
The following article is special to our International Maritime Shipping Week. While we often discuss the threats to maritime shipping, this week looks at dangers arising from such global trade, and possible mitigations.
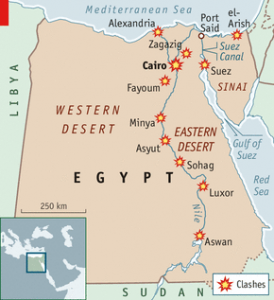
As months of massive opposition protests culminated on July 3, 2013 in a military coup against Egyptian President Mohamed Morsi, the eyes of the commercial maritime industry were fixated on the Suez Canal. Though the general report from the vital waterway is ‘business as usual,’ the political and security situation in Egypt remains incredibly fluid. In the restless Sinai Peninsula, militant groups have seized a perceived moment of weakness to launch a fresh round of attacks against Egyptian authorities. In the major cities, including those along the Canal, pro- and anti-Morsi demonstrations and security crackdowns have turned violent, resulting in hundreds of deaths. Military deployments have been increased in the Canal Zone, but the balance between security and efficiency is a delicate one.
As an exercise in speculative analysis, this article examines the questions of who might attempt to shut down the Suez Canal, while the second installment will assess how such an objective could be achieved. Of particular relevance for International Maritime Shipping Week, is the possibility that a vessel transiting the Canal might unwittingly become a pawn in a scheme to close it.
Potential Perpetrators
There is no shortage of local and regional groups hostile to Egypt’s interim military government. As the military’s legitimacy and public support is largely based on the relative stability it provides, an attack on the Suez Canal would serve to undermine and embarrass the interim government, demonstrating to the world that the military is unable to protect the country’s vital interests. That said, the integral boost that Canal revenues provide to the Egyptian economy—accounting for some 2.5% of GDP—makes it unlikely that a political actor with aspirations to govern the country, such as the Muslim Brotherhood, would publically seek to disrupt the Suez Canal.
Riding West from Sinai
Militants in the Sinai Peninsula—a mix of local Bedouins, Palestinians arriving from Gaza, and handful of foreign jihadists—have engaged in low-level conflict with the Egyptian state for decades, but have dramatically escalated their attacks since Morsi’s ousting. The targets of militant attacks are usually symbols of Egypt’s political and military authority in the Peninsula, including security checkpoints, police stations, administrative buildings and army camps. Militants have also struck at critical infrastructure such as oil pipelines to Israel and Jordan, power stations, and the airport at El-Arish. An influx of weapons looted from Libya and the function of Gaza as a smuggling hub has meant that Sinai militants are increasingly well armed, brandishing unguided missiles, RPGs, mortars, and guided anti-tank and anti-aircraft weapons.

As the Egyptian army attempts to crackdown on the militants, there are several indicators that Sinai insurgents may attempt to broaden their campaign and target the Canal Zone. On July 8, armed gunmen attacked the Port Said traffic police directorate and the city’s western seaport in a series of drive-by shootings that mirrored those seen in northeast Sinai. On June 25, a rocket fired from central Sinai landed in an empty area east of the Canal in what Egyptian officials speculate may have been a military drill by an insurgent group. It was also reported that another inaccurate rocket launch in early July was an attempt to hit oil installations in the city of Suez. In addition, Egyptian military sources claim that a cache of Iranian-sourced Fajr-5 rockets seized in Sinai on August 9 were part of a plot to attack Suez Canal facilities.
Forcing a closure of the Canal would be incredibly difficult, but options for disruption are many (see Part II). Regional security expert Ehud Yaari notes that even a lone jihadist in the Sinai could fire an anti-tank missile or RPG at a ship moving slowly through the Suez Canal. This would be unlikely to block the Canal, but may result in delays, increased insurance premiums, and demands for hazard pay for shipping companies.
An Escalating Circle of Political Violence
Two weeks ago, this author assessed that “there is a very low probability that the Muslim Brotherhood will abandon its current strategy of sit-ins and protests in favor of armed revolt against the military.” Recent events, however, have increased the likelihood of political violence spilling over into the Canal Zone. Clashes between Morsi supporters and security forces that left some 80 dead on July 26 were in fact only a preview of the carnage witnessed on August 14, when a police effort to clear protest camps in Cairo was backed by army units firing automatic weapons and sniper rifles. By August 15, the Egyptian ministry of health had recorded 525 dead, but other estimates put it hundreds higher. This event is likely to prove a watershed moment for Egypt and has already resulted in violent blowback from Brotherhood supporters.
Egypt’s interior ministry claims that 43 policemen were killed during the clashes, four of them captured and summarily executed in the village of Kerdasa near Cairo. Muslim Brotherhood supporters stormed government buildings in Cairo and Suez city, while violent mobs also set fire to some 18 Christian churches across the country.
Now facing an imposed nighttime curfew and state of emergency declaration, the official line from the Muslim Brotherhood leadership is to continue with demonstrations and marches. “We will rise and rise again until we push the military back into the barracks and restore democracy,” tweeted Brotherhood spokesman Gehad El-Haddad.
The longer this cycle of protest and repression continues, the harder it will be for the Brotherhood’s leaders to prevent its members from engaging in violent acts. There are reports that some Islamists have fled mainland Egypt to join the insurrection currently waged in the Sinai. Other protest groups have threatened to block roads and railways, and attack security directorates and public facilities if the military continues to break up sit-ins or gatherings. These types of actions will have a direct effect on Canal operations. GAC Egypt, a shipping service provider, recently recommended that transiting vessels suspend crew changes and logistical deliveries until further notice.
The worst-case scenario for the Suez Canal would be if individual Islamists become so frustrated with the Egyptian government that they resort to economic destabilization by disrupting the Canal. It is also possible that continued military violence against Islamist protestors could lead other political groups, such as the Salafists (ultra-conservative Islamists), to abandon mainstream politics in favor of armed conflict. If such groups flee the political system, it could equate to targeted attacks against the backbone of the Egyptian economy: the Suez Canal, the Suez-Mediterranean (SUMED) oil pipeline and tourist centers.

Eyes on the Canal
Though Canal traffic remains normal, the political violence that has spread to the Canal cities of Port Said, Ismailia and Suez is of great worry for the Suez Canal Authority (SCA) and Egypt’s military government. Reinforcements from the army, navy, and air force have been sent to secure the entire length of the waterway. There are also unconfirmed reports that the SCA raised the Canal’s security level to “extreme emergency” following the August 14 massacre. The exact nature of this perceived threat—including possible targets for attack and potential impacts of worst-case scenarios—will be the focus of this briefing’s second installment.
This article contains excerpts from the Delex Maritime Analysis Center’s “Suez Canal Security Tracker” series, co-authored by Delex analysts James Bridger and Jonathan Zinger. For more information about this product offering, please contact jbridger@delex.com





