minimum Essential Force (MEF) concept that has been around since mid-2000s. The MEF was designed less for a China threat and more for an organisational and technological revamp and to meet existing operational requirements. The urgency becomes salient when we consider that the TNI lost numerous men due to accidents and platform decay in the past decade.
Indonesia isn’t building up its military power against a resurgent China, but the current political climate does provide the TNI leadership with the opportunity to further push for their pre-existing plans and to deflect criticisms from civil society activists arguing against expensive weaponry.
Finally, we can speculate whether Commodore Zaini was speaking for the Indonesian government. The clarification from the Foreign Ministry, however, suggests he wasn’t. Does this mean Commodore Zaini was speaking for the TNI? One of my contacts close with the defence establishment in Jakarta suggests that wasn’t the case either. There haven’t been any significant changes or plans made regarding the Natunas and the South China Sea at TNI headquarters.
We should also consider the fact that the Coordinating Ministry for Political, Legal, and Security Affairs isn’t a decision making body like the Ministry of Defense. They coordinate policies, they don’t formally make them.
Why Commodore Zaini made the arguments isn’t clear. What is clear, I think, is: (1) he wasn’t authoritatively tasked with announcing a major policy shift (nor is there actually a policy shift), and (2) he was merely echoing long-held Indonesian policy sentiments.
For these reasons, I think the articles that have suggested an official policy change from Indonesia on the Natuna Islands and South China Sea may have taken things out of their proper context.
Evan A. Laksmana is currently a Fulbright Presidential PhD Scholar in political science with the Maxwell School of Citizenship and Public Affairs at Syracuse University. He is also a researcher with the Centre for Strategic and International Studies in Jakarta. Image courtesy of Wikipedia.