There’s been a big uproar lately about innovation in the Navy throughout message boards and the blogosphere – what is innovation, what it’s not, and what method Big Navy should be taking to jumpstart innovation among the fleet, if any at all. LT Jon Paris and LT Ben Kohlmann, both of whom are very involved in the conversation, had a great discussion about the topic on CIMSEC’s Sea Control Podcast, hosted by LT Matt Hipple. LT Paris followed up with an excellent blog post. While there are some contrasting views, it seems like one thing that’s agreed upon is that the deckplate innovation already occurring in the fleet sometimes doesn’t make it “up and out” or isn’t as publicized as it should be. In that capacity, LT Hipple, and some members from the CNO’s Rapid Innovation Cell, offered a challenge to start publishing examples of innovation in the fleet. I’ve decided to take this up head on in a series of “Innovation Files”.
Nearly every command has a “Plan of the Day” (POD) – a widely distributed one-page agenda with at least the current and following days’ schedule of events. Depending on the command, certain PODs are very long and many regularly contain dozens of events per day, some at overlapping times. Early on, I noticed a couple glaring inefficiencies particular to my command. First was the process – A yeoman would be specifically assigned to “do the POD” for the day, a duty rotated among the junior yeomen that nobody wanted. This task started by opening the previous day’s POD, changing the date, piling through various e-mails and files on the shared drive, and then writing the new daily schedule by hand. After an hour or two, it would get routed up to the ship secretary, personnel officer, admin officer, training officer, operations department, various department heads, command master chief (CMC), and some others before finally getting to the XO. Every position in the chop chain had their own changes and events to add, and it required the yeoman to literally go around the ship looking for each of these people, and then going back and correcting the changes for each correction or addition. It wasn’t uncommon to print in excess of 15 POD drafts before the final revision. As you can imagine, POD duties were an all-day event, and since the POD needed to be finalized and signed by the next day, it kept everybody around well into the evening.
After much thought, the XO, personnel officer, and I agreed on a plan to create a public calendar on Microsoft Outlook to streamline the POD process. However, PODs have a very specific format, and Outlook can print nothing close to the format. For example, asterisks had to be next to times if the event was to be announced on the 1MC, events had to be in bold lettering if the CO was attending, and everything had to fit on the page in two neat columns. It wasn’t as simple as hand-copying every single event into the old POD format though; the daily schedule constantly changed throughout the day, and there was no process in place to ensure if any late additions or modifications in Outlook were included in the POD. This, along with other human errors, severely complicated the process, and made it essentially as inefficient as the old method. If only there was a better way!
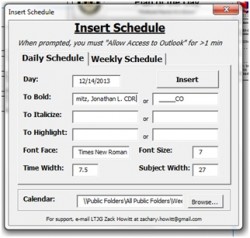
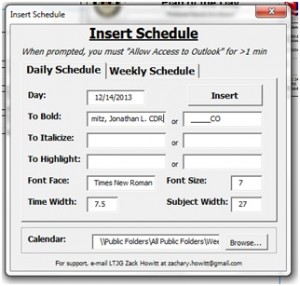 Introduce the automated POD (autoPOD). We decided to devise a macro app on top of Microsoft Publisher, a computer publishing tool, to automatically translate events on Outlook into the same easy POD format everyone was used to seeing. Macros are essentially programs, coded in easy-to-learn VBA (Visual Basic for Applications), that are built on top of application documents (in this case Publisher’s and Outlook’s) meant to automate tasks within these programs. Because of this attribute, it gets around IT policy requirements, which prohibit the introduction of specific executable programs not pre-approved by SPAWAR. Microsoft Publisher was chosen over Word because it’s specifically designed to manipulate documents with multiple dynamic text boxes. Through an appropriate script reference, the app asks the user permission to reach out to any designated public Outlook calendar. Then all the user has to do is click one button, and it automatically inserts the daily schedule into the POD publication – complete with dates, events, headers, etc. The layout is easily manipulated by different codes inputted into the appointment screen on Outlook. For example, for an event to appear “bold”, which indicates the CO is attending, an actual Outlook invitation for that appointment is sent to the CO, which is then designated on the user interface with a specific user name.
Introduce the automated POD (autoPOD). We decided to devise a macro app on top of Microsoft Publisher, a computer publishing tool, to automatically translate events on Outlook into the same easy POD format everyone was used to seeing. Macros are essentially programs, coded in easy-to-learn VBA (Visual Basic for Applications), that are built on top of application documents (in this case Publisher’s and Outlook’s) meant to automate tasks within these programs. Because of this attribute, it gets around IT policy requirements, which prohibit the introduction of specific executable programs not pre-approved by SPAWAR. Microsoft Publisher was chosen over Word because it’s specifically designed to manipulate documents with multiple dynamic text boxes. Through an appropriate script reference, the app asks the user permission to reach out to any designated public Outlook calendar. Then all the user has to do is click one button, and it automatically inserts the daily schedule into the POD publication – complete with dates, events, headers, etc. The layout is easily manipulated by different codes inputted into the appointment screen on Outlook. For example, for an event to appear “bold”, which indicates the CO is attending, an actual Outlook invitation for that appointment is sent to the CO, which is then designated on the user interface with a specific user name.

Along with events, the app supports all sorts of informational headers put in by different users through Outlook tags – for example, the operations officer puts in the appropriate command duty officers and duty sections, and the quartermasters put in sunrise and sunset times into Outlook. The app supports time structures displayed as “All Day” or “TBD”, and all types of recurring events. Different permissions (ie: read only, add, or modify/delete) can be granted to different users to modify the Outlook Calendar, and the program is set up for an administrator to view when and who is putting in the events, so it’s not possible to sneak a last minute evolution for the next day without the XO and CMC knowing.
AutoPOD was eventually customized for several other tasks. By request, we built an automated Plan of the Week (POW) 10-day printable outlook on top of Microsoft Excel for the Planning Board for Training (PB4T), which mimics the POD format each day, for planning purposes. Other ships had a weekly or monthly outlook summary with important events listed on the back of their POD, and autoPOD was customized for these commands as well, using the “priority” attribute to determine if the item should be displayed on a weekly summary. We have continuously refined AutoPOD to accommodate every ships’ POD format, meaning there will be little, if any, visible change to the Sailor. For example, there are options to 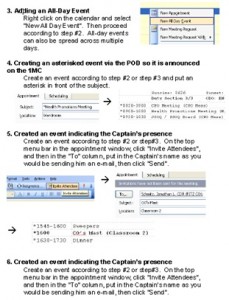 modify the font, size, and width for the time and subject columns. Additionally, it’s designed to be plug-and-play – all contained in one publisher file – so it can be used immediately and without any complicated installation procedures. Detailed documentation is provided on how to install the program and manipulate the schedule via Outlook.
modify the font, size, and width for the time and subject columns. Additionally, it’s designed to be plug-and-play – all contained in one publisher file – so it can be used immediately and without any complicated installation procedures. Detailed documentation is provided on how to install the program and manipulate the schedule via Outlook.
It is worth noting that the initial concept of autoPOD was not received well in its early stages. For example, the yeomen were used to a certain way of doing things, and didn’t want to move over from Word to Publisher. Despite comprehensive training, some department heads and department lead chief petty officers continued to send e-mails to admin with their events, instead of deconflicting and scheduling it themselves in Outlook. However, after much dedication and patience, everyone slowly acclimated. The new system is now second nature, and it’s hard to think of how life even functioned in the past.
To date, autoPOD has been distributed to over a dozen ships, across several waterfronts. It has undoubtedly made the POD process less frustrating, and has saved countless manhours and time, from the junior yeoman who can produce a POD in minutes, to the XO who no longer has to micromanage the process. Unfortunately, we recently hit a bump in the road when asked to set up the app on a ship that finished an extensive shipwide IT refresh known as a Consolidated Afloat Networks and Enterprise Services (CANES) installation. At the time, CANES strictly restricted ships from creating and using shared calendars, along with other security settings that prevented the app from working properly. A workaround is in progress, but it illustrates a point that has been brought up in the recent discussions – many Navy policies and procedures are around for valid reasons, but often come at the expense of productivity and innovation. It’s essential to collaborate between the fleet and appropriate project managers / designers / policymakers to figure out an optimal mix.
Zachary Howitt is a proud American, Naval Officer, and Tech Entrepreneur. He is a designated operations analysis subspecialist and has served in two warships forward-deployed to Yokosuka, Japan. His opinions and views expressed in this post are his alone and are presented in his personal capacity. They do not necessarily represent the views of U.S. Department of Defense, the U.S. Navy, or any command.


 Introduce the automated POD (autoPOD). We decided to devise a macro app on top of
Introduce the automated POD (autoPOD). We decided to devise a macro app on top of 
 modify the font, size, and width for the time and subject columns. Additionally, it’s designed to be plug-and-play – all contained in one publisher file – so it can be used immediately and without any complicated installation procedures. Detailed documentation is provided on how to install the program and manipulate the schedule via Outlook.
modify the font, size, and width for the time and subject columns. Additionally, it’s designed to be plug-and-play – all contained in one publisher file – so it can be used immediately and without any complicated installation procedures. Detailed documentation is provided on how to install the program and manipulate the schedule via Outlook.