OK, Explain Again Just Why the American Taxpayer Should Pay For All This
This article, the sixth of the series, presents reasons why Congress and the American taxpayer should pay for all the drones, buoys, railguns and the additional necessary ships to deploy them at sea introduced earlier in the series. Some of the justifications briefly discussed below are sure to be familiar to the reader, some less so. In either event, please feel free to mentally rearrange them according to your own priorities. Read Part One, Part Two, Part Three, Part Four, Part Five.
Expensive Assets
These are not inexpensive assets that can be squeezed into the Navy’s spending plans somehow. With a likely cost of $3 billion plus for the CVLN and CARN classes, less the cost of at least one, possibly two DDGs that a CARN replaces in a carrier task force and $2 billion plus cost for an AORH, Congress and the American taxpayer are going to have to be persuaded to purchase these as additional assets for the Navy. So why should they do so?
Deterrence
Adding large quantities of ISR and ASW drones along with a dozen, or more, railguns as a matter of routine will provide a credible defense against the increasing A2AD threat the Navy faces. Presenting a potential adversary with overwhelming force in a potential area of conflict is a time proven technique for preventing conflict and promoting dialogue. It should also be noted that while these additional assets are expensive, combined they are still less than half the construction cost of just the CVN being protected, much less the air wing embarked aboard.
Protection
For CVNs
Much of the surface warfare assets the Navy possesses are routinely dedicated to protecting other critical ship classes and their embarked sailors. The CVNs operating in their dedicated task forces normally find themselves free to go where they please given the protection against air, submarine and surface threats the surrounding ships provide. Adding a CVLN and a CARN to this operating procedure is simply adding to a proven recipe by countering the increasingly formidable A2AD assets other nations are steadily acquiring.
For amphibious assaults
The Marine Corp routinely catches a ride on an ARG provided by the Navy. Most of the time there is no need to provide the extra protection provided by the suggested new ship classes. Come the big moment though, both during the few days leading up to and then during an amphibious assault placing a CARN, an AORH and a Zumwalt class destroyer between the opposing forces ashore and the ARG can very substantially improve the chances of success and measurably lower the anticipated casualty rates amongst the Marines making the landing. By providing substantial ASW assets in the coastal waters involved, numerous ISR and target spotting assets from the AORH, formidable fire support abilities from the CARN and Zumwalt and substantial anti-missile, rocket or artillery shell protection courtesy of the twelve railguns the new ship classes will significantly improve the Navy’s ability to support an amphibious invasion. Plus the Marines making the ride ashore will be able to start from just over the horizon thanks to the presence of multiple targeting drones and railguns instead of the much discussed fifty mile seasick inducing slog currently anticipated.
Ally reassurance
Protecting the carrier strike groups also means reassuring our allies that we will be able to fulfill the defense commitments we have made, particularly in the Western Pacific. However, building and deploying the means to allow the fleet to go where it wants is a globally useful capability, allowing the U.S. to confidently assert it will be there in time of need.
Multi-polar world
We live in a multi-polar geopolitical structure. China, Russia, India, Europe, the Gulf States, Brazil and others already are jostling with the U.S. for influence and trade. Including a China who already is in some respects, and will remain our economic equal in world affairs. This economic equivalence is something the U.S. has not had to deal with since our enormous industrial expansion in the last three decades of the 19th Century. We need to refresh our thinking with some of the concepts that worked well for us as we dealt with Great Britain, the existing economic power back then.
That said being a rival is not the same as being an enemy. There certainly are many areas where the U.S. and China will find ways to cooperate to our mutual benefit. We are certain to jostle each other though, especially in China’s immediate area as that proud civilization looks to ‘put things right’ after their many difficulties of the last two centuries. As mentioned above, we want to deter everyone in the area from using violence to bring about change, instead encouraging patience while the various nations involved discover mutually acceptable adjustments via discussion.
Playing defense to maintain the world as it is
There are other issues that come with being in a multi-polar world. In the new global circumstances the U.S., and the Navy in particular, need to execute defense, and first things first, keep our ships afloat. Something we have not had to overly concern ourselves with since the demise of the Soviet Union or the destruction of the Imperial Japanese Navy in the 1940s. Increasingly we will no longer be able to exercise the freedom of the seas and engage in whatever activity we want, whenever we want to. Russia is already building a submarine and long-range bomber force to potentially contest our passage. Others, China in particular, will be able to invest steadily increasing resources in military assets that make sense for their geo-political situation. Investments that mean the U.S Navy may have to fight our way across the North Pacific or North Atlantic before we commence operations at the location of our choice.
Hawaii has to eat
Our geography as a nation includes Hawaii, control of which easily translates into the control of the bulk of the Pacific Ocean. Yet Hawaii is a series of islands, thousands of miles from the mainland with a population of 1.4 million. Again, the change to a multi-polar world means we have to give thought to just how we can ensure the population on the islands can eat when trouble arrives. Russia already has the submarine assets needed to threaten mining or torpedoing ships crossing the North Pacific. Obviously the naval assets based at Pearl Harbor and the West Coast should be able to prevent that. However, we can no longer just take it for granted. The Navy needs to consciously add this to its long list of missions to accomplish.
The same issues apply to Guam, though the much smaller population can be fed by air if necessary, which means the mission is more one of being able to get our needed fuel and ammunition supplies delivered. Once more, the local air and naval forces should be able to ensure it happens. This is an area where the rise in China’s capabilities means we cannot take free passage for granted there either.
Maritime Commons
Protecting the global commons to ensure free passage of American trade was one of the primary reasons the U.S navy was originally built in the 18th Century. The need, a global need in the 21st Century, continues unabated.
Blockade
Occasionally over the years the U.S. has chosen to impose a blockade during a dispute. This is a capability, or more importantly for our relationship with China, a potential capability that we need to maintain. And the world needs to be reminded of on occasion.
Protection
As many others have noted over the last few years, a British citizen in the 19th Century could travel the world secure in the realization that the local government, regardless of whether it got along well with London or not, was not going to antagonize Britain by harming, or allowing to be harmed, the traveling Brit. A benefit that transferred to American citizens as a result of our overwhelming victory in 1945.
Unfortunately, in growing numbers of places in the world this benefit no longer exists due to the inability of many local governments to provide law and order within their borders for anyone, much less wandering Americans. This means that the U.S. Navy and Marine Corp have to face the reality that just as in the ‘olden days’ of the 18th and 19th Centuries, they are on call to provide basic protection to Americans all across the globe.
Rescue
The need for the Navy and Marine Corp to provide rescue service as needed has never gone away. And given the monotonous regularity of severe weather events, civil disturbances and the endless list of troubles that arise, this is certainly not going to change.
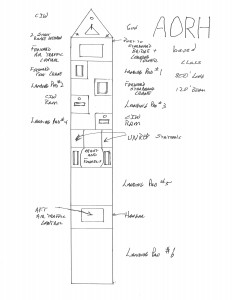
AORH uses
The AORH class suggested earlier in this series of articles was quite consciously designed to be capable of taking on some of the responsibilities, new and old, mentioned above. First among these was to be flagship capable, coupled with the resupply abilities and the substantial ASW and special forces capabilities built into the design.
These abilities are capable of being useful undertaking missions beyond the obvious applications in the Gulf, South China Sea and Northeast Asia. In addition, an ice-strengthened version of an AORH is very well suited to leading a small task force of frigates on ASW duty in the Arctic. It can also be used as the centerpiece for an old-fashioned hunter killer group prosecuting submarines or to provide transoceanic convoy protection in either the North Pacific or North Atlantic.
Current Political Impasse
As for the likelihood of persuading the current Congress to pay for this the Navy needs to be frank. The additional spending being asked for here are additional dollars for additional capabilities. Beyond some small incremental steps, most of the needed dollars will not fit inside the spending limits in place over the next few years. It is intended as a long term plan, to be funded as a recovering economy allows, with the big ticket items being built starting in the 202os and extending into the late 2030s.
For the economy is slowly growing and just as importantly the deficit is in notable decline. There are multiple reasons for this and there is good reason to believe they will continue to positively impact the deficit. A growing economy, the impact fracking is having on energy production, the beginning of the return of some manufacturing to North America from China due to higher wages there, the fact that Medicare costs are much less onerous than forecast five years ago, Obamacare is not costing nearly as much as feared when it was passed, and ending the Bush-era tax cuts are having a real impact on the actual deficit as well as on the, far larger, feared one.
So the enormous fear factor that was driving the deficit reduction hawks back in 2010/11 is in the process of dissipating, being replaced with some truly old-fashioned value driven politics. It is important to note that the Republic has been down this road before. After both the Revolutionary War and the Civil War Congress chose to slowly bring down an enormous deficit by running small annual surpluses. In essence, some variation of this strategy, regardless of how fiercely you espouse the ‘value’ part of balanced budgets, is what we are going to have to do as we deal with the left over Cold War debt and the enormous additional debt load piled on post 9/11 and due to the Great Recession.
Die Hard Yankee Frugality
Or depending on one’s viewpoint, good old-fashioned small town frugality, skinflints, True Blue small town values defending America from corrupt Big City mentalities, etc. The reader should feel free at this point to insert the variation(s) he hears most often where he lives. This cultural attribute came to the New World with the Pilgrims and remains a vigorous part of American culture. It has not, and will not be, departing from our political discussions. Or budgeting decisions.
So, how should we address those who hold this belief? In my experience, when trying to influence or alter decisions made by those operating from this position, argument and persuasion can work. If. Actually two ifs. Big ones. First a resolution to the revenue versus budget issue forcing hard choices has to be visible to the individual you are working with. And it is they that have to see it; regardless of how obvious it is to you, they are the ones that have to see, understand and agree. Then you need a plan dealing with anticipated results and consequences that you can clearly articulate, including how you will execute the plan, deal with the known potential problems and be convincing about being able to complete the task on time and most importantly, within the agreed upon budget.
Mid-America Teary-Eyed Balanced Budget Goodness
Across much of interior America another strong cultural value, the Intrinsic Goodness of Balancing Your Budget also accompanied some of the earliest English settlers of North America. Over the centuries this value has also been passed on to succeeding generations over family dinner tables, political discussions at the local diner or at the town’s barbershop. The at times teary-eyed value some of it’s current believers place in it can be almost moving to observe by someone who considers it merely another number. Plus, minus or zero each have meaning, yet no particular cultural Goodness.
To the True Believers amongst us it constitutes one of life’s bedrock values though. And it is not departing the American political scene either. Which means it will strongly impact budgeting issues far into the future as well.
However, unlike those professing Yankee Frugality, True Believers are virtually impervious to discussion and argument. Sometimes they will patiently listen to you and your points, still no matter how cogent and persuasive one might be, True Believers, once they start their decision making process, will cycle back and check your argument against various values and beliefs they hold. And if they find your argument in conflict with one of their values, for the purposes of this article, the Intrinsic Goodness of Balancing Your Budget, your suggested plan will be rejected.
Any additional information you might provide tends to ultimately provoke something along the line of this real life quote. “You are just trying to confuse me with facts,” responded one individual a few years ago. Global warming was the topic that day rather than the budget and the end result was, “I have my faith (in the rightness of their belief – not really a conclusion, a belief) and I will not change my position.”
This attribute is very much in play when discussing the current budget situation. Unfortunately it is, in my experience anyway, impervious to analysis and discussion. All those carefully honed arguments and points of persuasion potentially useful when speaking with those convinced of the value of frugality will only be considered by True Believers after the budget is balanced. Maybe.
Their faith in the correctness of the uttermost value of balanced budgets can be trumped by another value however. Not by many though, as it ranks high in their pantheon. Historically of course the value to use was the need for defense. Whether national defense from other nations, personal defense against crime or terrorism or preserving orderly and lawful procedures when discussing social issues, over the decades this has proven an effective approach.
Unfortunately the current spending debate has been embroiled in the revolt of a significant number of voters, primarily though not entirely, conservative Republicans, over the blatant abuse of this trump value during the second Bush administration. Vice President Cheney was incorrect when he claimed there were no electoral consequences to running vast deficits. There are, both economic and political, a truth that is not going away.
A significant portion of their political base could, and did for a while, accept the national defense against terrorism argument after 9/11. However subsequent failures to control Federal spending, under a Republican President, Senate and House no less infuriated them. Fury then became something close to horror after the Salomon Brothers debacle unleashed a need for massive federal deficits to restore the economy.
So after years of serious abuse of the national defense trump value, its use with those who fervently believe in the Intrinsic Goodness of Balancing Your Budget has been heavily invalidated. For a significant portion of the American electorate the call for a return to this basic value remains a hot button issue. It is five years on from the revolt that took place in 2010 and the fury and horror seem to have been replaced with a grim resolve to never allow spending to run out of control again. And balance the budget.
This implies, barring a serious political change in the House in a future election year, we may well have to wait for the sanctified day when the Federal government takes in more revenue than it spends before any substantive increases in spending, or allocations for substantial new abilities for the U.S. Navy can be expected.
In all likelihood this means it will not be until sometime in the 2020s before much of what has been suggested in terms of shipbuilding, i.e. the new AORH, CVLN and CARN class ships and large quantities of the associated drones and buoys, can obtain the political support needed for the substantial sums needed.
Count Our Blessings
It is always useful to Count Your Blessings though. The bulk of the resistance in Congress is to additional spending, with no more than the usual amount of Congressional meddling in the details of departmental, including DOD, spending. Just figure out a way to get things done within the dollar amount allotted is a frequently expressed desire by many in the House.
Nor is there any value based or carefully analyzed opposition to new equipment programs from any of the services. So while the suggested ship classes and drones will provoke a fierce defense of spending limits, there is no reason to anticipate Congressional opposition to the new equipment if the Navy develops a coherent plan including them. As suggested above in all probability the big items will not be affordable until sometime in the 2020s, nonetheless if the items are part of a long term acquisition plan it will merely be a question of waiting for funds to become available rather than overcoming fierce opposition to the plans and equipment.
So have a long-term plan in place
This means the U.S. Navy needs to have that forward looking plan in hand, constantly being updated as various improvements in doctrine, sensors and drones are developed. And be ready when additional funds become available, rice bowl pointed upwards as the saying goes. Whether the motivation to Congress is a perceived problem somewhere across the globe, the occasional Congressional compromise over something or other that includes extra funds for some department, a call for ‘shovel ready’ projects when recessions hit, or the slippery processes of logrolling; having a plan in place will allow the extra funds to be applied far more beneficially to the Navy’s, and the countries, benefit than a haphazard purchase of a few more of this and that.
Honor the Premise
In the end though, funding for the U.S. Navy, and all other Federal government departments, is only going to grow as fast as the economy. Which will happen, meaning any plan including the suggestions made in this series of articles will have to be implemented over a period of many years. Into the late 2030s or mid-2040s before the last of nine ship CARN build for instance. The early 2030s for eleven AORHs and the same for a six ship CVLN build are also reasonable build out expectations at this point.
Clearly the time to start to work on such a plan is now.
Jan Musil is a Vietnam era Navy veteran, disenchanted ex-corporate middle manager and long time entrepreneur currently working as an author of science fiction novels. He is also a long-standing student of navies in general, post-1930 ship construction thinking, design hopes versus actual results and fleet composition debates of the twentieth century.