By Harry Halem
Introduction
This past January, Benjamin Netanyahu undertook a high-profile visit to India, becoming the second Israeli Prime Minister to travel to the country. Accompanied by a 130-member delegation, Netanyahu’s trip included a stay in New Delhi, and visits to the Taj Mahal, Mahatma Gandhi’s grave, and Gandhi’s home in the state of Gujrat. The personal relationship between Netanyahu and his Indian counterpart, Narendra Modi, seems extremely strong – in a distinct break from protocol, Modi greeted Netanyahu at the airport, an honor denied to the popular Canadian Prime Minister Justin Trudeau during his visit a month later.
Netanyahu and Modi’s strong personal relationship indicates the growing closeness of Indo-Israeli relations. While India opened an embassy in Tel Aviv only 26 years ago, since the two countries have engaged in growing levels of trade and military cooperation – the present diplomatic evolution simply reflects underlying trends. Since 1992, India has also engaged in a sustained rapprochement with the United States. Tacitly aligned with the Soviet Union during the Cold War, the USSR’s collapse revolutionized India’s strategic situation, and has resulted in progressively improving relations with the U.S., despite multiple hiccups along the way.
Strategic trends dictate growing areas of cooperation between India, the U.S., and Israel, particularly in the maritime sphere. As such, U.S. policymakers are faced with the unique opportunity of being able to forge an alliance with a major power that could revolutionize American security architecture in the Near East and Indian Ocean. Despite the potential points of Indo-American and Indo-Israeli friction that remain, Washington can use the relationship between its critical Near Eastern ally and New Delhi to actualize the full potential of this partnership.
The Development of Indian Foreign Policy – Non-Alignment to Balancing
India’s shifting policy toward the West is the culmination of steady changes in India’s approach toward the external world since its independence in 1947. Despite its initial war with Pakistan, India faced few external threats during its first decade of independent existence. Its armed forces were employed internally, enabling the absorption of reticent enclaves into the fledgling Republic. Jawaharlal Nehru, India’s first Prime Minister, embarked upon an anticolonial foreign policy, using India’s ostensible moral capital to build links with other nations emerging from their colonial pasts.
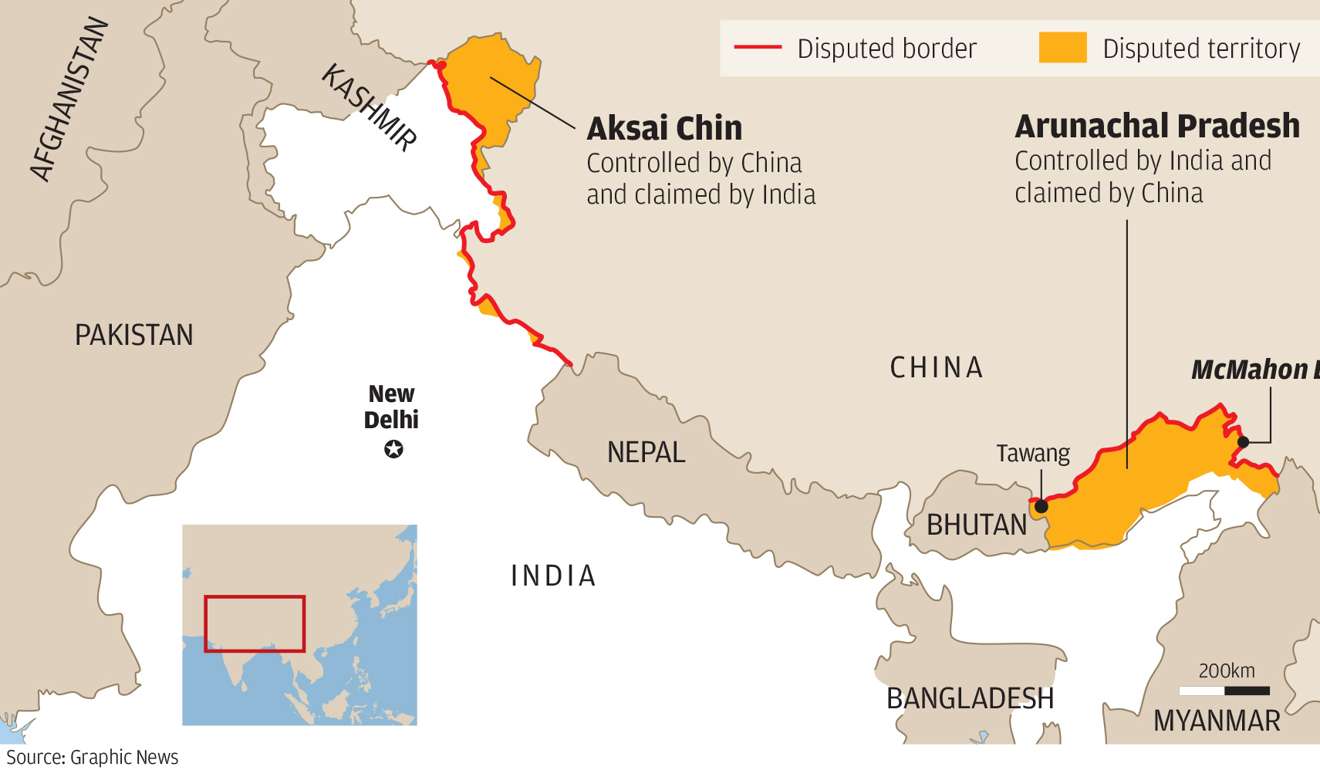
The outbreak of war with China in 1962, therefore, was a distinct shock for the Indian governing establishment. Up until that point, China had been viewed as a Marxist brother in arms – Nehru hoped to anchor Indian foreign policy on cooperation with China, and use the combined authority of the two formerly colonial powers to remain independent from the Cold War. Despite its border dispute with China, the PRC’s invasion across the McMahon Line and into Ladakh was utterly unanticipated. Not only were India’s armed forces unprepared for conflict in Jammu and Kashmir’s harsh mountain conditions against the more experienced People’s Liberation Army, China also executed its offensive concurrent with the Cuban Missile Crisis, ensuring that neither Washington nor Moscow could properly focus on the region and lend New Delhi support until after Beijing consolidated its initial gains.
Following the Sino-Indian War, India’s foreign policy shifted away from its idealistic roots. However, relations between India and the West remained chilled, particularly over America’s persistent support for Pakistan, a critical facilitator in Nixon and Kissinger’s attempts to realign China during the early 1970s. Ideologically, the socialist, anti-Imperialist Indian National Congress (INC), which dominated Indian politics until the late 1970s, found the Soviet Union to be a more amenable partner than the United States, with its capitalist ideology and close relationship with Britain and other former colonial European powers, while the Kremlin had a progressively increasing interest in balancing China as relations cooled and animosity increased from Stalin’s death onward. India’s relationship with Israel was similarly frigid, albeit for more pragmatic reasons. India initially refused to recognize Israel, and remained wary of appearing too close to the Jewish state despite recognition in 1950. Indian politicians feared the response of the significant Muslim minority population if New Delhi formally opened an embassy in Tel Aviv. Moreover, India was dependent upon Israel’s Arab adversaries for energy supplies, relied on the Persian Gulf states to maintain Indian foreign exchange reserves, and significantly benefited from the productivity of Indian nationals working in the Near East. Formally engaging with Israel would therefore have risked Indian economic and energy security.
The Cold War’s conclusion was a major turning point for Indo-Israeli and Indo-American relations. INC progressively lost its political monopoly from Indira Gandhi’s ouster in 1977 after unprecedented centralization. By 1989, India’s political environment had become much more balanced, with various opposition parties, namely the Bharatiya Janata Party (BJP) and its affiliates challenging long-standing socialist economic policies, and implementing free market reforms. American loans underwrote India’s market liberalization. The U.S. also identified India as a potential defense export market, and gradually increased technological transfers. More notably, the U.S. Navy began its Malabar exercises with its Indian counterpart in 1992, explicitly focusing on rehearsing combat operations, rather than non-wartime activities. Indo-American relations then cooled in 1998 when the Clinton administration sanctioned India for its nuclear testing. However, President Clinton quickly abandoned his sanctions policy, while President Bush identified India as a critical potential partner in the Global War on Terror after the September 11th Attacks. The Malabar naval exercises have continued to increase in scope, while Indian Navy and U.S. Navy ships cooperate on antipiracy, counterterrorism, and other maritime patrol missions in the Indian Ocean.
Indo-Israeli relations also progressively thawed. India opened an embassy in Tel Aviv in 1992. Economic relations have flourished since, while India and Israel also have a progressively expanding security relationship. Indian forces have participated in training exercises in Israel, while Israeli defense companies sell advanced technologies to the Indian military – India has used Israeli drones to offset the advantages of its regional rivals. Increased state visits demonstrate the strength of this relationship: the Netanyahu-Modi visits are only the most recent of a rising number of high-profile diplomatic exchanges. Additionally, significant are changes in Indian rhetoric. In the 2014 Gaza War, India broke with its previous strong condemnation of Israeli action in the Palestinian territories, instead blaming both parties for the conflict, and calling upon the Israel Defense Forces (IDF) to limit civilian casualties. This reflects a broader attempt to “de-hyphenate” Indo-Israeli relations: New Delhi wishes to build an independent relationship with Tel Aviv, regardless of the Palestinian issue. One can only expect this cooperation to increase in the future.
The Strategic Roots of Cooperation
Policymakers rarely have the opportunity to forge new, lasting alliances. The uncertainty of the international environment makes ensuring sustained cooperation difficult, particularly among great powers – a cursory observation of Sino-Russo-American relations from 1945 to the present indicates this fact. However, the clear confluence of interests between India, Israel, and the United States makes the potential for cooperation extremely high, particularly in the maritime domain.
The U.S. and Israel have clear shared interests in the Eastern Mediterranean, Arabian Gulf, and Indian Ocean. Both require Near Eastern stability to advance their interests. The Islamic Republic of Iran is presently the greatest regional threat to both of their goals. Iranian influence in Iraq, Syria, and Lebanon poses a physical threat to Israeli security through irregular assets like Hezbollah and their missile capabilities, or, potentially in the future, a direct threat from conventional ground forces. Iranian expansion in the Indian Ocean also threatens the U.S.’ ability to impose a “far blockade” on China in the event of conflict by attempting to closing the Strait of Hormuz and pressure American sea lines of communication running from the Near East to the Western Pacific. Hence, Israel and the U.S. have a clear joint interest in ensuring their control over the Eastern Mediterranean and Indian Ocean.
India and the U.S. also share a critical interest concerning China. China is a blatant threat to India’s sphere of influence in South Asia. The Doklam Crisis is only the most recent evidence of Chinese encroachment on Indian or Indian allied borders, while China’s hedging strategy involves supporting India’s chief rival, Pakistan. India is the only regional actor that can offer China significant resistance without external support. The qualitatively sophisticated JSDF and Taiwanese militaries are too small to sustainably challenge the PLA absent American aid, while the Vietnamese and Philippine Armed Forces are qualitatively and quantitatively outmatched. India’s active military ranks only behind China’s numerically, while if reserves and paramilitary groups are included, the Indian Armed Forces could field nearly two million more personnel than the PLA. Moreover, as a nuclear-armed state, India can limit Chinese escalatory options in a way no other regional power can. However, India’s military is outmatched by the PLA. The PLAAF fields more combat aircraft than its Indian counterpart, and faces only three substantial regional threats aside from India – the Taiwanese Air Force, Japanese Air Self Defense Forces, and Republic of Korea Air Force (assuming the ROK is not tied down in some fashion by North Korea either through conflict or deterrence requirements) while the Indians will need to divert forces to deterring or fighting Pakistan’s Air Force in any conflict. At sea, the PLAN outmatches the Indian Navy. The PLAN’s two STOBAR carriers’ air wings match the INS Vikramaditya’s in size, while it outnumbers India in every surface combatant category. In the near future, the Indian Navy could face as much as a one-to-four disadvantage in a conflict with the PLAN. Nevertheless, India has a commanding geographic position over the approaches to and from the South China Sea, and can use both naval forces and land-based maritime patrol craft to prevent PLAN surface combatants from entering the Indian Ocean. Considering concurrent American interest in countering China’s rise, formalized cooperation between the U.S. and India would significantly improve the relative position of both countries in the Indian Ocean and South Pacific.
Israel and India also share a number of direct interests outside of their present economic and military transactions. Israel is not directly threatened by China – indeed, Israeli companies have sold the PLA military technology – while India relies on Iran for a significant portion of its energy imports. However, both have a clear interest in Indian Ocean maritime security. Chinese patrols in the Indian Ocean could pressure Indian supply lines, while China’s growing economic relationship with Iran could allow it to diplomatically leverage the Islamic Republic into choking off its oil flows to New Delhi. Israel, alternatively, would be unable to respond to Chinese submarine harassment of Israeli shipping in the Indian Ocean. Despite the IDF’s military sophistication, it lacks a blue water navy, and small powers remain at the mercy of larger adversaries in conflict absent a great power partner. Additionally, damage inflicted upon the Indian economy would harm Israel’s own productivity: Israel has a clear interest in ensuring India remains insulated from Chinese economic pressure. Finally, Israel could benefit from the ability to pressure Iran from the Indian Ocean, rather than simply overland. The U.S. Navy’s current presence in the Arabian Gulf allows for greater Israeli freedom of action on land. However, Israel would benefit from having its own naval forces, giving it the ability to act more independently.
These bilateral interests cohere into a broader whole. India, Israel, and the U.S. would all benefit from a more formal maritime arrangement in the Indian Ocean, while each nation would directly or indirectly benefit from the increases to the others’ security. These overlapping strategic interests are reinforced by the broader desire of all three potential partners to combat terrorism and respond to Islamic extremist organizations. With the roots for cooperation evidently existing, one must understand how to leverage this into a more explicit framework.
Future Steps to Facilitate Cooperation
Despite the clear cooperative potential between India, the U.S., and Israel, actualizing cooperation is a difficult task. Israel would likely be hesitant to be drawn into a formalized security architecture that would commit it to defending tangential interests with force, while India would reasonably be wary of jeopardizing relations with Iran, and by extension its access to oil. Nevertheless, American policymakers can take several steps to increase cooperation and lay the groundwork for a broader Mediterranean-Indo-Pacific security architecture that can respond to increasing Chinese, Russian, and Iranian southward pressure. Four specific policy recommendations can actualize this cooperation.
First, the U.S. should consider inviting the Israeli Navy to future iterations of the Malabar Exercises. Israel’s participation at Malabar would be a public way to signal Indo-Israeli cooperation, without Israel making any formal commitments in the Indian Ocean. Ensuring the stability of military-to-military contacts between the IDF and Indian Armed Forces will help insulate the security relationship between Israel and India despite changes in administration. Other joint training exercises are possible, and would be beneficial. India already sends fighter aircraft and Special Operations Forces units to Israel for various activities – America’s CENTCOM military forces could engage in exercises along their IDF and Indian Armed Forces counterparts.

Second, the U.S. can encourage further defense cooperation by making a concerted effort to win over the Indian market. The Indian military largely uses Soviet and Russian equipment. All but six percent of the Indian Army’s main battle tanks, and 20 percent of its combat aircraft, are Russian made or designed. Two-thirds of the Indian Navy’s attack submarine fleet, and slightly under half of its large surface combatant fleet of guided missile destroyers and frigates were produced in Russian shipyards. The U.S.’ high-cost systems, and Israel’s smaller industrial base, makes it difficult to imagine either one of them singlehandedly crowding out Russian production. But at least when it comes to surface combatants, one could envision Israeli or American ships being increasingly represented in the Indian fleet, with Israeli and American-designed small surface combatants competing for purchase. Moreover, the Indian Navy’s undersized submarine fleet offers U.S. producers an opportunity to revive diesel-electric submarines, and produce cheaper platforms to counter growing Chinese numerical superiority. Just as the British shipbuilding industry benefited from building capital ships and surface combatants for foreign nations before the Great War, American shipyards could help expand and maintain critical wartime capacity by producing warships for friendly and allied foreign powers. This could extend to IDF and American tanks and other armored vehicles replacing Soviet and Russian alternatives. Israel’s unmanned expertise is a critical facilitating factor. The Indian Air Force already uses Israeli UAV’s, namely the IAI Harop, a loitering munition, the IAI Searcher, a light scout platform, and the IAI Heron, a MALE reconnaissance and strike UCAV. Not only will demand for these sorts of platforms grow, as armed forces globally develop their understanding of teaming between manned and unmanned assets, but increases in AI technology will likely lead to a fully unmanned fighter aircraft in the next two to three decades. India, the U.S., and Israel would all benefit from research and production of such platforms – or risk being left behind by their Russian and Chinese rivals, who are undoubtedly engaging in developing those capabilities.
Third, American diplomacy can help decrease Iran’s role in India’s energy supply by leveraging energy supplies in the Eastern Mediterranean’s Leviathan Gas Field and other neighboring energy deposits. Current exploration indicates that these newly-discovered Eastern Mediterranean resource deposits contain upwards of 16.5 trillion cubic feet of gasoline. Combined with an increase in already high exports from Saudi Arabia, and a concerted effort to export North American oil and natural gas to India, the U.S. can decrease the proportion of India’s Iranian energy imports, and thereby give India the ability to more openly cooperate with the U.S. and Israel by lessening energy security risks.
Fourth, the U.S. should explore political and military relationships with India to increase security in the Indian Ocean. The present Indo-American relationship is remarkably similar to the early stages of Anglo-French cooperation before the First World War. The 1912 Anglo-French Naval Convention, in which Britain offered to secure the North Sea and France’s Atlantic coastline in return for France’s safeguarding of British interests in the Mediterranean, allowed Britain to concentrate its forces against the Imperial German Kaiserlichmarine while maintaining a degree of security in other global chokepoints. Even if implemented successfully, the PLAN will outnumber the U.S. Navy by nearly 150 ships in 2030, and could outnumber the U.S. Navy as early as 2020, and has nearly achieved numerical surface combatant parity today. Most dangerously, between 2025 and 2035, the U.S. Navy’s ship numbers will hover between 310 and 320 – such a disparity increases potential instability Absent a colossal shipbuilding program, the U.S. Navy’s only hope for parity will involve transferring the vast majority of American combat power to the Pacific, while easing force commitments elsewhere. Turning Indian Ocean and Arabian security over to the Indian Navy, in return for American guarantees to protect shared Indo-American interests in the South and East China Seas, may therefore be a preferable solution. At a minimum, the U.S. should consider joint basing arrangements with Indian facilities in the Southern and Western Indian Oceans, replicating the Royal Navy’s commanding position in the Indian Ocean during the Second World War. Israel could also benefit from such an arrangement – its submarines could refuel and resupply from Indian bases, or Indian support ships, enabling more consistent presence on Iran’s southern flank.
Conclusion – Forging the Strategic Relationship
Seldom does the international environment explicitly conform to the goals of high policy. Sophisticated strategies can easily unravel when they encounter certain facts on the ground. However, this makes identifying the points where a state can exert its influence even more critical. The confluence of interests between Israel, India, and the U.S. creates such a situation. With proper American policy action, the U.S. can effectively further its interests in the Near East, Indian Ocean, and Western Pacific, and potentially build a lasting partnership that stabilizes critical regions stretching from Cyprus to Ceylon.
Harry Halem is an undergraduate at the University of St Andrews studying International Relations and Philosophy. He welcomes your comments at hh66@st-andrews.ac.uk.
Featured Image: Prime Minister Benjamin Netanyahu and his Indian counterpart Narendra Modi shake hands at a joint press conference in the president’s house in New Delhi, India, on January 15, 2018. (Avi Ohayon/GPO)