The following is a two-part series on the role cruisers played in the Soviet and Russian Navy. The first part examines historical inspiration for developing a cruiser-focused force, concepts of employment, and strategic rationale. Part II will focus on how cruisers shaped the environment through forward presence during the Cold War, and how the nature of presence may evolve into the future.
By Alexander Clarke
“A Man-of-War is the best ambassador.”
This is an often quoted phrase of Britain’s 17th Century Lord Protector Oliver Cromwell;1 a phrase stated in an age when seapower had shown promise of potential,2 but not yet attained the capabilities, or achieved the feats, that would truly make it demonstratively so.3 This words were said before the ministry of William Pitt (the Younger, Prime Minister 1783-1801 & 1804-6),4 before the works of Alfred Thayer Mahan5 and Julian Stafford Corbett6 were published, and before the age of Empire and Gunboat Diplomacy.7 Yet still, in just eight simple words, it sums up the root construct of all this history and thought that have, does, and will continue to shape the world and relations between states to this day. It does this because it succinctly sums up a principle function, and duty, of warships in ‘peacetime.’ A function, which is entirely entwined with navies’ roles of maintaining maritime security8 – enabling freedom of trade, as well as access to the bounty of the sea, and presence,9 the protection of interests, reassurance of allies, and deterrence of potential aggressors.
Maritime Security and Presence are big missions for navies, they are the roles of ‘peacetime’ which make ‘peace’ such a relative term for navies in comparison to armies.10 A situation accelerated by the fact that in ‘peacetime’ the rules of engagement become by necessity stricter, the constabulary duties (fishery protection, counter piracy, counter smuggling, etc.) get greater focus, and engagements with other nations, both friend or potential foe, become more nuanced and subjective. This though is nothing new, and despite the recent phraseological development of the ‘Oceanic Global Commons,’11 patrolling the world’s original super highway – the sea,12 has been the subject of discussion and debate probably since humans first set to sea. The best lesson that has been drawn from these discussions, is that there is always more to be learned.
So with the discussion started, it is necessary to explain the question, why focus on the Soviet, and successor Russian navy? That is explained by the fact that while the Soviets and the Russians have never achieved dominant status at sea, they have successfully managed to enhance their status, maximize their presence, and achieve a growing level of influence through leveraging the capability they had/have in ways that have limited other nations ability to interfere with their interests. This success has not been achieved by accident, instead it is a product of long running analysis;13 analysis which has diverged at a significant point from the traditional Anglo-American Western naval model14 – not through a different understanding of warfighting, but a different perspective on operations outside of warfighting.
As students of history the Soviets had seen how a land power, Germany, had not really gained anything, but lost a lot strategically by building a fleet which was shaped directly to challenge the largest sea power prior to WWI15 – conversely the same nation had got far closer to success with a more asymmetric approach both in that war and WWII. The prime example of this is a weapon of sea denial, the submarine.
Unfortunately, the experience of both WWI and WWII showed that submarines alone were not enough in war time; furthermore, it showed they are only really useful in wartime. In ‘peacetime’ they are good for intelligence gathering, Special Forces operations, and practicing for war. Submarines are so limited in conducting presence operations because they are by their very nature stealth units, and the visibility required for presence goes against this fundamental attribute. Furthermore, due to the physical and technological sensitivity of their hull coats and sonic signatures, even port visits to the closest of allies are fraught with potential risks that are more sensibly avoided. The use of submarines in the presence mission, therefore usually comes at the point of it becoming focused towards ‘conventional’ deterrence16 – rather than just overt presence.
This is where surface combatants come in, and it explains the evolving Russian approach with a growing focus on designs which were far more general purpose than specialists despite their often stated role of Anti-Submarine Warfare.17 No area is this seen more clearly than in the consistent focus on cruisers, and the ‘cruising mission.’18 Understanding the difference is something which will begin to matter more, not only because of the resurgent Russia, but the growth of other navies, for example China and India. These nations have not merely acquired equipment, they also draw heavily from the Russian (and by extension, Soviet) naval experience and practice in conceptualizing naval operations.
How and why the Soviets used the Cruiser…
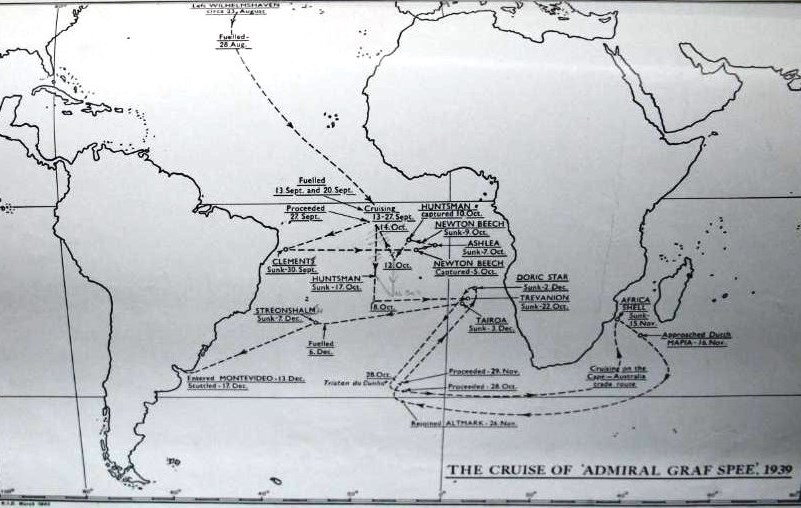
The post-WWII Sverdlov class19 was where the Soviet navy started to bring their vision of cruiser capability to fruition. Pre-war plans had been very conventional and these post-war plans were heavily influenced by their understanding of WWII German naval surface raider operations.20 These operations had tied down large amounts of Royal Navy (RN) combatants, and had been very successful. For example the cruise of the ‘Pocket’ Battleship, the Admiral Graf Spee, whilst ending heroically (for both sides21) at the Battle of the River Plate,22 had sunk nine merchant ships, captured two ships, and ‘frightened’ at least one other. Although these are the easily measurable effects, there is no real way of quantifying how many Captains changed or altered their course, how many loads were late or connections missed, all as a result of the fear of where the German raider was – or just as strong, the fear of where it might be.
In any case, the effects were not limited to the merchant marine. According to the Soviet Historian L.M. Eremeev23 in his work Some Results of the Cruiser Operations of the German Fleet, the RN mobilized numerous forces to catch the Admiral Graf Spee, including Commodore Harwood’s South Atlantic Squadron, seven cruisers, two aircraft carriers, a battlecruiser, and at least three destroyers (although considering the escorts required by the capital ships mobilized, he was likely underestimating this number by a long way). This demonstrated to the Soviet Union the potential of surface ships, if used in a ‘cruiser warfare’ manner, to exert great impact upon operations disproportionate to the realistic capabilities of the vessel.
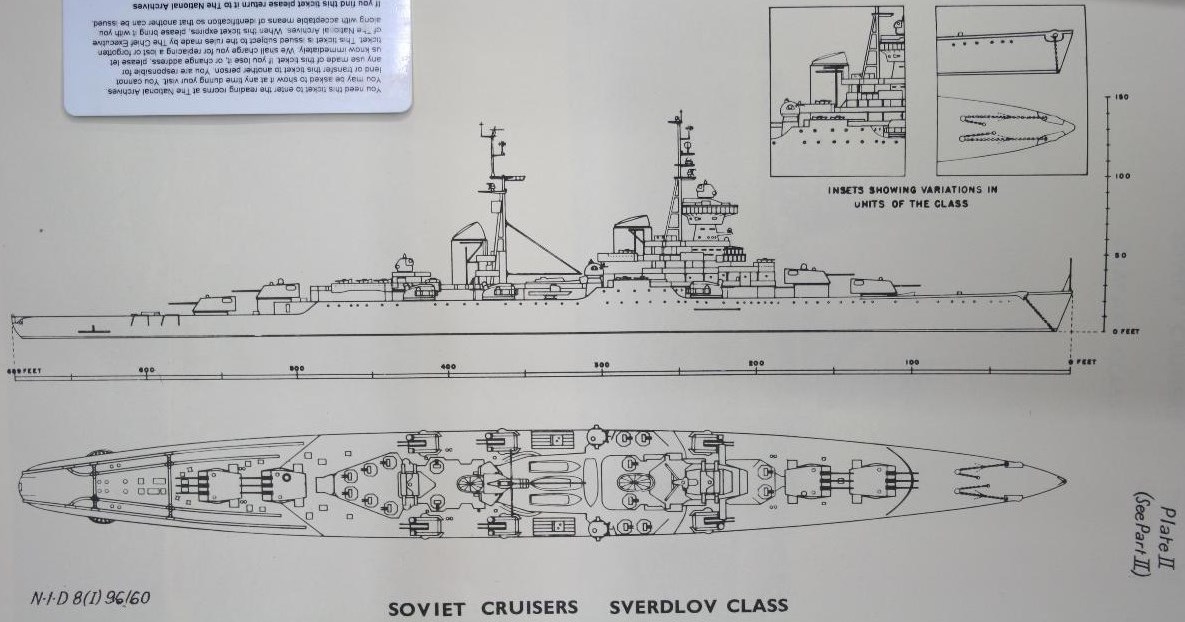
Eremeev not only discusses these wartime achievements, but the political and national impacts of such ships being built. The Sverdlov class were (even in the post-WWII/early Cold War era), powerful looking ships, fitted with the very best radars the Soviets had available,25 and had an impressive array of weaponry (see Figure 2) for the period.26 They were also big – displacing 16,000 tons,27 which is roughly double that of a modern RN Type 45 Daring-class destroyer or the U.S. Navy’s Flight I Arleigh Burke-class destroyers. The Sverdlovs were ships which were just as useful for solo raiding missions and Task Group commands as they were for peacetime ‘impression presence’ and diplomacy missions. What’s more, the Sverdlov was a light cruiser design28 and there were even bigger ships planned.29
Maximum benefit was sought from every rouble of the naval budget30 by making the most of unit presence for peacetime missions and multiplication of assets to make any opponent’s attempts to use the sea as complex as possible.31 Warfighting was about sea denial, raiding, and the tying down of enemy forces while simultaneously making their movement difficult.32 Peacetime was for building relationships, strengthening alliances, for stretching muscles, gaining experience, and hindering other actors such as Britain and the United States in their attempts to shape the world whilst simultaneously seeking to shape it themselves.33 The 1950s Sverdlovs were not though the only class of ship built by the Soviets that would fit into this mould. They were more the beginning of a story, which would continue into the 1970s with the Slava-class, Kara-class,34 and the behemoth 28,000 ton Kirov-class ‘Battlecruisers.’35 Alongside these vessels were other cruiser designs, less capable in terms of combat and command, but still with comparable status, size and armament of cruisers;36 just as large a statement of intent and capability. This capability was different from western navies, as it was not built upon the warfighting prowess of aircraft carriers. The cruiser-centered force better suited the strategic vision and peacetime presence mission profile for the Soviet Union better than any other available option.
The advantages were that cruisers are cheaper and easier to build and operate than aircraft carriers, can physically enter more ports to support diplomacy, and while being lesser in range of combat power than aircraft carriers were not necessarily lesser in combat capability within that more limited scope. This made them powerful tools for a nation which was seeking to flex its muscles around the world as a method of spreading its influence but not foment a naval arms race in the way that it was already in a strategic arms race.39 The Soviets realized that aircraft carriers, like Germany’s pre-WWI dreadnought battleships,40 would be seen as provocation and direct challenge. Cruisers were enough of challenge to be status worthy, but did not represent a direct confrontation of the carrier-centric NATO navies41 – therefore, would not be a direct attack on their confidence and thus a provocation. This is a policy though which did not stop with the end of the Cold War; in fact modern Russia has gone to great lengths to continue it.

They have done this by keeping as many of the Soviet-era ships in service as they are able to. Soviet cruisers are still the core of the Russian fleet and its capability to project influence worldwide.43 There has also been a resurgence in submarine production,44 and perhaps more interestingly, a focus on the procurement of new corvette-sized combatants.45 Additionally, there has been a significant reconstituting of amphibious warfare capability.46 Based, as this policy is, in a fairly simple and straightforward analysis of international relations that there are:
- Actors – nations which take charge and command events
- Reactors – nations which flow with the tide of events, only reacting to what happens
- Contractors – nations which get others to act on their behalf
These are classifications which can, and do change from circumstance to circumstance. The Russians have clearly chosen to equip themselves to be ‘actors’ as often as possible. This is understandable as they do not have enough reliable, capable, allies to be ‘contractors’ – and even if they did, possible ‘contractors’ often do not have sufficient influence over the course of events to satisfy and sustain Russian interests. Being a ‘reactor’ would mean that Russia would automatically cede any influence on the pace and circumstance of events. This is more than just theory and direction, it is a policy which has been illustrated by real world events in Georgia,47 Syria48 and Ukraine.49
Dr. Clarke graduated with a PhD in War Studies from KCL in 2014, the thesis of which focused upon the Royal Navy’s development of naval aviation and aircraft carrier design in the 1920s and 1930s. He was supervised during this by Professor Andrew Lambert. Alongside this he has published works on the 1950s with British Naval History, and has also published on current events with European Geostrategy and the Telegraph online as part of the KCL Big Question series. He has maintained an interest in digital history, and is organizing, hosting, and editing a series of Falklands War veterans interviews for the Center for International Maritime Security and Phoenix Think Tank. Recent research outputs include presenting a paper at the National Maritime Museum’s 2016 conference on the ASW capabilities of the RNAS in WWI, and will be presenting a paper on the design & performance of Tribal Class Destroyers in WWII at the forthcoming BCMH (of which he is a member) New Researchers Conference.
1. Tsouras (2005), p.396
2. Rodger, The Safeguard of the Sea; A Naval History of Britain, 660-1649 (2004), pp.263-71
3. Rodger, The Command of the Ocean (2004)
4. Ibid, pp.364-6
5. Mahan (1987)
6. J. S. Corbett (1911)
7. Cable, Gunboat Diplomacy 1919-1979, Political Applications of Limited Naval Force (1981), and Clarke, August 2013 Thoughts: Naval Diplomacy – from the Amerigo Vespucci to a Royal Yacht (2013)
8. Clarke, Protecting the Exclusive Economic Zones – Part I (2014), and Clarke, Protecting the Exclusive Ecconomic Zone – Part II (2014)
9. Clarke, October 2013 Thoughts (Extended Thoughts): Time to Think Globally (2013)
10. Air forces, as has been highlighted recently also experience issues – with other nations probing air space; but still they do not face potential problems on the scale or diversity that navies could experience, especially navies belonging to nations with far flung territories strewn around the globe.
11. Flournoy and Brimley (2009)
12. Hipple (2014)
13. TNA: ADM 223/714 (1959), and TNA: ADM 239/533 (1960)
14. Sergey Gorshkov (1980, p.230) goes into great detail as to the diference between the idea of dominance at sea adopted by Russian in comparison to England, and America which had inherited the English model.
15. Massie (2005) – a conclusion which is further supported by the experience of Japan in WWII, it had also chosen to build a scaled battlefleet, and whilst with its challenges this did make some sense – its lack of infrastructure to support a rapid expansion of its fleet to equivalent levels meant that although it suited the cultural/political perception of its national leaders, it was not necessarily as sensible as a less conventional fleet structure might have been (Stille, The Imperial Japanese Navy in the Pacific War 2014).
16. A. Clarke, August 2013 Thoughts: Sea Based Conventional Deterrence; more than just gunboat diplomacy! (2013)
17. Polmar (1991), and TNA: ADM 239/821 (1959), both highlight how often ships with very capable surface-to-surface and surface-to-air weaponry, for example the Kara Class (Polmar (1991), pp.155-7) are described as ASW Guided Missile Cruisers, yet both their SA-N-3 Anti-Aircraft missiles, and SS-N-14 anti-submairne missiles, had significant anti-ship capability (especially the latter, which being torpedos at their terminal stage are arguably more dangerous than a pure missile system)…furthermore as the class was built, one of the class, Azov, had it’s air-defence upgraded to include the far better SA-N-6 (which also has an anti-ship capability), and all of the class were built with extenseive command and control facilities.
18. Clarke, Europe and the Future of Cruisers (2014)
19. Clarke, Sverdlov Class Cruisers, and the Royal Navy’s Response (2014)
20. TNA: ADM 223/714 (1959)
21. TNA: ADM 116/4109 (1940)
22. TNA: ADM 116/4109 (1940), TNA: ADM 116/4320 (1941), and TNA: ADM 116/4470 (1940)
23. TNA: ADM 223/714 (1959)
24. TNA – Admiralty: 116/4109 (1940)
25. A. Clarke, Sverdlov Class Cruisers, and the Royal Navy’s Response (2014)
26. Rohwer & Monakov (2006), pp.199
27. Ibid, pp.197-9
28. Rohwer & Monakov (2006), pp.197-9, and Polmar (1991), p.164
29. Rohwer & Monakov (2006), pp.194-7
30. Gorshkov (1980), p.248, and Dismukes & McConnell (1979), pp.88-114
31. Gorshkov (1980), pp.213-77, and Dismukes & McConnell (1979), pp.1-30
32. Rohwer & Monakov (2006), pp.215-6, G. S. Clarke (2007), and Gorshkov (1980), pp.213-22
33. Rohwer & Monakov (2006), pp.215-6, G. S. Clarke (2007), and Gorshkov (1980), pp.245-53
34. Polmar (1991), pp.155-7
35. Ibid, pp.148-51
36. For example the Slava, Kresta and Kynada classes (Polmar (1991), pp.152-4 & 158-63)
37. Rohwer & Monakov (2006), p.199, and TNA: ADM 239/533 (1960)
38. TNA – Admiralty: 239/533 (1960)
39. Rohwer & Monakov (2006), illustrates this in their work by highlight how many grandiose naval schemes were planned, and enver completed; when if the will had been present, and decision had been made, then the Soviets under Stalin could have allocated the resources to do it.
40. Massie (2005)
41. Clarke, Sverdlov Class Cruisers, and the Royal Navy’s Response (2014)
42. Wikimedia Commons (2015)
43. Janes (2006), or for those wanting quick verification of this then there is the Russian Navy Website (http://rusnavy.com/nowadays/strength/) or Wikipedia (https://en.wikipedia.org/wiki/List_of_active_Russian_Navy_ships) for those preferring something slightly more straightforward.
44. Cavas (2015)
45. Pike (2015)
46. Keck (2015), and Defence Industry Daily Staff (2015)
47. Georgia: McGuinness (2013), and King (2008)
48. Syria: Keck, Russia’s Aircraft Carrier to Visit Syrian Naval Base (2013), and Daily Mail Reporter (2011)
49. Ukraine: Harress (2015)
Featured Image: The Pyotr Veliky nuclear-powered Kirov-class cruiser. (Wikimedia Commons)