
From the Korean peninsula came news on Thursday that construction on a divisive Republic of Korean (ROK) naval base could proceed on Jeju Island. According to Stars and Stripes:
The South’s Supreme Court ruled Thursday that the controversial construction of a naval base on Jeju Island, south of the Korean peninsula, is lawful and may continue.
When finished in 2015, the base will be able to accommodate as many as 20 navy ships and submarines, not to mention the occasional cruise ship.
The island’s southern coast village of Gangejeong is an attractive location for a naval base. It will more easily allow the Republic of Korean Navy (ROKN) to project forces south to protect the shipping lanes on which the nation relies, and respond to ongoing territorial and natural resource disputes with China over a nearby contested reef. Further, it will provide an appealing stopover for the visiting American naval vessels that regularly call at ports on the peninsula.
The island, once home to the ancient Kingdom of Tamna, also bears echoes of Okinawa. The people of Jeju consider themselves a separate people from mainland Koreans as Okinawans do of mainland Japanese. Many too fear shouldering a disproportionate share of the military burden, impacts to the island’s environment, and getting caught in the middle of clashing American and Chinese forces. Such qualms have led to boisterous protests and the just-resolved court case.
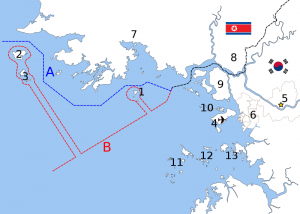
2–Baengnyeong Island
A-Northern Limit Line
B-DPRK-claimed border
Meanwhile to the north, the ROK announced last week the construction of a much smaller new facility in the region just south of the contested maritime border with North Korea. This facility will be built on the island of Baengnyeong, one of five islands west of the peninsula in the area (though further north) that saw the sinking of the ROKN warship Cheonan and the shelling of the island of Yeonpyang:
One official with the South Korea Ministry of National Defense said the Baengnyeong facility will enable “a more stable management over the Northern Limit Line” that divides the two Koreas in the Yellow Sea.
The Baengnyeong Island facility reportedly will have accommodations for up to 100 troops and a dock for small warships by the time it is completed in 2014. Ministry of National Defense officials took issue Thursday with those calling it a “naval base.”
“To the public, it might be seen as a base,” one said. “But, it’s more of a mooring facility,” with accommodations for a military company.
Asked if the ministry fears making Baengnyeong Island a potential target for a North Korean attack, another ministry official said, “We have no fear putting it there at all. We’re just building a dock to improve our soldiers’ living conditions.”
Whether North Korea follows through with a sabre-rattling response to Baeongnyeong facility remains to be seen, but the DPRK has reportedly completed a base for troop-carrying hovercraft 31 miles north of Baengnyeong at Koampo.






