Read Part 1 on defining distributed maritime operations.
Read Part 2 on anti-ship firepower and U.S. shortfalls.
Read Part 3 on assembling massed fires and modern fleet tactics.
By Dmitry Filipoff
Introduction
Modern naval combat can consist of forces firing dozens if not hundreds of missiles at one another’s fleets and salvos. These volumes of fire can be unleashed within mere minutes as forces look to launch offensive and defensive salvos that are large and dense enough to kill and defend warships. Yet these sophisticated weapons are available in limited numbers and require long lead times to produce.1 Only a fraction of these inventories are available for immediate use given how the magazines of the operating force’s platforms are distinct from the weapon stocks they draw from. Militaries can be limited to using the weapon stocks they had shortly before conflict broke out, and a short conflict may be decided by what was mainly fielded in platform magazines. Unless the conflict becomes especially prolonged and the industrial base grows significantly, the inventory of precision weapons will steadily diminish and pose critical constraints. A core operational challenge is how to carefully manage weapons depletion while still unleashing massed fires.
Weapons depletion is in its own right a powerful force for shaping warfighting behavior and securing major operational advantage. The larger consequences of depletion can include steep decreases in unit availability and overall operations tempo on a theater-wide scale. This challenge is especially severe for the U.S. Navy given how long it would take a depleted U.S. warship to travel out of a Pacific battlespace, rearm in safe havens, and return to the fight.2 In a short, sharp conflict featuring intense salvo exchanges, a warship that depletes itself only once may very well miss the rest of the war.
The concentration and distribution of a force will flex and evolve as its platforms suffer depletion. As commanders look to employ mass fires, they must be mindful of how to spread depletion across the force, how to interpret the adversary’s expenditures, and how inventory pressures can be manipulated through the last-ditch salvo dynamic.
Distribution and Depletion
One of the critical advantages of massing fires from distributed forces is the ability to more effectively manage depletion. A distributed force fielding a vast array of overlapping firepower makes for an especially large and shared magazine. This offers a much greater chance of mustering enough firepower to overwhelm robust defenses while achieving a better spread of depletion. Depletion can be spread across a broader scope of platforms and occur more gradually across the force, rather than all at once for individual strike platforms and force packages. Spreading depletion prolongs distribution, because every depleted asset makes the remaining force less distributed and more concentrated.
Some platforms and force packages certainly have sufficiently deep magazines to launch large enough volumes of fire on their own, with less of a need for outside contributing salvos. But large standalone salvos diminish a core tenet of distribution – maintaining many spread out threats to complicate adversary targeting. Forces that fire large standalone salvos can quickly give away that they just depleted most of their offensive firepower, reducing their value as targets and diminishing the distribution of the broader force.
The more a platform has to discharge a large number of missiles to contribute fires, the more easily an adversary can ascertain the composition and depth of their remaining inventory. A U.S. destroyer that fires 30-40 Maritime Strike Tomahawks in a single large salvo can give away that it has little remaining long-range anti-ship weaponry. By comparison, massing fires from a broader array of distributed forces makes it harder for an adversary to ascertain when platforms and formations have depleted their individual magazines.
Aggregation allows firepower to be combined in smaller portions from individual launch platforms. Ideally each launch platform can afford to expend only a small fraction of its magazine at a time, if many other platforms are doing the same with proper timing and coordination. Individual platforms will be able to sustain distributed offensive threats for longer than if they had fired off large, independent salvos of their own.
However, as inventory begins to dwindle across a distributed force, mass fires can cause larger portions of the force to reach the end of their magazines around a similar timeframe. This could radically collapse the offensive posture and capability of the distributed fleet if not carefully managed. By delaying magazine depletion at the individual platform level, mass fires risk magazine depletion across a broader portion of the force at a later time.
Consider a fleet that has four distributed warships available for contributing fires. If one warship emptied its entire offensive inventory per strike, then the remaining force becomes increasingly concentrated and predictable as to where the next several strikes may come from. Instead, if those four warships combine fires to launch a quarter of their offensive inventory per strike, the distributed force posture endures for more time and across more attacks. But all of those warships would deplete at a similar time, triggering a larger drop in force distribution compared to depleting only one platform per strike through the first scheme. By spreading depletion to prolong distribution, mass fires trade smaller decreases in distribution earlier in the fight in exchange for larger decreases later on.
Having deeper magazines or more strike platforms reduces the share of magazine depth each attacker must deplete to contribute to mass fires, and further delays the broader depletion of the force. A distributed force posture can be preserved by having a large number of assets with overlapping firepower, or rotating assets quickly enough to replace those that have depleted their magazines. The goal is to maintain enough available firepower over time so the distribution of the force can endure.
Asymmetric Weapons Depletion and Operational Risk
There are important asymmetries in how warships can deplete their offensive missile firepower versus their defensive firepower. One asymmetry is that commanders may be deeply uncomfortable keeping large surface warships in the battlespace when they are low on defensive firepower but fuller on offensive firepower compared to the reverse situation. Another key asymmetry is that defensive firepower is mostly drawn from the local magazines of the naval forces under attack, while offensive firepower can be drawn from the many magazines of a broader distributed force. Leveraging these key asymmetries can secure operational advantage.
Even if a ship survives an intense attack, being on the wrong side of firing effectively first can take the form of being low on defensive firepower while still full on unused offensive firepower. These units can still remain offensive threats, but the volume of fire required to overwhelm their defenses is substantially lowered. This can force commanders to pull these units out of the fight for the sake of survival and replenishing their defenses.
In this sense, firing effectively first is not only defined by scoring successful hits and kills, it can also mean depleting enough of the adversary’s defenses that commanders no longer feel confident in pressing their attack or maintaining warships in a contested battlespace. If those depleted warships are in escort roles and are responsible for defending other ships, then those ships could be forced to withdraw as well. By depleting defensive firepower to the point that warships must be withdrawn before they can attack, those warships’ offensive inventory can be removed from the fight before it can be used, thereby suffering depletion indirectly.
The battle of nerves in naval salvo warfare is partly a function of accepting risk for the sake of minimizing weapons depletion. A more efficient missile exchange tolerates more risk, demanding stronger nerves on the part of commanders. Otherwise, the desire to build more confidence into offensive or defensive engagements can make commanders waste their munitions. A defending warship that fires too many anti-air weapons per incoming missile wants to bolster its odds of near-term survival, but it can deplete itself earlier than warranted and increase risk in follow-on engagements. A warship that fires an excessive amount of anti-ship weapons can risk too much overkill and leave it with little offensive capability for later in the fight.
But commanders who attempt to precisely optimize their offensive salvos in a bid to just barely overwhelm targets with enough fire will risk much greater uncertainty than those willing to accept overkill by expending more volume. Indeed in a form of combat featuring salvos with dozens of missiles that only need to strike a single hit, overkill is more likely than not. Instead, it is the degree of overkill that separates what is sufficient from what is wasteful. Achieving a small degree of offensive overkill can be the more efficient outcome, since attacking with an insufficient volume of fire can lead to waste by making follow-on salvos once again pay the price of breaking through strong defenses to threaten a target. With too much overkill, a unit or commander witnessing a heavy volume of fire pouring into a dead or dying friendly warship may take some small satisfaction in knowing the enemy just suffered depletion far out of proportion to their target.
A key asymmetry is how the risk of depletion through overkill is much more manageable for offensive fires because of the greater ability to mass those weapons from across many forces. Defensive inventory has far less margin to work with because of the isolating effect of the radar horizon on ship self-defense, where there is little ability for ships to leverage a broader shared magazine against sea-skimming threats. An attack on a naval formation can consist of fires pulled from a wide variety of forces, but the formation will often have only its own magazine to defend itself. And with that magazine, the formation may not only have to match the incoming volume of fire, but exceed it to ensure survival. Matching the attacking volume with only one interceptor fired per incoming missile may not be enough to confidently survive a dynamic where a warship cannot afford to take a single hit, yet the attacker can afford to have every attacking missile take a hit except one.
For defensive volume of fire, there can be a thin line between what is sufficiently dense and what is wastefully excessive. Firing just one more interceptor per incoming missile can dramatically increase expenditure in a single engagement and result in a warship facing follow-on threats with a far more depleted magazine. But as mentioned, defensive depletion not only increases risk to the individual platform, it threatens to take that platform’s offensive fires out of the fight prematurely. The broader offensive inventory that is available for massed fires can therefore be threatened by the localized manner of defensive engagements and their especially depleting nature.
Range advantages convert to depletion advantages, where forces with longer-ranged weapons can inflict asymmetric depletion against their shorter-ranged opponents. These threatening dynamics are more probable for navies that can be up against anti-ship weapons with much greater ranges than their own, such as the current range disparity the U.S. Navy is suffering against many Chinese anti-ship missiles.
If two opposing forces have a major disparity in the range of anti-ship weapons, then the forces with less range can be forced to travel hundreds of miles while under fire before they can finally be in a position to attack. These warships can be depleting their defensive firepower while still pressing forward in an increasingly risky bid to bring their offensive firepower to bear. By comparison, the longer-ranged side will deplete far fewer defenses to make their attacks, if they have to deplete those defenses at all. Warships with a significant offensive range advantage are not only in a much better position to fire first, they can fire their salvos and then simply reverse course to keep themselves out of reach while preserving their defensive firepower. The outranged fleet can be pressing forward without much of its defensive firepower left, while the other fleet can be in the much more comfortable position of pulling back with most of its defensive firepower remaining. It is unlikely that the fleet with shorter-ranged weapons would be in a position to catch up to the opposition in many circumstances. Because of the vast distances involved and the large speed differential between anti-ship missiles and warships, it seems improbable that surface warships will run each other down on the open ocean in the age of missile warfare.
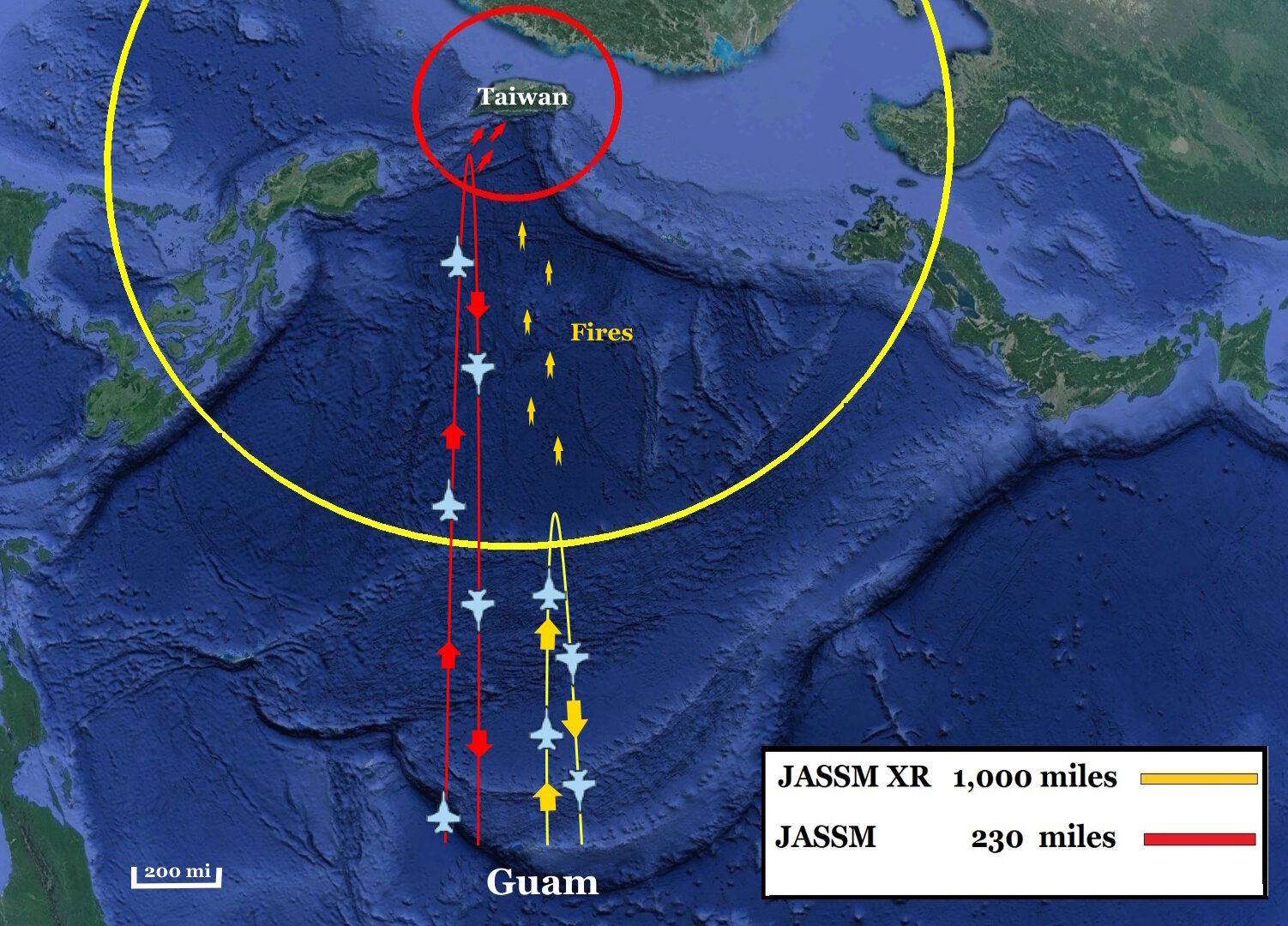
Increased payload range can also translate into increased reload speed, where shifting more of the burden of maneuver onto the payload shortens the logistical lifeline of the platform. The longer the range of the weapon, the less the platform has to travel between its launch areas and rearmament points, shortening the episodic drops in force distribution while offering higher rates of fire. This effect is especially potent for aviation, such as how aircraft firing JASSMs at 230 miles can have much lower reload rates and availability of fires compared to aircraft firing the 1,000-mile extreme range variant of JASSM (Figure 1).3 An asymmetry in weapon range between opposing forces can translate into asymmetry in reload speeds, and make the distribution of a force more resilient against depletion than its adversary’s.
Massed Fires and Uneven Depletion Across Platform Types
As waves of massed fires ensue, the distribution of depletion across the platforms of a force can become uneven. A distributed force may prefer to prioritize its longest-ranged fires, its most common weapons, or other payloads for other reasons, which depletes the specific platforms that launch them. This sets the stage for operational tradeoffs and an evolving risk profile, since one type of platform’s fires can preserve the inventory of another’s, and different platforms have different magazine depths and timeframes for reloading. Uneven depletion can gradually shift the burden of massing fires onto platforms that must assume more risk to continue the fight, encouraging a force to carefully consider how to distribute weapons depletion across platforms over time.
The anti-ship Tomahawk will offer long range and broad magazine depth across many platforms, making it an ideal weapon for massing fires. But heavily prioritizing the use of the anti-ship Tomahawk can make surface forces and submarines among the first to deplete their anti-ship missile inventories, and where these platforms can take many days to reload and return to the fight. The weapons that can contribute the most to mass fires can suffer the most depletion, putting the distribution of the force at risk down the line.
As the fight continues and warships become more depleted, more of the U.S. burden of assembling mass fires against warships can gradually accrue to aviation because aviation can reload much faster than warships. This is especially true for carrier air wings, and carriers have the deepest magazines of all afloat combatants, potentially making them the last warships standing when it comes to remaining inventory after intense exchanges.4 Yet this would pose an especially concentrated posture to an adversary and force air wings to take major risks in deploying the remaining firepower. Preserving the anti-ship inventory of warships is therefore critical in forestalling a need to rely more heavily on aviation-based strikes, which would tie down numerous aircraft to muster volume of fire, pull carriers deeper into the battlespace, and assume more risk.
Yet this relationship is paradoxical. Preserving warship-based inventory can also take the form of leaning more on aviation fires earlier in the fight. Therefore a balance can be defined between the proportion of fires to come from different platform types at different phases of the fight, in order to manage how the risk profile of depletion evolves. A commander that carefully balances a combination of air wing depletion and warship depletion earlier in the fight can better delay the prospect of air wings shouldering more of the burden. Or a commander could heavily favor bombers in the opening phases, which can preserve warship-based fires for later phases, which preserves carriers. Depletion does not necessarily mean firing options have to get far worse as time goes on, depending on how commanders balance risk with regard to what combinations of launch platforms they favor depleting at different periods of the fight.
Submarines offer one of the most critical advantages in managing depletion through the highly favorable tradeoffs that come with sinking ships with torpedoes instead of missiles. The undersea domain is far less saturated with warship defenses compared to above the waterline. The cost of a missile salvo large enough to credibly threaten a group of several warships could easily exceed $100 million and require expending dozens of missiles.5 Credibly threatening the same group would require only several torpedoes, which could cost ten percent or less of the missile salvo.6 A single lethal torpedo strike can substitute for the dozens of missiles that could be required to overwhelm the same warship from above water.
By sailing far into contested littorals and laying near ports, bases, and maritime chokepoints, submarines are much more likely to be in a position to sink ships with fuller magazines compared to other platforms and deprive the adversary of inventory. However, closing the distance for torpedo strikes increases risks to submarines. The operational implications include weighing tradeoffs in the amount of risk commanders are willing to accept for their valuable submarines, versus the risk that could be incurred by depleting the broader missile magazine of the distributed force. Risking submarines in torpedo attacks can spare broader missile inventory and vice versa.
Aircraft and ground-based launchers certainly carry far fewer missiles per loadout compared to a large surface warship. Their shallower magazine depth substantially shortens the interval between launching fires and reloading, even if each of their fires is limited to a few missiles. But these platforms can typically access weapons stocks to rearm at a fraction of the time it takes a warship to do the same. Their shallow magazine depth can make their availability for fires more episodic than warships, but their episodes of depletion are not nearly as steep or prolonged. Land-based forces in the form of Chinese launchers on the mainland would have particularly more endurance than expeditionary stand-in forces that heavily depend on lengthy logistical lifelines to sustain their fires in a long fight.
The nature of uneven depletion will make for especially challenging command decisions. Commanders may face pressure to maintain depleted assets in the fight for the sake of posing some semblance of a distributed posture to the adversary. Commanders weighing such decisions would have to consider whether the adversary’s tracking of expenditure may have been accurate enough to provide the critical insight that portions of the distributed force are depleted. Operational behavior may significantly change based on one’s estimate of an adversary’s depletion and if asymmetric depletion has emerged between opposing forces.
Tracking adversary depletion is a critical operational imperative, but the desire to understand the specific composition and volume of missile salvos can place major demands on ISR and decision-making. Forces may struggle to distinguish between different types of anti-ship or anti-air missiles at long range and in the midst of battle. But knowing the type of launch platform narrows down the potential type of fires, where the tracking challenge is simplified by how certain weapons are exclusive to certain kinds of platforms. An F/A-18 firing on a warship is most likely firing Harpoons or LRASMs, and a Chinese warship firing on a ship is most likely firing YJ-83s or YJ-18s. Weapons that have longer range and are compatible with a broader variety of launch platforms will complicate the adversary’s ability to track expenditure and form estimates of depletion.
Defying Destruction and the Last-Ditch Salvo Dynamic
The adage of “firing effectively first” may be better described as striking effectively first, since two opposing naval formations can still destroy each other even if one fires after the other. In defining what it means to fire effectively first, an ideal kill of a warship or platform can include putting it out of action before it had a chance to use its offensive firepower. Similar to how it would be ideal to destroy a carrier while it is still embarking its air wing, it is ideal to destroy a warship before it has depleted its magazine of offensive missiles. This creates profound psychological and operational pressures that come into play when commanders of individual platforms and formations feel on the cusp of being destroyed. The critical phenomenon of last-ditch fires can threaten to destabilize distributed fleets and massed fires.
Commanders can be extraordinarily pressured to unleash most if not all of their offensive firepower if they believe there is a real risk of imminent destruction. Once a ship or fleet realizes that a potentially fatal salvo is incoming, enormous pressure can quickly force commanders to discharge their offensive firepower soon or else risk losing it permanently. Similar to how a carrier commander would be tempted to launch the air wing before the salvo hits the carrier, warships can make similar decisions with their missile magazines.
Last-ditch salvos are meant to deny the enemy one of the most critical benefits of firing effectively first. Launching a last-ditch salvo right before ships could be destroyed gives those offensive weapons a final chance of somehow contributing to the fight and deprives the adversary the benefit of sinking ships with fuller magazines. Last-ditch fires aim to ensure that archers are never destroyed before they can fire arrows. Concerns over losing limited weapons inventory are sharply intensified by lethal inbound salvos, making the last-ditch salvo a critical protocol for making the most of friendly losses moments before they are incurred.
A last-ditch anti-ship salvo cannot be an act of self-preservation. Commanders can be completely confident that an incoming salvo is dense enough and capable enough to overwhelm their defenses and destroy their warships. Launching their own anti-ship salvo in response is not going to change such an outcome. Anti-ship missiles cannot save warships from anti-ship missiles that are already incoming. These weapons can only save warships from anti-ship missiles that have yet to leave their magazines.
Many platforms that can threaten warships with anti-ship missiles cannot be threatened by those same missiles in return. This creates an asymmetric dynamic where some forces can enhance the effects of distribution by threatening to trigger last-ditch salvos that are futile. Since airborne aviation, submarines, and land-based forces cannot be directly attacked by anti-ship missiles, a warship launching a last-ditch salvo could very well be firing at perceived targets it can do nothing against. Even a single incoming torpedo from a submarine attack could trigger a last-ditch salvo fired in futility. Warships must strive to maintain awareness of candidate targets they can actually threaten with last-ditch salvos if a fatal attack comes from a domain they cannot effectively retaliate in.
A last-ditch salvo may be fired despite a lack of quality targeting information, since the method of simply firing down a line of bearing suggested by the incoming attack may be more than enough for a desperate warship. But warships ideally need broader situational awareness to launch effective last-ditch salvos, and especially to know whether they are under attack by a last ditch salvo themselves. If a warship does not recognize it is facing down a last-ditch salvo and simply reciprocates the attack, it could be firing on a warship with an empty magazine or even a warship that was already destroyed minutes earlier. This is even more wasteful than firing on a depleted warship, and a worthy result for warships whose final actions caused an adversary to waste precious firepower.
Last-ditch salvos are therefore a double-edged sword. This desperate act is meant to prevent precious weapons inventory from being permanently lost, yet this desire can be manipulated to prompt wasteful fires. An adversary can be made to take self-defeating actions in the crucial battle of nerves that infuses salvo warfare.
The simple appearance of an inbound volume of fire can be enough to trigger last-ditch firing protocols. Weapons with longer range and waypointing ability will have more opportunity to feint attacks on the way to their true target, multiplying the combat potential of salvos. If a weapon has enough range, attacking salvos may be waypointed to appear to threaten multiple targets in succession and provoke last-ditch fires from each (Figure 2).
Figure 2. A waypointed salvo triggers last-ditch fires from multiple formations by feinting attacks along the way to its true target. (Author graphic via Nebulous Fleet Command)
The U.S. may eventually have a substantial advantage in this regard by fielding a cruise missile with especially long range. The Tomahawk has enough range to where a salvo can threaten multiple naval formations through waypointed feints, even if those formations are distributed across hundreds of miles. If several Chinese naval formations are concentrated within 300 miles so they can mass YJ-18 missiles, then it becomes even more feasible to waypoint Tomahawks to trigger last-ditch fires within this radius. If one side’s naval formations have to concentrate within shorter distances to mass their fires, they become more susceptible to this waypointing tactic than their opponents, and they may not even have the range to launch viable last-ditch salvos at all.
Salvos used to trigger last-ditch fires may have to risk a degree of attrition by allowing themselves to be seen by warships. Networked missiles could coordinate pop up maneuvers to rise above the horizon and make themselves known, but only briefly enough before they can be struck by defensive fires. Otherwise the salvo could suffer enough attrition that it loses both its psychological and kinetic potency. Decoy weapons that can project the signatures of multiple aerial contacts, such as the ADM-160 MALD, can be used to inflate the appearance of mass while reducing the ability of defensive fires to chip away at the salvo.7

Posing the appearance of significant mass may not be a hard requirement for inducing last-ditch fires from a target. There may be a significant disparity in the volume of fire required to actually kill a platform, versus the volume of fire that is enough to manipulate it into firing prematurely. This disparity can stem from commanders being uncertain about the capability of enemy salvos or their ability to defeat them, or the strain of combat operations taking its toll on decision-making. The last-ditch dynamic can therefore magnify the tactical value of salvos that lack enough volume of fire to destroy targets. Commanders that are limited to local awareness may struggle to differentiate between a small salvo that was only launched as a standalone attack, versus a small salvo that is a harbinger of incoming mass fires. A small salvo can leverage these uncertainties to score outsized tactical benefit by triggering last-ditch fires despite not being able to actually threaten the target.
Even if a salvo cannot strike a target due to limited range or other constraints, it may still provoke emissions, signatures, and other reactions that could be exploited. Commanders may struggle to distinguish between different types of incoming missiles in real time, where last-ditch salvos consisting of low-capability, short-range, or non-anti-ship weapons can still manipulate reactions. A warship launching a last-ditch salvo could certainly fire its land-attack cruise missiles toward an enemy warship, who either can’t tell the difference or won’t take the chance. The prospect of wresting any sort of non-kinetic benefit can encourage platforms under heavy attack to launch last-ditch salvos regardless of capability or volume of fire.
And non-kinetics can prompt last-ditch fires themselves. Actions such as heavy jamming, blinding attacks against networks, aggressive posturing, and other methods that could be interpreted as a prelude to an imminent attack could also provoke last-ditch salvos. Last-ditch fires can be triggered by much more than just other fires.
The act of firing last-ditch salvos is extremely sensitive to timing given how warship launch cells are often carrying both offensive and defensive firepower, and how some cruise missiles require a minimum amount of lead time to be programmed for launch.8 A warship under attack from a subsonic anti-ship missile fired at a range of 250 miles has barely more than 20 minutes to react. And this assumes the target warship has knowledge of the launch. If the warship becomes aware of the incoming salvo only after it crosses the horizon, it can have roughly two minutes or less to prosecute an intense anti-air engagement while simultaneously discharging the whole of its offensive firepower in a last-ditch salvo. Those final moments would be characterized by an intense outpouring of the ship’s firepower in all-out offensive and defensive warfare. But these vast volumes of firepower would be bottlenecked by the rate of fire, of how many missiles can be fired by a warship’s launch systems in short periods of time. The volume of outgoing offensive and defensive firepower would be diminished as missiles of both types are primarily being fired from the same sets of launch cells, making them compete with each other for brief launch windows.
These challenges can be mitigated by having situational awareness over sea-skimming spaces that go beyond the radar horizon of a warship. Aircraft can provide early warning of incoming salvos and help warship commanders determine whether they must initiate a last-ditch salvo. Effective warning can allow commanders to discharge their last-ditch salvos early enough so that offensive missiles are not competing with defensive missiles for launch windows when it comes time for the warship to defend itself. In any case, warship commanders should strive to have a variety of pre-programmed responses at the ready so they can initiate last-ditch fires as fast as possible, and to have the subjective tactical judgement to know when it is time.
Warships under attack could be forced to fire their final salvos alone and in isolation from the broader distributed force. Yet last-ditch salvos may hardly be enough on their own to overwhelm concentrated defenses. This can put pressure on other combatants and commanders to add contributing fires in the hopes of growing enough volume to credibly threaten targets. A cascading domino effect could threaten to unravel a distributed force’s firepower as last-ditch salvos prompt hasty contributing fires from other platforms. The pressured nature of last-ditch salvos will exacerbate the timing challenges associated with combining fires and potentially rule out a variety of options for growing the volume of fire.
A commander of a distributed force must weigh the risks of attempting to combine fires with a last-ditch salvo. A last-ditch salvo may force a commander’s hand in adding contributing fires to a salvo that was fired on insufficient targeting data, lacks the volume to penetrate defended targets, or features other deficiencies. A commander could hold off on launching contributing fires, conserve the inventory of weapons, and allow the last-ditch salvo to play out on its own. But this may come at the risk of failing to support a salvo that could have effectively put opposing warships out of action if it had received just enough outside fires to tip the scales and cross the thresholds needed to overwhelm defenses. Commanders have to be ready to weigh these options as missile exchanges unfold in real time, and decide if a last-ditch salvo should remain a standalone attack, or leverage it through adding contributing fires.
Conclusion
As distributed forces unleash massed fires against one another, their desire to decisively overwhelm the opposition will be tempered by the need to minimize depletion. Depletion can threaten to break naval operations and yield major advantage to an adversary. Effectively massing fires from distributed forces can help manage depletion, but the need to achieve overwhelming volume of fire will make this risk a pervasive consideration at all levels of warfare.
Part 5 will focus on missile salvo patterns and maximizing volume of fire.
Dmitry Filipoff is CIMSEC’s Director of Online Content and Community Manager of its naval professional society, the Flotilla. He is the author of the “How the Fleet Forgot to Fight” series and coauthor of “Learning to Win: Using Operational Innovation to Regain the Advantage at Sea against China.” Contact him at Content@Cimsec.org.
References
1. For weapon production lead times, see:
“Department of Defense Fiscal Year (FY) 2023 Budget Estimates,” Navy Justification Book Volume 1 of 1 Weapons Procurement, Navy, Page 2 P-1 Line #7, (PDF pg. 94), April 2022, https://www.secnav.navy.mil/fmc/fmb/Documents/23pres/WPN_Book.pdf.
Seth Jones, “Empty Bins in a Wartime Environment: The Challenge to the U.S. Defense Industrial Base,” Center for International and Strategic Studies, pg. 14, January 2023, https://csis-website-prod.s3.amazonaws.com/s3fs-public/2023-01/230119_Jones_Empty_Bins.pdf?VersionId=mW3OOngwul8V2nR2EHKBYxkpiOzMiS88.
2. For one example, a warship on a one-way trip and traveling at 20 knots would take nearly two weeks to reach the Philippine Sea from U.S. naval infrastructure in San Diego. This assumes a straight line path, which may be less realistic under wartime conditions.
3. For JASSM range, see:
“AGM-158 Joint Air-to-surface Stand-off Missile (JASSM),” U.S. Air Force, https://www.af.mil/News/Art/igphoto/2000420243/.
For extreme-range JASSM variant, see:
Brian A. Everstine, “USAF to Start Buying ‘Extreme Range’ JASSMs in 2021, Air & Space Forces Magazine, February 14, 2020, https://www.airandspaceforces.com/usaf-to-start-buying-extreme-range-jassms-in-2021/.
4. Hon. John F. Lehman with Steven Wills, “Where are the Carriers? U.S. National Strategy and the Choices Ahead,” Foreign Policy Research Institute, pg. 67, 73, September 9, 2021, https://www.fpri.org/wp-content/uploads/2021/09/fpri-where-are-the-carriers-.pdf.
5. At an average unit cost of $3.5 million per missile, a combat credible salvo of about 30 LRASMs yields a volume of fire that costs in excess of $100 million.
For LRASM unit cost, see:
“Department of Defense Fiscal Year (FY) 2023 Budget Estimates,” Navy Justification Book Volume 1 of 1 Weapons Procurement, Navy, Page 1 of 10 P-1 Line #16, (PDF pg. 261), April 2022, https://www.secnav.navy.mil/fmc/fmb/Documents/23pres/WPN_Book.pdf.
6. MK 48 MOD 7 torpedoes have an average unit cost of around $5 million, but have far less of a requirement to be salvoed in large numbers because of the less saturated nature of undersea warship defenses.
For MK 48 MOD 7 torpedo cost, see:
“Department of Defense Fiscal Year (FY) 2023 Budget Estimates,” Navy Justification Book Volume 1 of 1 Weapons Procurement, Navy, Page 1 of 16 P-1 Line #27, (PDF pg. 351), April 2022, https://www.secnav.navy.mil/fmc/fmb/Documents/23pres/WPN_Book.pdf.
7. “U.S. Airborne Electronic Attack Programs: Background and Issues for Congress,” Congressional Research Service, pg. 16-17, May 14, 2019, https://crsreports.congress.gov/product/pdf/R/R44572.
8. General Accounting Office, “Cruise Missiles: Proven Capability Should Affect Aircraft and Force Structure Requirements,” GAO/NSIAD-95-116, April 1995, pg. 35-36, https://www.gao.gov/assets/nsiad-95-116.pdf.
Newer Tomahawk variants than those discussed above have considerably shorter launch preparation times. See:
“Tomahawk,” Missile Threat CSIS Missile Defense Project, last updated February 23, 2023, https://missilethreat.csis.org/missile/tomahawk/
and
Rear Admiral Edward Masso (ret.), “On The Tomahawk Missile, Congress Must Save The Day,” Forbes, June 10, 2015, https://www.forbes.com/sites/realspin/2015/06/10/on-the-tomahawk-missile-congress-must-save-the-day/?sh=7b86cc956bad.
Featured Image: September 3, 2005 – U.S. Navy Sailors aboard the USS Fitzgerald (DDG 62) inspect the MK 41 Vertical Launching System (VLS). (Photo via U.S. National Archives)