By Tim McGeehan
Most Navy bridge watchstanders have had the experience of adjusting their surface-search radar to eliminate sea clutter or rain. In relation to the task of detecting surface ships, these artifacts represent “noise,” just as when one tunes out unwanted transmissions or static to improve radio communications.
However, information can be gleaned indirectly from unintentionally received signals such as these to yield details about the operating environment, and it may reveal the presence, capabilities, and even intent of an adversary. This “electromagnetic bycatch” is a potential gold mine for the Navy’s information warfare community (IWC) in its drive to achieve battlespace awareness, and represents a largely untapped source of competitive advantage in the Navy’s execution of electromagnetic maneuver warfare (EMW).
Electromagnetic Bycatch
The term electromagnetic bycatch describes signals that Navy sensors receive unintentionally. These signals are not the intended target of the sensors and usually are disregarded as noise. This is analogous to the bycatch of the commercial fishing industry, defined as “fish which are harvested in a fishery, but which are not sold or kept for personal use, and includes economic discards [edible but not commercially viable for the local market] and regulatory discards [prohibited to keep based on species, sex, or size].”1
The amount of fisheries bycatch is significant, with annual global estimates reaching twenty million tons.2 Navy sensor systems also receive a significant volume of bycatch, as evidenced by efforts to drive down false-alarm rates, operator training to recognize and discard artifacts on system displays, and the extensive use of processing algorithms to filter and clean sensor data and extract the desired signal. Noise in the sensor’s internal components may necessitate some of this processing, but many algorithms aim to remove artifacts from outside the sensor (i.e., the sensor is detecting some sort of phenomenon in addition to the targeted one).
U.S. and international efforts are underway to reduce fishing bycatch by using more-selective fishing gear and methods.3 Likewise, there are efforts to reduce electromagnetic bycatch, with modifications to Navy sensors and processing algorithms via new installations, patches, and upgrades. However, it is unlikely that either form of bycatch ever will be eliminated completely. Recognition of this within the fishing industry has given rise to innovative efforts such as Alaska’s “bycatch to food banks” program that allows fishermen to donate their bycatch to feed the hungry instead of discarding it at sea.4 This begs the question: Can the Navy repurpose its electromagnetic bycatch too?
The answer is yes. Navy leaders have called for innovative ideas to help meet twenty-first century challenges, and do to so in a constrained fiscal environment. At the Sea-Air-Space Symposium in 2015, Admiral Jonathan W. Greenert, then-Chief of Naval Operations, called for the Navy to reuse and repurpose what it already has on hand.5 Past materiel examples include converting ballistic-missile submarines to guided-missile submarines; converting Alaska-class tankers to expeditionary transfer docks (ESDs), then to expeditionary mobile bases (ESBs); and, more recently, repurposing the SM-6 missile from an anti-air to an anti-surface and anti-ballistic missile role.6 However, the Navy needs to go even further, extending this mindset from the materiel world to the realm of raw sensor data to repurpose electromagnetic bycatch.
Over The River and To The Moon
The potential value of bycatch that U.S. fisheries alone discard exceeds one billion dollars annually (for context, the annual U.S. fisheries catch is valued at about five billion dollars).7 Likewise, the Navy previously has found high-value signals in its electromagnetic bycatch.
In 1922, Albert Taylor and Leo Young, two engineers working at the Naval Aircraft Radio Laboratory in Washington, DC, were exploring the use of high-frequency waves as new communication channels for the Navy. They deployed their equipment on the two sides of the Potomac River and observed the communication signals between them. Soon the signals began to fade in and out slowly. The engineers realized that the source of the interference was ships moving past on the river.8 Taylor forwarded a letter to the Bureau of Engineering that described a proposed application of this discovery:
If it is possible to detect, with stations one half mile apart, the passage of a wooden vessel, it is believed that with suitable parabolic reflectors at transmitter and receiver, using a concentrated instead of a diffused beam, the passage of vessels, particularly of steel vessels (warships) could be noted at much greater distances. Possibly an arrangement could be worked out whereby destroyers located on a line a number of miles apart could be immediately aware of the passage of an enemy vessel between any two destroyers in the line, irrespective of fog, darkness or smoke screen. It is impossible to say whether this idea is a practical one at the present stage of the work, but it seems worthy of investigation.9
However, this appeal fell on deaf ears; the idea was not considered worthy of additional study. Later, in 1930, after it was demonstrated that aircraft also could be detected, the newly formed Naval Research Laboratory (NRL) moved forward and developed the early pulsed radio detection systems whose successors are still in use today.10 What started as degradations in radio communication signals (owing to objects blocking the propagation path) evolved to being the signal of interest itself. Today that bycatch is used extensively for revealing the presence of adversaries, navigating safely, and enforcing the speed limit. It is known as RAdio Detection And Ranging, or simply by its acronym: RADAR.
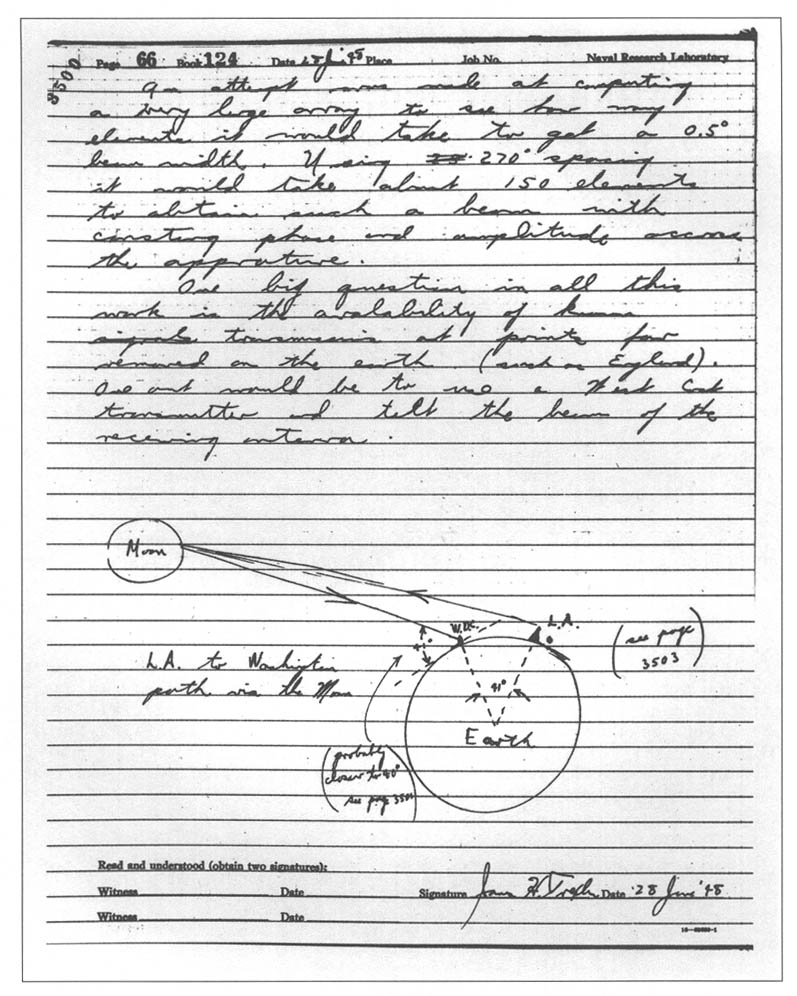
During World War II, Navy radar and radio receivers became increasingly sensitive and began picking up stray signals from around the world. Instead of discarding these signals, the Navy set out to collect them. The NRL Radio Division had been investigating this phenomenon since the mid-1920s, and in 1945 NRL established a Countermeasures Branch, which had an interest in gathering random signals arriving via these “anomalous propagation” paths.11 By 1947, it had erected antennas at its Washington, DC, field site to intercept anomalous signals from Europe and the Soviet Union.12 Just the year before, the Army Signal Corps had detected radio waves bounced off the moon. The convergence of these events set the stage for one of the most innovative operations of the Cold War.
NRL engineer James Trexler, a member of the Countermeasures Branch, advocated exploiting the moon-bounce phenomenon for electronic intelligence (ELINT). He outlined his idea in a 1948 notebook entry:
From the RCM [Radio Counter Measures] point of view this system hold[s] promise as a communication and radar intercept device for signals that cannot be studied at close range where normal propagation is possible. It might be well to point out that many radars are very close to the theoretical possibility of contacting the Moon (the MEW [actually BMEWS, for Ballistic Missile Early Warning System] for example) and hence the practicability of building a system capable of intercepting these systems by reflections from the Moon is not beyond the realm of possibility.13
Trexler’s idea addressed a particular intelligence gap, namely the parameters of air- and missile-defense radars located deep within the Soviet border. With an understanding of these parameters, the capabilities of the systems could be inferred. This was information of strategic importance. As friendly ground and airborne collection systems could not achieve the required proximity to intercept these particular radar signals, the moon-bounce method provided a way ahead. All that was required was for both the Soviet radar and the distant collection site to have the moon in view at the same time. What followed were NRL’s Passive Moon Relay experiments (known as PAMOR) and ultimately the Intelligence Community’s Moon Bounce ELINT program, which enjoyed long success at collecting intelligence on multiple Soviet systems.14
Around this time, the Navy grew concerned about ionospheric disturbances that affected long-range communications.15 So the service employed the new moon-bounce propagation path to yield another Navy capability, the communications moon relay. This enabled reliable communications between Washington, DC, and Hawaii, and later the capability to communicate to ships at sea.16 Thus, what started as bycatch led to a search for the sources of stray signals, revealed adversary air- and missile-defense capabilities, and ultimately led to new communications capabilities for the Navy.
Extracting the Electromagnetic Terrain
Signals in the electromagnetic spectrum do not propagate in straight lines. Rather, they refract or bend on the basis of their frequency and variations in the atmospheric properties of humidity, temperature, and pressure. Signals can encounter conditions that direct them upward into space, bend them downward over the horizon, or trap them in ducts that act as wave guides. Knowing this electromagnetic terrain is critical to success in EMW, and can prove instrumental in countering adversary anti-access/area-denial capabilities.
Variation in electromagnetic propagation paths can lead to shortened or extended radar and communications ranges. Depending on the mission and the situation, this can be an advantage or a vulnerability. Shortened ranges may lead to holes or blind spots in radar coverage. This information could drive a decision for an alternate laydown of forces to mitigate these blind spots. It also could aid spectrum management, allowing multiple users of the same frequency to operate in closer proximity without affecting one another. Alternatively, extended radar ranges can allow one to “see” farther, pushing out the range at which one can detect, classify, and identify contacts. Signals of interest could be collected from more distant emitters. However, the adversary also can take advantage of extended ranges and detect friendly forces at a greater distance via radar, or passively collect friendly emissions. Identifying this situation could prompt one to sector, reduce power, or secure the emitter.
As the weather constantly changes, so too does signal propagation and the resultant benefit or vulnerability. Understanding these effects is critical to making informed decisions on managing emitters and balancing sensor coverage against the signature presented to the adversary. However, all these applications rely on sufficient meteorological data, which typically is sparse in space and time. More frequent and more distributed atmospheric sampling would give the U.S. Navy more-complete awareness of changing conditions and increase its competitive advantage.
Luckily, Navy radar sensors already collect a meteorological bycatch. Normally it is filtered out as noise, but emerging systems can extract it. The Hazardous Weather Detection and Display Capability (HWDDC) is a system that takes a passive tap from the output of the SPS-48 air-search radar (located on most big-deck amphibious ships and carriers) and repurposes it like a Doppler weather radar.17 Besides providing real-time weather information to support operations and flight safety, it can stream data to the Fleet Numerical Meteorology and Oceanography Center in Monterey, California, to feed atmospheric models. With this data, the models can generate better weather forecasts and drive electromagnetic propagation models for prediction of radar and communications-system performance.18 The Tactical Environmental Processor (TEP) will perform the same function by extracting atmospheric data from the SPY-1 radar.19
By passively using the existing radar feeds, HWDDC and TEP provide new capabilities while avoiding additional requirements for power, space, frequency deconfliction, and overall system integration that would be associated with adding a new radar, antenna, or weather sensor. There also is the potential to extract refractivity data from the radar returns of sea clutter.20 The multitude of radar platforms in the Navy’s inventory represents an untapped opportunity to conduct “through the sensor” environmental data collection in support of battlespace awareness.
Likewise, the Global Positioning System (GPS) also collects meteorological bycatch. As GPS signals pass through the atmosphere, they are affected by the presence of water vapor, leading to errors in positioning. The receiver or processing software makes corrections, modeling the water vapor effect to compensate, thereby obtaining accurate receiver positions. However, water vapor is a key meteorological variable. If the receiver location is already known, the error can be analyzed to extract information about the water vapor, and by using multiple receivers, its three-dimensional distribution can be reconstructed.21 Instead of dumping the bycatch of water vapor, it can be (and is) assimilated into numerical weather prediction models for improved short-range (three-, six-, and twelve-hour) precipitation forecasts.22
Do Not Adjust Your Set
There is also great potential to harvest bycatch from routine broadcast signals. While a traditional radar system emits its own pulse of energy that bounces back to indicate the presence of an object, passive systems take advantage of signals already present in the environment, such as television and radio broadcasts or even signals from cell towers or GPS.23 These signals propagate, encounter objects, and reflect off. This leads to the “multipath effect,” in which a transmitted signal bounces off different objects, then arrives at the same receiver at slightly different times owing to the varied distances traveled. (This is what used to cause the “ghost” effect on television, in which an old image seemed to remain on screen momentarily even as the new image was displayed.) Variations in this effect can be used to infer the presence or movement of an object that was reflecting the signals.
In a related concept, “multistatic” systems collect these reflections with multiple, geographically separated receivers, then process the signals to detect, locate, and track these objects in real time.24 These systems have proved effective. In a 2002 demonstration, Lockheed Martin’s Silent Sentry system tracked all the air traffic over Washington, DC, using only FM radio and television signal echoes.25 More recently, another passive system went beyond simple tracking and actually classified a contact as a small, single-propeller aircraft by using ambient FM radio signals to determine its propeller rotation rate.26 This level of detail, combined with maneuvering behavior, operating profiles, and deviations from associated pattern-of-life trends, could even give clues to adversary intent.
Passive radar systems have many advantages. They emit no energy of their own, which increases their survivability because they do not reveal friendly platform location and are not susceptible to anti-radiation weapons. They do not add to a crowded spectrum, nor do they need to be deconflicted from other systems because of electromagnetic interference. The receivers can be mounted on multiple fixed or mobile platforms. Technological advances in processing and computing power have taken much of the guesswork out of using passive systems by automating correlation and identification. Moving forward, there is great potential to leverage radar-like passive detection systems.
That being said, operators of the passive radar systems described may require extensive training to achieve proficiency. Even though the systems are algorithm- and processing-intensive, they may require a significant level of operator interaction to select the best signals to use and to reconfigure the network of receivers continually, particularly in a dynamic combat environment when various broadcasts begin to go offline. Likewise, the acquisition, distribution, placement, and management of the many receivers for multistatic systems (and their associated communications links) is a fundamental departure from the traditional employment of radar, and will require new concepts of operations and doctrine for employment and optimization. These efforts could be informed by ongoing work or lessons learned from the surface warfare community’s “distributed lethality” concept, which also involves managing dispersed platforms and capabilities.27
Challenges and Opportunities
Among the services, the Navy in particular has the potential to gain much from harvesting the electromagnetic bycatch. During war or peace, the Navy operates forward around the world, providing it unique access to many remote locations that are particularly sparse on data. Use of ships provides significant dwell time on station without requiring basing rights. Navy platforms tend to be sensor intensive, and so provide the means for extensive data collection. This extends from automated, routine meteorological observations that feed near-term forecasts and long-term environmental databases to preconflict intelligence-gathering applications that include mapping out indigenous signals for passive systems to use later.28 The mobility of Navy platforms allows for multiple units to be brought to bear, scaling up the effect to create increased capacity when necessary.
However, there are many challenges to overcome. The Navy soon may find itself “swimming in sensors and drowning in data”; managing this information will require careful consideration.29 Returning to the fishing analogy, to avoid wasting bycatch fishermen need to identify what they have caught in their nets, find someone who can use it, temporarily store it, transport it back to port, and get it to the customer before it spoils. Likewise, the Navy needs to dig into the sensor data and figure out exactly what extra information it has gathered, identify possible applications, determine how to store it, transfer it to customers, and exploit it while it is still actionable.
This hinges most on the identification of electromagnetic bycatch in the first place. As automation increases, sensor feeds should be monitored continuously for anomalies. Besides serving to notify operators when feeds are running outside normal parameters, such anomalous data streams should be archived and analyzed periodically by the scientists and engineers of the relevant systems command (SYSCOM) to determine the presence, nature, and identity of unexpected signals. Once a signal is identified, the SYSCOM team would need to cast a wide net to determine whether the signal has a possible application, with priority given to satisfying existing information needs, intelligence requirements, and science and technology objectives.30
History has shown that this is a nontrivial task; remember that the original discovery and proposed application of radar were dismissed. If the unplanned signal is determined to have no current use, it should be noted for possible future exploitation. Subsequent sensor upgrades, algorithm improvements, and software patches then should strive to eliminate the signal from future incidental collection. If there is potential value in the incidental signal, upgrades, algorithms, and patches should optimize its continued reception along with the original signal via the same sensor, or possibly even demonstrate a requirement for a new sensor optimized for the new signal. The identified uses for the electromagnetic bycatch will drive the follow-on considerations of what and how much data to store for later exploitation and what data needs to be offloaded immediately within the limited bandwidth owing to its value or time sensitivity.
The analogy to fisheries bycatch also raises a regulatory aspect. Much as a fisherman may find that he has caught a prohibited catch (possibly even an endangered species) that he cannot retain, the same holds true for electromagnetic bycatch. It is possible that an incidental signal might reveal information about U.S. citizens or entities. Once the signal is identified, intelligence oversight (IO) requirements would drive subsequent actions. Navy IO programs regulate all Navy intelligence activities, operations, and programs, ensuring that they function in compliance with applicable U.S. laws, directives, and policies.31 IO requirements likely would force the SYSCOM to alter the sensor’s mode of operation or develop upgrades, algorithms, and patches to avoid future collection of the signal.
The Role of the Information Warfare Community
The Navy’s IWC is ideally suited to play a key role in responding to these challenges. Its personnel have experience across the diverse disciplines of intelligence, cryptology, electronic warfare, meteorology and oceanography (METOC), communications, and space operations, and assembling these different viewpoints might reveal instances in which one group can use another’s bycatch for a completely different application. IWC officers now come together to make connections and exchange expertise in formal settings such as the Information Warfare Basic Course and the Information Warfare Officer Milestone and Department Head Course. Further cross-pollination is increasing owing to the cross-detailing of officers among commands of different designators. Recent reorganization of carrier strike group staffs under the Information Warfare Commander construct has increased and institutionalized collaboration in operational settings. Restructuring has trickled down even to the platform level, where, for example, the METOC division has been realigned under the Intelligence Department across the carrier force. As a net result of these changes, the IWC has a unique opportunity to have new eyes looking at the flows of sensor data, providing warfighter perspectives in addition to the SYSCOM sensor review described above.
The Navy also can capitalize on the collective IWC’s extensive experience and expertise with issues pertaining to data collection, processing, transport, bandwidth management, archiving, and exploitation. Furthermore, the different components of the IWC share a SYSCOM (the Space and Naval Warfare Systems Command, or SPAWAR); a resource sponsor (OPNAV N2/N6); a type commander (Navy Information Forces); a warfighting-development center (the Navy Information Warfighting Development Center); and a training group (the Navy Information Warfare Training Group will be established by the end of 2017). This positions the IWC to collaborate across the doctrine, organization, training, materiel, leadership and education, personnel, and facilities (DOTMLPF) spectrum. This will support shared ideas and unified approaches regarding the employment of emerging capabilities such as the machine-learning and “big-data” analytics that will sift through future electromagnetic bycatch. Ultimately, the members of the IWC can forge a unified way forward to develop the next generation of sensors, data assimilators, and processors.
Conclusion
While the Navy might not recognize exactly what it has, its sensors are collecting significant amounts of electromagnetic bycatch. The Navy’s forward presence positions it to collect volumes of unique data with untold potential. The associated electromagnetic bycatch is being used now, previously has yielded game-changing capabilities, and could do so again with future applications. Instead of stripping and discarding it during data processing, the Navy needs to take an objective look at what it can salvage and repurpose to gain competitive advantage. The fishing bycatch dumped every year could feed millions of people; the Navy needs to use its electromagnetic bycatch to feed new capabilities. Don’t dump it!
Tim McGeehan is a U.S. Navy Officer currently serving in Washington.
The ideas presented are those of the author alone and do not reflect the views of the Department of the Navy or Department of Defense.
[1] Magnuson-Stevens Fishery Conservation and Management Act of 1976, 16 U.S.C. § 1802 (2) (1976), available at www.law.cornell.edu/.
[2] United Nations, International Guidelines on Bycatch Management and Reduction of Discards (Rome: Food and Agriculture Organization, 2011), p. 2, available at www.fao.org/.
[3] Ibid., p. 13; Lee R. Benaka et al., eds., U.S. National Bycatch Report First Edition Update 1 (Silver Spring, MD: NOAA National Marine Fisheries Service, December 2013), available at www.st.nmfs.noaa.gov/.
[4] Laine Welch, “Gulf Bycatch Will Help Feed the Hungry,” Alaska Dispatch News, June 4, 2011, www.adn.com/; Laine Welch, “Bycatch to Food Banks Outgrows Its Beginnings,” Alaska Fish Radio, August 3, 2016, www.alaskafishradio.com/.
[5] Sydney J. Freedberg Jr., “Tablets & Tomahawks: Navy, Marines Scramble to Innovate,” Breaking Defense, April 13, 2015, breakingdefense.com/.
[6] Sam Lagrone, “SECDEF Carter Confirms Navy Developing Supersonic Anti-Ship Missile for Cruisers, Destroyers,” USNI News, February 4, 2016, news.usni.org/; Missile Defense Agency, “MDA Conducts SM-6 MRBM Intercept Test,” news release, December 14, 2016, www.mda.mil/.
[7] Amanda Keledjian et al., “Wasted Cash: The Price of Waste in the U.S. Fishing Industry,” Oceana (2014), p. 1, available at oceana.org/.
[8] David Kite Allison, New Eye for the Navy: The Origin of Radar at the Naval Research Laboratory, NRL Report 8466 (Washington, DC: Naval Research Laboratory, 1981), p. 39, available at www.dtic.mil/.
[9] Ibid, p. 40.
[10] “Development of the Radar Principle,” U.S. Naval Research Laboratory, n.d., www.nrl.navy.mil/.
[11] David K. van Keuren, “Moon in Their Eyes: Moon Communication Relay at the Naval Research Laboratory, 1951–1962,” in Beyond the Ionosphere, ed. Andrew J. Butrica (Washington, DC: NASA History Office, 1995), available at history.nasa.gov/.
[12] Ibid.
[13] Ibid.
[14] Frank Eliot, “Moon Bounce ELINT,” Central Intelligence Agency, July 2, 1996, www.cia.gov/.
[15] Van Keuren, “Moon in Their Eyes.”
[16] Pennsylvania State Univ., From the Sea to the Stars: A Chronicle of the U.S. Navy’s Space and Space-Related Activities, 1944–2009 (State College, PA: Applied Research Laboratory, 2010), available at edocs.nps.edu/; Van Keuren, “Moon in Their Eyes.”
[17] SPAWAR Systems Center Pacific, “Hazardous Weather Detection & Display Capability (HWDDC),” news release, n.d., www.public.navy.mil/; Timothy Maese et al., “Hazardous Weather Detection and Display Capability for US Navy Ships” (paper presented at the 87th annual meeting of the American Meteorological Society, San Antonio, TX, January 16, 2007), available at ams.confex.com/.
[18] Tim Maese and Randy Case, “Extracting Weather Data from a Hybrid PAR” (presentation, Second National Symposium on Multifunction Phased Array Radar, Norman, OK, November 18, 2009), available at bcisensors.com/.
[19] Hank Owen, “Tactical Environmental Processor At-Sea Demonstration,” DTIC, 1998, www.handle.dtic.mil/.
[20] Ted Rogers, “Refractivity-from-Clutter,” DTIC, 2012, www.dtic.mil/.
[21] Richard B. Langley, “Innovation: Better Weather Prediction Using GPS,” GPS World, July 1, 2010, gpsworld.com/.
[22] Steven Businger, “Applications of GPS in Meteorology” (presentation, CGSIC Regional Meeting, Honolulu, HI, June 23–24, 2009), available at www.gps.gov/; Tracy Lorraine Smith et al., “Short-Range Forecast Impact from Assimilation of GPS-IPW Observations into the Rapid Update Cycle,” Monthly Weather Review 135 (August 2007), available at journals.ametsoc.org/; Hans-Stefan Bauer et al., “Operational Assimilation of GPS Slant Path Delay Measurements into the MM5 4DVAR System,” Tellus A 63 (2011), available at onlinelibrary.wiley.com/.
[23] Lockheed Martin Corp., “Lockheed Martin Announces ‘Silent Sentry(TM)’ Surveillance System; Passive System Uses TV-Radio Signals to Detect, Track Airborne Objects,” PR Newswire, October 12, 1998, www.prnewswire.com/; Otis Port, “Super-Radar, Done Dirt Cheap,” Bloomberg, October 20, 2003, www.bloomberg.com/.
[24] Lockheed Martin Corp., “Silent Sentry: Innovative Technology for Passive, Persistent Surveillance,” news release, 2005, available at www.mobileradar.org/.
[25] Port, “Super-Radar, Done Dirt Cheap.”
[26] F. D. V. Maasdorp et al., “Simulation and Measurement of Propeller Modulation Using FM Broadcast Band Commensal Radar,” Electronics Letters 49, no. 23 (November 2013), pp. 1481–82, available at ieeexplore.ieee.org/.
[27] Thomas Rowden [Vice Adm., USN], Peter Gumataotao [Rear Adm., USN], and Peter Fanta [Rear Adm., USN], “Distributed Lethality,” U.S. Naval Institute Proceedings 141/1/1,343 (January 2015), available at www.usni.org/.
[28] “Automated Shipboard Weather Observation System,” Office of Naval Research, n.d., www.onr.navy.mil/.
[29] Stew Magnuson, “Military ‘Swimming in Sensors and Drowning in Data,’” National Defense, January 2010; www.nationaldefensemagazine.org/.
[30] U.S. Navy Dept., Naval Science and Technology Strategy: Innovations for the Future Force (Arlington, VA: Office of Naval Research, 2015), available at www.navy.mil/.
[31] “Intelligence Oversight Division,” Department of the Navy, Office of Inspector General, n.d., www.secnav.navy.mil/.
Featured Image: ARABIAN GULF (March 4, 2016) Electronics Technician 3rd Class Jordan Issler conducts maintenance on a radar aboard aircraft carrier USS Harry S. Truman (CVN 75). (U.S. Navy photo by Mass Communication Specialist 3rd Class Justin R. Pacheco/Released)







