The following article is part of our cross-posting partnership with Information Dissemination’s Jon Solomon. It is republished here with the author’s permission. You can read it in its original form here.
Read part one, part two, and part three of the series.
By Jon Solomon
Candidate Principle #6: Technical Degradation is Temporary, Psychological Effects can be Enduring
It must be appreciated that the greatest damage caused by an adversary’s successful cyber-electromagnetic attack may not be in how it degrades a system or network’s performance, opens the door to kinetic attacks against a force, or even tricks commanders into making operationally or tactically-sub-optimal decisions. All of these are generally temporary effects and can be recoverable with flexible plans, resiliency-embracing doctrine, and crafty tactics. Rather, as renowned naval analyst Norman Friedman has hypothesized, it could very well be the shattering of commanders’ and operators’ trust in their systems and networks that is most destructive. If personnel are not conditioned to anticipate their systems’ and networks’ disruption in combat, an attack’s lasting effect may be a morale-corroding fatalism. Likewise, if they are deceived just once by a manipulated situational picture, and even then not necessarily in a majorly harmful way, they may still hesitate to take needed actions in subsequent engagements out of fear of deception even when none is present. Either of these consequences could result in ceding the tactical if not operational initiative. In a short conflict, this might be catastrophic. Doctrinal collapse might also result, which would be especially debilitating if force structure is designed so tightly around a given doctrine that it severely limits options for creating or adapting operating concepts on the fly.[i]
Interestingly, similar effects might conceivably occur even when a system’s or network’s electronic protection and information assurance measures cause a cyber-electromagnetic attack to only achieve a relatively minor degree of immediate ‘damage.’ In fact, near-continuous cyber-electromagnetic harassment in the form of noise jamming, incessant yet readily parried cyber penetration attempts, situational picture-manipulation attacks that the target’s operators can quickly discover and reverse, intermittent system crashes or network connectivity interruptions that are quickly recovered from, or even severe disruptions of non-critical systems and network services may wear a force’s commanders and crews down mentally even if their critical systems and networks remain fully capable. A clever adversary might actually find this psychological degradation more exploitable (and more likely to be available for use at any given time) than technical degradation. Indeed, cyber-electromagnetic warfare’s psychological applications may well be where it finds its greatest utility.
Assessing the Implications
As the Chief of Naval Operations and others have asserted, the cyber and electromagnetic domains have become equally important to the physical domains in waging modern war.[ii] The cyber-electromagnetic fight will extend throughout all phases of major future conflicts, may begin well before open hostilities break out as an adversary attempts to ‘prepare’ the battle space, and accordingly may be particularly pivotal during a war’s opening phase. Indeed, high-impact anti-network operations with major maritime strategic implications date back as far as the opening moments of the First World War. Just as a belligerent might not be able to win a war with naval dominance alone but could easily lose without it, so it will be for cyber-electromagnetic dominance. It follows that a naval force’s ability to operate within a contested maritime zone will be highly questionable if it cannot effectively suppress or exploit the adversary’s force-level networks while simultaneously parrying the adversary’s own cyber-electromagnetic attacks. This will even extend to operations featuring stealth platforms, as such assets have long needed direct EW support to achieve maximal effectiveness.[iv] Should the U.S. Navy under-appreciate a potential adversary’s integration of cyber-electromagnetic warfare within combined arms doctrine, in a future conflict it would risk facing attrition rates on par with what it endured in the Solomon Islands from summer 1942 through summer 1943—something that its contemporary force structure simply could not endure.[v]
Assuming the candidate principles we have outlined are validated, they will influence future maritime warfare in at least five general ways. First, they will confirm leading tactical theorist Wayne Hughes’s hypothesis from over a decade ago that the next major maritime fight will be defined by the belligerents’ struggle for scouting superiority.[vi] This will represent a drastic change from the U.S. Navy’s post-Second World War combat experiences, in which the absence of threats to its sea control allowed it to focus on maximizing the efficiency and persistence of power projection ashore. Regardless of whether a tactical action pits two naval battleforces against each other, or one against a land-based force, the victor will likely be the side that is able to achieve high-confidence classification, identification, and targeting against his opponent’s forces first, thereby enabling effective attack.[vii] Cyber-electromagnetic discipline and capabilities will clearly be central to the success of the scouting/anti-scouting phases of any future operation.
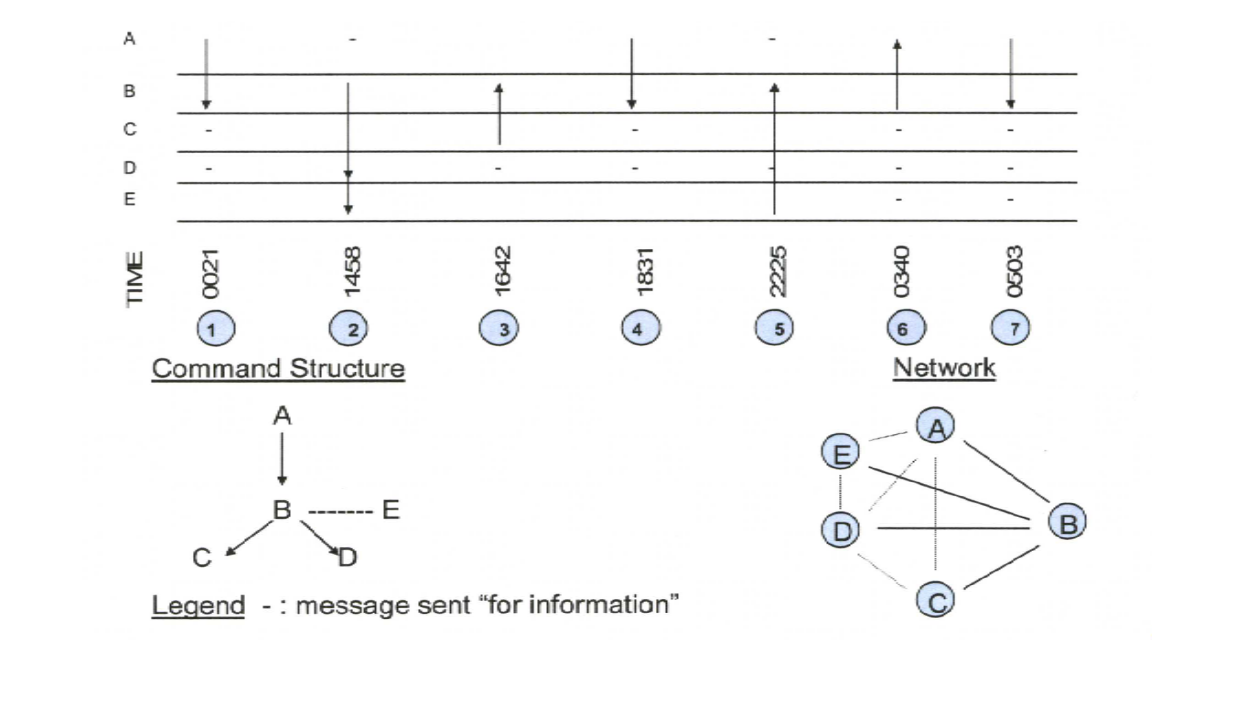
Second, the above signifies that a force will need to extend its effective scouting and anti-scouting reach beyond that of its opponent. This is not achieved solely by covering a given area with more sensors than the opponent, or deploying scouts at greater ranges than the opponent. Rather, as suggested earlier, a sensor network’s effectiveness is equally a function of its architecture. This means the availability of difficult-to-intercept communications pathways and backup communications infrastructure will be just as important as raw coverage volume, lest key sensors be cut off from the network or the situational picture they feed be decisively manipulated. This also means the network must employ multiple sensor types. For surveillance, this translates into multi-phenomenology sensors positioned (or covering areas) as far as possible forward within the battle space, with some using sensing methodologies and platform characteristics that allow them to avoid (or at least delay) counter-detection. For reconnaissance, this requires sensors capable of penetrating the opponent’s force to support the confident confirmation of a given contact’s classification and identity. The U.S. Navy simply cannot afford to waste precious inventories of advanced weapons by falling for deception in a future battle. In this light, the Navy’s proposed Unmanned Carrier Launched Airborne Surveillance and Strike (UCLASS) system could be a critical enabler for effectively employing the proposed Long Range Anti-Ship Missile (LRASM), beyond visual range anti-air missiles, and similar network-enhanced standoff-range maritime weapons. It should not be overlooked that UCLASS, a scouting and attack asset that will be organic to the battleforce, can be designed to support expanded operations on interior lines of networking.
Third, if there is to be a reasonable chance that any degradation will be graceful, cyber-electromagnetic resilience must become a defining attribute of systems’ and networks’ designs. Strong electronic protection and information assurance features are certainly vital, with the latter applying just as much to ‘engineering plant’ systems as to the warfare systems they support. Nevertheless, as no system or network can ever be unexploitable, those central to a force’s tactical capabilities must contain additional design features that allow for quick restoration, graceful degradation, or capability expansion when subjected to withering cyber-electromagnetic attacks. Systems’ avoidance of network-dependency will also help greatly to this end.
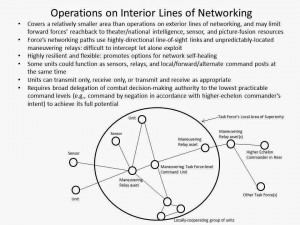
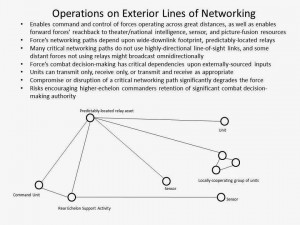
Fourth, operations within opposed cyber-electromagnetic environments will demand C2 decentralization, as a higher echelon’s ability to assert direct, secure control over subordinate units under such circumstances will be dubious. Even if possible, this kind of close control will almost certainly be inadvisable if only for force concealment and counter-exploitation considerations. Instead, maritime forces will need to re-embrace ‘command-by-negation’ doctrine, or rather the broad empowerment of lower-level commanders to exercise initiative in accordance with their higher commander’s pre-disseminated intentions, if they are to fight effectively. Relatedly, aggressive experimentation will be needed to find the proper balance between operating on interior and exterior lines of networking when inside a contested zone—and will probably reveal that the bias should be towards the former.
Lastly, forces capable of operating under command-by-negation and in opposed cyber-electromagnetic environments are not developed overnight. Frequent and intensive training under realistic combat conditions will be needed if the requisite force-wide skills are to be developed.[viii] In particular, much as we have traditionally done to cultivate physical damage control readiness, commanders and crews on the deck plates must be regularly conditioned to expect, recognize, and fight-through cyber-electromagnetic attacks. A force’s cyber-electromagnetic resilience will depend in no small way upon its personnel’s technical, tactical, and psychological preparation for operating with critical systems and networks degraded if not compromised, and with situational pictures that have been manipulated. Likewise, a force’s ability to successfully deceive the adversary—not to mention successfully employ countermeasures against the adversary’s weapons—will depend upon the cyber-electromagnetic tactical skills the force’s personnel cultivate through routinized peacetime training. Emission control discipline, decoy placement relative to defended assets, precision evasive maneuvers, precision timing and sequencing of tactics, and the like require frequent practice if commanders and crews are to gain and then maintain just the minimum proficiencies needed to survive in modern maritime battle. The Navy’s next Strategy for Achieving Information Dominance needs to make it clear that cyber-electromagnetic competence must not be isolated to its Information Dominance Corps, and instead must be ingrained within the total force.
While cyber-electromagnetic risks hardly invalidate the use of advanced sensor and networking technologies, they do caution us not to take for granted that our systems and networks will be secure, functional, and reliable when needed. Our doctrine, contingency operational plans, and tactics must be structured around the assumption each of our warfare systems contain exploitable cyber-electromagnetic vulnerabilities that may prevent us from using them to their fullest—or at all—when most needed. We must not allow ourselves to build and field a force that can only fight effectively when its systems and networks are unhindered and uncompromised.
Jon Solomon is a Senior Systems and Technology Analyst at Systems Planning and Analysis, Inc. in Alexandria, VA. He can be reached at jfsolo107@gmail.com. The views expressed herein are solely those of the author and are presented in his personal capacity on his own initiative. They do not reflect the official positions of Systems Planning and Analysis, Inc. and to the author’s knowledge do not reflect the policies or positions of the U.S. Department of Defense, any U.S. armed service, or any other U.S. Government agency. These views have not been coordinated with, and are not offered in the interest of, Systems Planning and Analysis, Inc. or any of its customers.
[i] Norman Friedman. “Trust but Verify.” Naval Institute Proceedings 134, No. 11 (November 2008), 90-91.
[ii] ADM Jonathan Greenert, USN. “Imminent Domain.” Naval Institute Proceedings 138, No. 12 (December 2012), 17.
[iii] LCDR James T. Westwood, USN. “Electronic Warfare and Signals Intelligence at the Outset of World War I.” U.S. National Security Agency, undated, accessed 1/31/14, http://www.nsa.gov/public_info/_files/cryptologic_spectrum/electronic_warfare.pdf
[iv] See 1. ADM Jonathan Greenert, USN. “Payloads Over Platforms: Charting a New Course.” Naval Institute Proceedings 138, No. 7 (July 2012), 18-19; 2. Gordon and Trainor, 213-215, 217; 3. Arend G. Westra. “Radar Versus Stealth: Passive Radar and the Future of U.S. Military Power.” Joint Forces Quarterly 55 (October 2009), 136-143.
[v] Thomas G. Mahnken. “China’s Anti-Access Strategy in Historical and Theoretical Perspective.” Journal of Strategic Studies 34, No. 3 (June 2011), 310.
[vi] CAPT Wayne Hughes, Jr, USN (Ret). Fleet Tactics and Coastal Combat, 2nd Ed. (Annapolis, MD: Naval Institute Press, 2000), 201-202, 210-212.
[vii] Ibid, 40-44.
[viii] Solomon, “Maritime Deception and Concealment,” 104-106.