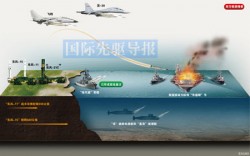
After months of patient progress the drones reached their targets. Over the span of a few weeks they silently arrived at their pre-assigned loiter boxes (lobos) in the many harbors of Orangelandia. Having been launched from inconspicuous commercial vessels in major shipping lanes, the transit time was shortened by a good month. Yet for the few who knew of the operation, the anxious waiting was plenty long enough. The policy makers monitored the gliders’ headway via secure satellite datalinks and assured themselves that the operation, sold as a precautionary measure, was warranted in light of heightened tensions with Orangelandia.
As the weeks passed tensions only increase. Orangelandia declared its claimed EEZ closed to all foreign military vessels and threatened to sink any violators. After making good on its promise in a naval skirmish against a neighbor with rival claims to an island chain, Orangelandia was given an ultimatum by the U.N. Security Council* to stand down. With no sign of the occurring, the policy makers decide it’s time to act.
——
Darkness falls in Orangelandia. Satellites command the gliders forward. They drift further into the harbors, their targets are naval vessels they’ve monitored for days. The sailors on watch see and hear nothing more than what they attribute to the usual debris floating by on a moonless night. The gliders release their payloads – smaller drones that specialize in climbing the hulls of ships. After clamoring aboard the weatherdecks, the small machines avoid the sealed doors of the ships’ airlocks and feel out the superstructures, their goals the exhaust stacks for the ships’ engines and generators.
On a few ships at anchor the drones encounter humming engines and generators, beckoning the heat-seeking drones. Burrowing past the louvers the drones drop down through ducts and move towards the ships’ mechanical hearts. As the heat of the exhaust on the active vessels melts the drones’ exterior sheathing, thermal-triggered explosives carried in the drone cores detonate, delivering mission kills and rendering the ships immobile for weeks-to-months of critical repair. On the inactive ships it takes longer for the drones’ schematics-recognition features to determine the stacks’ location but the outcome is more devastating. The drones are able to move further into the exhaust system’s interior, detonating once progress is blocked, and increasing the likelihood of destroying the engines or generators themselves. Within the span of a night the majority of Orangelandia’s in-port fleet is crippled.

The above passage is of course a piece of fiction, and not very good fiction at that. But it doesn’t have to be. The technology to enable the scenario exists and will become more sophisticated and cheaper in the coming years. This is also far from the only way to imagine a “Drone Pearl Harbor,” as slightly different capabilities hold the potential to impact the way an attack could play out.
Decision points
In developing a concept of operations for a stealth drone attack the ability to give the execute order is a sticking point. The technologically easiest course of action would be to simultaneously make both the decisions to set up for and to execute the strike at the beginning of the decision cycle, launching the drone operation as a “fire and forget” (or rather “fire and wait patiently”) strike. Yet few policy makers will want to make an irreversible decision far in advance of the impact of the effects. The decision to attack Orangelandia may be correct in the context of the 7th of the month, but not the 21st. One needs only remember the desperate attempts to recall the nuclear-armed bombers of Dr. Strangelove to grasp the concept.
However, any attempt to move the “execute” decision point later than the “set up” order, as I did in my example, faces technical hurdles. A direct transmission signal requirement would make the drones vulnerable to detection and possible hijacking or jamming. Using broadcast signals to transmit orders and obscure their location means leaving the drones even more susceptible to hijacking and jamming as Orangelandia could constantly emit signals to that end. Similar vulnerabilities exist when the drones are given reporting requirements, so an informed balancing of the need for one- or two-way communication and concerns over the exposures those needs create is necessary.
Variations on a Theme
The above scenario was played out against a generic surface ship. Other types of naval vessels have more accessible points of entry; and the job of penetration is made easier at less-stringent damage control settings that leave hatches and air locks open. Additionally the ways, means, and follow-on considerations of a drone sneak attack are also variable, but can be roughly broken down into fouling attacks, as in the scenario above; direct attacks; and cyber-attacks.
In a fouling attack, the drone payload would be used to achieve a mission kill against a critical piece of shipboard equipment. The drone would need the ability to locate that piece of equipment through some type of sensor – visual, thermal, chemical, etc. External targets, such as a ship’s propellers, would be the easiest to target. The benefit of a fouling attack is that the payload could be a small explosive, limiting drone’s size, likelihood of detection, and propulsion requirements for a trans-oceanic voyage. It could even be the drone itself, outfitted with special equipment or configuration options to inflict the maximum damage on the piece of critical gear. As an example imagine a piece of corrosive wire wrapping itself around the same hypothetical propeller. Again, the execute order in this type of attack could be withheld until very late in the decision-making process while the glider drones do “circles of death” in their lobos.
In a direct attack the glider drone would carry a weapon payload designed to inflict maximum kinetic damage. Such an attack would require less sophisticated targeting internal to the drone and could be used to attempt to disable a large portion of the ship’s crew and/or sink the ship. As with fouling attacks, direct attacks would be easier to conduct once the glider was on station and could incur the same delayed-decision benefits, the increased explosives requirement would increase the drone’s size and detectability.

In the last type of attack, a payload drone would find a way to penetrate the ship and access the ship’s industrial control systems (ICS), which operate things such as the ship’s main engines, to introduce a Stuxnet-like virus. Such drone would need to be small enough to fit through minuscule spaces or blend in during the process of crew traffic opening and shutting airlocks. The drone would also have to be the most advanced to successfully navigate around the ship unseen and interface with ICS through diagnostic, patching, or external monitoring ports. Such a drone could delay the policy-maker’s execute order until well after infection, potentially expanding the decision timeline until well after the drone has achieved its mission and the vessel has gotten underway. This delay would come at the cost of the very difficult task of being able to transmit the final execute order to the newly infected ICS, so the decision to infect the systems would more realistically have to be paired with the decision to execute virus’s programming. On the plus side, a cyber/drone sneak attack could potentially disguise the source of the attack, or even that an attack has occurred, unlike the other two types of attack, providing policy makers with further options than simply a kinetic attack.
That these courses of action are possible says nothing of whether executing any of them would be wise. The risk and potential repercussions of each course of action is as varied as the ways in which such an attack may occur. This is one reason I have attempted to draw out the effects different technologies have on moving the decision points. But possible they are, so it would be wise to both think of ways to take advantage of the options as new tools for policy makers, and think of ways to defend against them that don’t rely on weary roving deck watches. A few defensive options that come to mind include more stringent damage control settings in port, a thorough examination of the vulnerability of vessels and shipboard access points to drone penetrations, detection systems for drone penetrations, drone SIGINT detection and jamming, and possible external hardening of berths. But this is probably a good jumping off point for another post and your thoughts.
Scott Cheney-Peters is a surface warfare officer in the U.S. Navy Reserve and the former editor of Surface Warfare magazine. He is the founding director of the Center for International Maritime Security and holds a master’s degree in National Security and Strategic Studies from the U.S. Naval War College.
The opinions and views expressed in this post are his alone and are presented in his personal capacity. They do not necessarily represent the views of U.S. Department of Defense or the U.S. Navy.
*So no, Orangelandia is clearly not China, a veto-wielding member.