European Maritime Security Topic Week
By Martin N. Murphy, PhD and Gary Schaub, Jr. PhD
Hybrid Warfare
The governments and peoples of the Baltic States recognize that, following Russia’s takeover of Crimea and intervention in eastern Ukraine, they are once again in the Kremlin’s sights facing the prospect of Russian destabilization and even outright invasion.
NATO’s leadership termed Russian strategy “hybrid warfare,” defining it as warfare in which “a wide range of overt and covert military, paramilitary, and civilian measures are employed in a highly integrated design.”1 Questions were raised immediately about the suitability of the designation, as the label NATO adopted fails to adequately capture the reality of what Russia inflicted on Ukraine—and may inflict on states in the Baltic Sea Region (BSR) in the near future.
Russian successes in Crimea reinvigorated two longstanding instruments of its power: its armed forces and its capacity for intensive information warfare.2 “Grey-zone” perhaps captures the orchestrated multidimensional nature of Russian actions calibrated to gain specified strategic objectives without crossing the threshold of overt conflict and exploit Western concepts of war and peace as two distinct conditions.3 Any conflict between NATO and Russia will likely occur at the Article 4 rather than the Article 5 level, complicating any Western response.4
Hybrid War in the BSR: Political and Information Warfare Dimensions
It is possible to count all the fighters, bombers, troops and ships in the Baltic and arrive at a correlation of forces. But the BSR is a peripheral region, and only three things matter when it comes to its security:
- The commitment of core NATO powers – especially the U.S. – to the region’s defense;
- Russia’s determination to restore its sphere of influence in the region; and
- Russia’s desire to probe for Western weakness.
Russia is interested less in territory than in effect. NATO’s focus on military measures to defend the Baltic States may overlook the challenge posed by all arms of Russian power to identify and exploit political, social, economic, and military vulnerabilities in its target states and the Western alliance.
These dimensions have been underplayed in NATO thinking, a tendency reinforced by the military nature of its Charter and institutional culture. Questions remain as to whether NATO’s own legal framework and traditional instruments are sufficient to deal with these non-military challenges, and certainly whether they can respond to a fast-changing situation. The means Russia is prepared to use in order to deceive and confuse NATO are based on the same tools it used during the Cold War, but it has adapted them to the mores of the social media age, which lacks the experience to judge the import of Russian messaging or actions.
Applying the Hybrid Model to Warfare at Sea
Russia’s high-end forces would not constitute the first movers in a hybrid conflict. They should be regarded as deterrents to local resistance and intervention by NATO and other Nordic states. It would rather pursue more ambiguous methods.
Broadly speaking, two scenarios for a Russian campaign in the BSR appear possible:
1. A low-key, possibly opportunistic, campaign that exploits real or manufactured discontent among Russian compatriots to destabilize one or more of the Baltic States, creating a “frozen conflict” that undermines NATO’s credibility; or
2. A more structured, high-tempo campaign to achieve the same objectives against NATO power in the BSR and also render Nordic defense cooperation redundant.
It is reasonable to assume that the Baltic Sea Fleet and other organs of Russian maritime power will play supporting rather than leading roles in any such conflict.
Aside from Moscow’s ability to manipulate the loyalty of Russian expatriate communities in the Baltic states, many of the points where it can apply pressure lie on or under the Baltic Sea itself. These include:
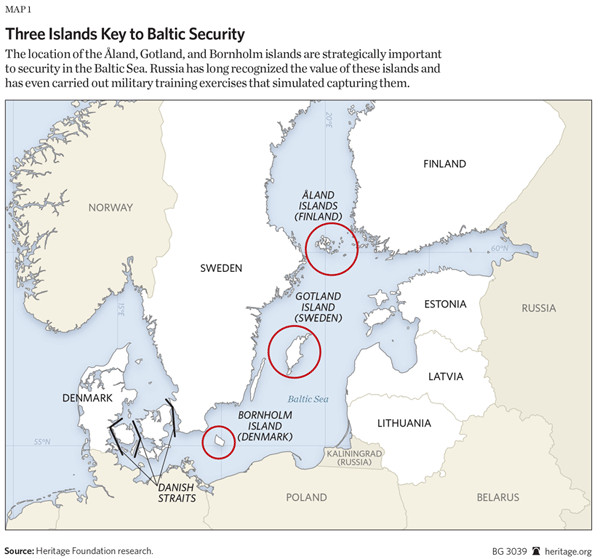
Geographically Isolated Islands and Disputed Borders
The Bornholm, Gotland and the Aland group are respectably Danish, Swedish, and Finnish islands that have considerable strategic significance in the BSR. Many are ideal as bases, supply points, staging areas, and jumping off points for SOF operations and ambushes, while bays, fjords, and peninsulas provide hiding places and launch points for fast raiders.
Undersea Cables
Modern economies depend upon a remarkably vulnerable information and communications infrastructure. Roughly 95 percent of intercontinental communications traffic—e-mails, phone calls, money transfers, and so on—pass through fiber-optic cables that “lack even basic defenses, both on the seabed and at a small number of poorly guarded landing points.”5
When it comes to the Baltic Sea particularly, Poland, Lithuania, and Latvia have only a few nodes that need be severed, while Estonia, the Nordic countries, and Germany have much more redundancy in their connections. Still, the economic disruption caused by severing these undersea cables would be considerable in time and cost and be difficult to mitigate, even for those countries with multiple nodes. They would therefore be a prime target in a hybrid warfare campaign.
Energy Supplies
It has long been recognized that Estonia, Latvia, Lithuania, and Poland depend upon Russian energy. This exposes them to the possibility of economic coercion. These states have reduced their dependence on Russian supplies, but diversification has been difficult given the cost of replacing existing infrastructure and vulnerabilities remain.
Port and Supply Chain
Ports and ships could be subject to sabotage and strikes using SOF as part of a hybrid offensive. Yet the most serious threat could come from cyberattacks, a concern that already animates much of the landward resilience debate. Modern ports could not operate absent sophisticated computer systems, while modern ships are increasingly automated to cut crew costs. Any prolonged interference with the region’s maritime trade could severely impact industrial production flows and economic security.
Why Would Russia Disrupt the BSR?
Russia is a revisionist power. Internationally, it wants to revise the existing regional order at the least possible political and military cost to itself, diminish U.S. power, and further a multipolar world. Domestically, Putin’s government requires an enemy to divert attention from internal troubles. The Baltic States lie at the point where American power is most extended and Russian power can be concentrated most easily. As Russia is under no illusion it can fight the U.S. directly, or a coalition of America’s core allies, its challenges will stay below the level of direct confrontation.
The Soviet Union invested around fifty percent of its shipbuilding capacity in the St. Petersburg area. A second vital facility is located in the Kaliningrad Oblast. The Baltic Sea has also become a vital conduit for Russian trade. Prolonged interruptions in flows of energy and goods would inflict considerable damage on Russia’s poorly diversified economy. During 2015, 52 percent of Russian container traffic passed through St. Petersburg. Europe remains a major customer for Russian crude oil shipped by tanker from ports near St. Petersburg. On the seabed is the Nord Stream gas pipeline. A second pipeline–Nord Stream 2–has been proposed that would double the capacity. This connection reinforces the dependency and mutual interest that already exists between the EU and Russia and risks compromising Western European responses to possible Russian aggression in CEE.
The Baltic Sea Region has plentiful points of vulnerability where Russia can test Western resolve. While these are not confined to the Baltic States, the most obvious point of leverage is the Russian minorities who reside in each one with concentrations in port cities and other maritime areas.6 Nor are the Baltics removed from Russia’s deeply ingrained sense of insecurity arising out of its loss of strategic depth. Advancing the Russian right flank to the Baltic Sea would right a perceived wrong, prevent the encirclement of Kaliningrad, the main base of the Russian Baltic Sea Fleet, and provide a platform from where Russia could threaten the entire Baltic Sea littoral.
Sweden and Finland are clearly concerned about this possibility. Sweden has returned its army garrison to the strategically important island of Gotland, while towns and cities across Sweden have been told to make preparations against a possible military attack.7 Conscription has also been reintroduced.8 However, any move by either to join NATO could “provoke Russia to launch a pre-emptive provocation in order to demonstrate the alliance’s weakness” and deter either country from proceeding with its application.9
Russian Military Capability
Despite the importance of the Baltic Sea routes, the Russian Baltic Sea Fleet is the weakest of Russia’s four fleets (Baltic, Black Sea, Pacific, and Northern). It continues to have the lowest priority for new units.
That does not mean modernization has not taken place. Since 2007, the fleet has been upgraded with two new classes of corvette equipped with land-attack missiles, a capability that is new to the Baltic Sea fleet.10 However, the fleet’s submarines have not been modernized and remain inferior to German and Swedish boats. Lacking AIP propulsion, which Russian industry is having problems mastering, they are also likely to be noisier. The fleet’s anti-submarine warfare (ASW) and mine counter-measures (MCM) capabilities are also limited.

That said, the Baltic Sea is relatively small with an average width of only 193km (120 mi). The sea and surrounding littoral can–and almost certainly would–be dominated by air power and air-deployable ground forces in any high intensity conflict. In particular, Russia is able to effectively dominate large areas of the Baltic Sea and air space using missile forces based in the Kaliningrad and Leningrad oblasts.11 The Iskander-M mobile ballistic missile is capable of hitting targets in much of Sweden and from southern Poland to central Finland, whether fixed or mobile.
NATO movement would be affected in all environments: air transports bringing reinforcements into theater would be at risk from manned interceptors and a layered, air-and-missile defensive system equipped with the S-300 and the highly-capable S-400 systems. Movements by sea would be threatened by the Bastion-P coastal defense system based on the supersonic 300km-range P-800 Yakhont anti-ship missile, which Russia has announced will shortly be deployed to the Kaliningrad Oblast.12
NATO ground forces, meanwhile, would need to travel further than Russian units to reach the capitals of the Baltic states and throughout the transit could be subjected to long-range air and ground-based bombardment.
Naval “Hybrid Warfare”
Hybrid warfare as deployed by Russia in Crimea and Eastern Ukraine has received considerable analytical coverage; hybrid warfare at sea less so.13 The geography of the Crimea and Ukrainian theaters, and the circumstances of the incursions, meant the naval role was limited in both. However, Russia appears to have taken note of the success China has achieved with hybrid warfare tactics in the South China Sea, including its harassing behavior as multiple incidents have taken place on and over the Baltic and Black Seas.14 At the same time, Russia has resumed Soviet-style probing missions against NATO countries, while the Baltic states, Sweden, and Finland have all had their territorial waters and airspace compromised.15
The Chinese have made extensive use of their maritime paramilitary forces to assert maritime claims and to deny neighboring states access to waters for fishing and resource extraction purposes. The opportunities for the disruptive use of coast guard and border forces appear to be less in the BSR yet Russian behavior–for instance withholding ratification of the Narva Bay and Gulf of Finland Treaty–demonstrates that they are maintaining the potential for disruption inherent in the handful of disputes that remain.16
Mitigation Measures
Given the essentially political nature of hybrid war, mitigation measures should focus on political, economic, and information outcomes. Still, Russia needs to be convinced that all BSR states are committed to challenging Russian aggression at sea. The maritime component of NATO’s 2014 Readiness Action Plan includes intensified naval patrols in the Baltic built around the Standing NATO Maritime and Mine Countermeasures Groups, increased sorties by maritime patrol aircraft, and an expansion of the annual BALTOPS naval and amphibious exercise.17 However, BALTOPS in large measure still reflects the Alliance’s focus on high-end military operations. Changes have been made that broaden its focus and these need to be maintained and expanded in order to continuing raising maritime readiness and interoperability standards at all stages along the deterrence-to-conflict continuum. In addition, both Baltic and NATO navies need to exercise lower-end maritime security, VBSS, fishery protection, and SAR missions, while regional navies need to demonstrate they can act seamlessly with regional coast guards and border forces, port authorities and other maritime agencies, police forces and intelligence services. Furthermore, cooperation in intelligence sharing and analysis through a BSR Hybrid Threats Fusion Cell coupled with a strategic communications response capability to provide swift and consistent factual responses to false narratives would contribute to building societal resilience.
Societal resilience also requires less dependence on Russian energy supplies. A new facility for the import and regasification of liquefied natural gas (LNG) has been built at Klaipeda in Lithuania. Ensuring its security is vital. Further diversification could be achieved if additional terminals were to be built in Estonia and Latvia with reversible-flow pipelines linking all three. Ideally, a trans-Baltic pipeline should be built to link the Baltic States with the Swedish system.18 These pipelines would supplement the “NordBalt” power cable laid between Sweden and Lithuania. Notably, this link was interfered with by Russian warships on three occasions during the course of its construction. Finally, BSR states need to place a strong emphasis on port and supply chain security. This must include defenses against cyber-attacks. Protecting this largely maritime infrastructure would place a premium on effective Baltic Sea maritime domain awareness (MDA).
Conclusion
Russia considers itself to be a maritime power. It has always sought to control the seas that give it access to the world ocean. The Baltic Sea is vital in this regard. Despite this perception, Russian power, when compared to its Soviet predecessor, is sadly diminished. It is therefore understandable that it should continue to augment its remaining military power with the measures of influence, deception, and covert action that were so characteristic of the Soviet approach to inter-state relations.
Any repetition of the Crimean model is likely to be a whole-of-government effort of political subversion and destabilization in which the conventional military—as opposed to SOF and proxy militia—will play a largely passive role until the last minute, or unless the political campaign fails and can only be redeemed using conventional military force. Whole-of-government aggression demands a whole-of-government response.
In this sense, there is no such thing as maritime hybrid warfare, certainly in Russian political or military doctrine or practice. What states in the BSR may be confronting even now, however, is a long-term campaign of politically motivated societal disruption, aspects of which may occur in, through, or from the maritime domain. The seaborne aspects of the campaign will be maritime rather than exclusively naval in that what takes place could involve any of the ways people use the sea, the seabed, and the airspace over the sea. It will involve warships, submarines, and military aircraft but also include fisheries, shipping and ports, coast guards, and border forces along the way. Conventional naval forces are likely to play an analogous background role in any disruptive campaign at sea in the Baltic, as they did during the Crimea invasion and Ukraine intervention.
Martin N. Murphy, PhD is a Visiting Fellow at Corbett Centre for Maritime Studies at King’s College London. He has held similar positions with CSBA and the Atlantic Council in the U.S. He is the author of three books and numerous book chapters and articles on maritime security and unconventional warfare at sea. His next book, On Maritime Power, is due for publication in 2018.
Gary Schaub, Jr., PhD, is a Senior Researcher at the Centre for Military Studies, Department of Political Science, University of Copenhagen. Before that he held a number of academic positions in the U.S. including Assistant Professor of Strategy at the U.S. Air War College.
References
1. NATO. ‘Wales Summit Declaration’. Issued by the Heads of State and Government participating in the meeting of the North Atlantic Council in Wales, 5th September 2014.
2. Kier Giles, et al. ‘The Russian Challenge’, Chatham House Report, June 2015, p. 46. NATO Article 4 states that “The Parties will consult together whenever, in the opinion of any of them, the territorial integrity, political independence or security of any of the Parties is threatened.” NATO, ‘The North Atlantic Treaty’, last updated 21st March 2016.
3. For clear definitions of “hybrid” and “grey-zone” conflicts, and comparisons between the two, see Frank Hoffman. ‘The Evolution of Hybrid Warfare and Key Challenges’. Statement before the House Armed Services Committee, 22nd March 2017.
4. Stephen F. Larrabee, et al. Russia and the West after the Ukrainian Crisis: European Vulnerabilities to Russian Pressures. Santa Monica: RAND, 2017, pp. 10-11.
5. Robert Martinage. “Under the Sea: The Vulnerability of the Commons,” Foreign Affairs, Vol. 94, No. 1, January/February 2015, p. 117.
6. Martin N. Murphy, Frank G. Hoffman and Gary Schaub, Jr. ‘Hybrid Maritime Warfare and the Baltic Sea Region’. Copenhagen: Centre for Military Studies, University of Copenhagen, November 2016, pp. 11-14.
7. Richard Orange. ‘Swedish towns told to “make preparations regarding the threat of war and conflict” with Russia’. Daily Telegraph, 15th December 2016.
8. Daniel Dickson; and Bjorn Rundstrom. ‘Sweden returns draft amid security worries and soldier shortage’. Reuters, 2nd March 2017.
9. Edward Lucas. ‘The Coming Storm: Baltic Sea Security Report’. Washington, DC: Center for European Policy Analysis, June 2015, p. 4.
10. ‘Russia reinforces Baltic Fleet with ships armed with long-range cruise missiles in ‘worrying’ response to Nato build-up’. Daily Telegraph, 26th October 2016.
11. Kaas. ‘Russian Armed Forces in the Baltic Sea Region’.
12. ‘Russia deploys “Bastion” coastal missile complex to the Kaliningrad region’. UAWire, 22nd November 2016.
13. Charles K. Bartles and Roger N. McDermott. ‘Russia’s Military Operation in Crimea: Road-Testing Rapid Reaction Capabilities’. Problems of Post-Communism, Vol. 61, No. 6, November–December 2014, pp. 46–63; Admiral James Stavridis, USN (rtd.). ‘Maritime Hybrid Warfare is Coming’. U.S. Naval Institute Proceedings, Vol. 142, No. 12, December 2016, pp. 30-33.
14. For example, Julian E. Barnes and Gordon Lubold. ‘Russian Warplanes Buzz U.S. Navy Destroyer, Polish Helicopter’. Wall Street Journal, 13th April 2016.
15. Thomas Frear, Łukasz Kulesa and Ian Kearns. ‘Dangerous Brinkmanship: Close Military Encounters between Russia and the West in 2014’. European Leadership Network Policy Brief, November 2014.
16. ‘Russian envoy: Ratification of border treaty with Estonia obstructed by bad relations’. The Baltic Times, 9th July 2016.
17. NATO. ‘NATO’s Readiness Action Plan’. NATO Fact Sheet, May 2015; Megan Eckstein. ‘U.S. Led BALTOPS 2015 begins with heftier presence than last year’s exercise,” USNI News, 5th June 2015; Megan Eckstein.‘Foggo: BALTOPS 2016 includes more anti-sub, more challenging amphibious operations’. USNI News, 15th June 2016.
18. Milda Seputyte. ‘Lithuania grabs LNG in effort to curb Russian dominance’. Bloomberg, 27th October 2014; ‘Sweden gets new LNG terminal’. World Maritime News, 20th October 2014.
Featured Image: Soldiers sit atop of amphibious vehicles as NATO troops participate in the NATO sea exercises BALTOPS 2015 that are to reassure the Baltic Sea region allies in the face of a resurgent Russia, in Ustka, Poland, Wednesday, June 17, 2015. (AP Photo/Czarek Sokolowski)







