After more than a decade of land war and a desire to rebalance to Asia, America’s Navy finds itself smaller, and in many ways weaker in certain respects. One area that should be of great concern is the current practice and future of maritime cryptology.
Cryptology at sea was proven decisive during World War II, beginning with the battle at Midway and the breaking of the Japanese naval code “JN25.”[i] Equally important was the allied program that cracked the German Enigma machines, “Ultra,” especially those used by the German Navy. Winston Churchill famously remarked to King George VI that, “It was thanks to Ultra that we won the war.”[ii]
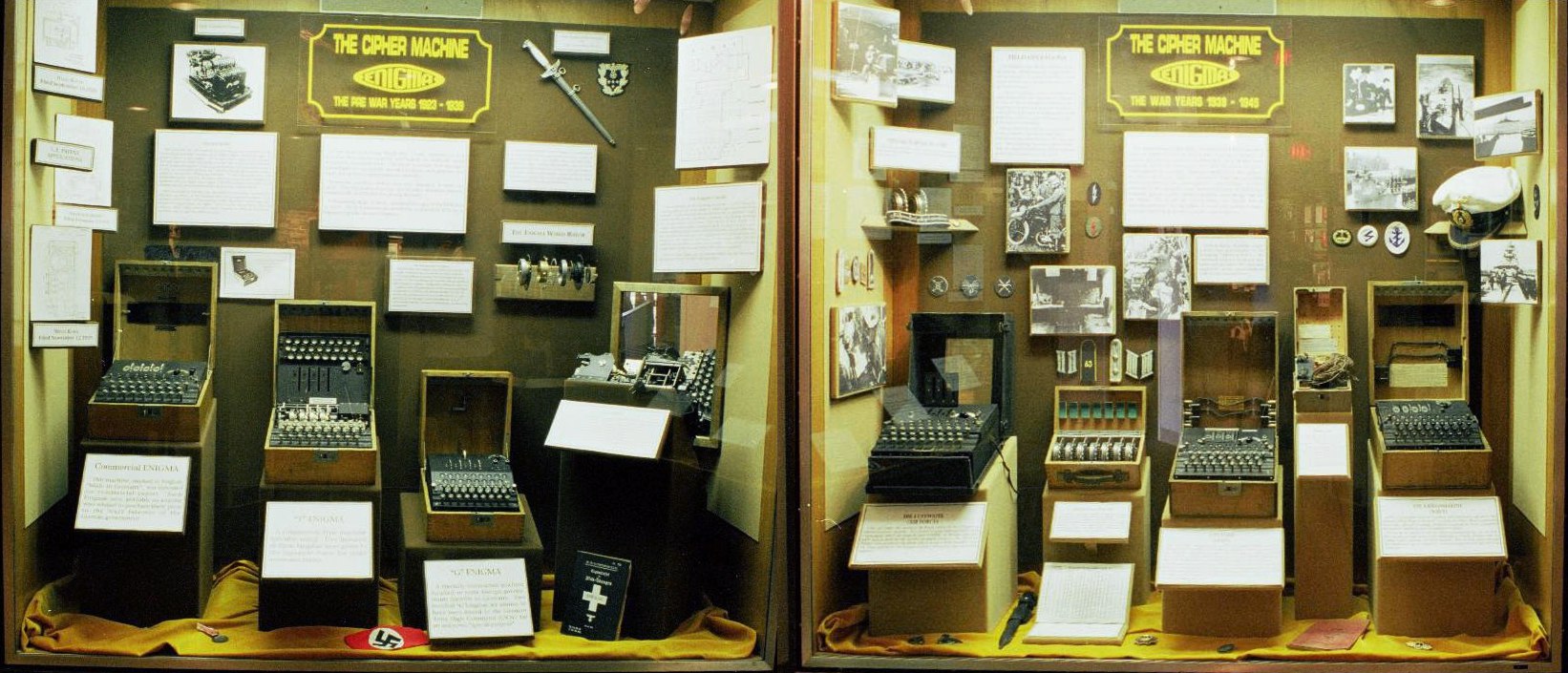
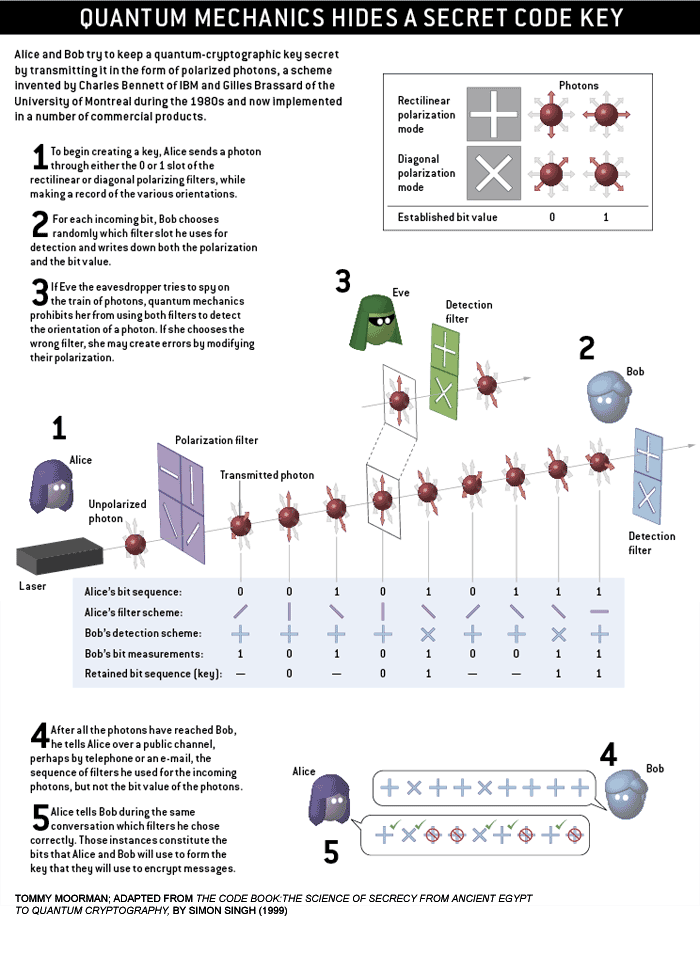
The hope was that through force shaping, automation and remote operations, maritime cryptology could continue to thrive in an ever more complex electromagnetic (EM) environment. Adversarial communications have become far more challenging to detect, exploit and prosecute. The Radio Frequency (RF) environment of today is incredibly complex, with tactical, strategic and data communication links operating in all areas of the spectrum and often at frequencies with a very low probability to intercept. Modern encryption techniques have evolved from mechanical electronics to the use of quantum mechanics.[iv]
The effects of force shaping, automation and remote operations are beginning to take their toll on the tradecraft of maritime cryptology. Today’s junior Sailors and officers have had their training time cut in order to meet growing operational demands on a shrinking Navy. To be successful in the art of cryptology – and it is a practiced art – one must have a deep understanding of the fundamentals of radio signal transmission as well as more than a passing familiarity with the collection equipment. A junior cryptologic technician and junior officer should be able to draw a basic transmitter-receiver diagram and trace the origin of a signal from its original state, such as voice or data, through the transmitter, across a medium and into the collection gear and the operator’s ears. Foundational knowledge required that the basic operator have a working knowledge of the equipment and be able to perform diagnostic and troubleshooting tasks in the event of a malfunction. Finally, operators and junior officers must understand the process of signal intelligence reporting to the tactical unit at sea (indications and warning intelligence) as well as to the national signal intelligence system.
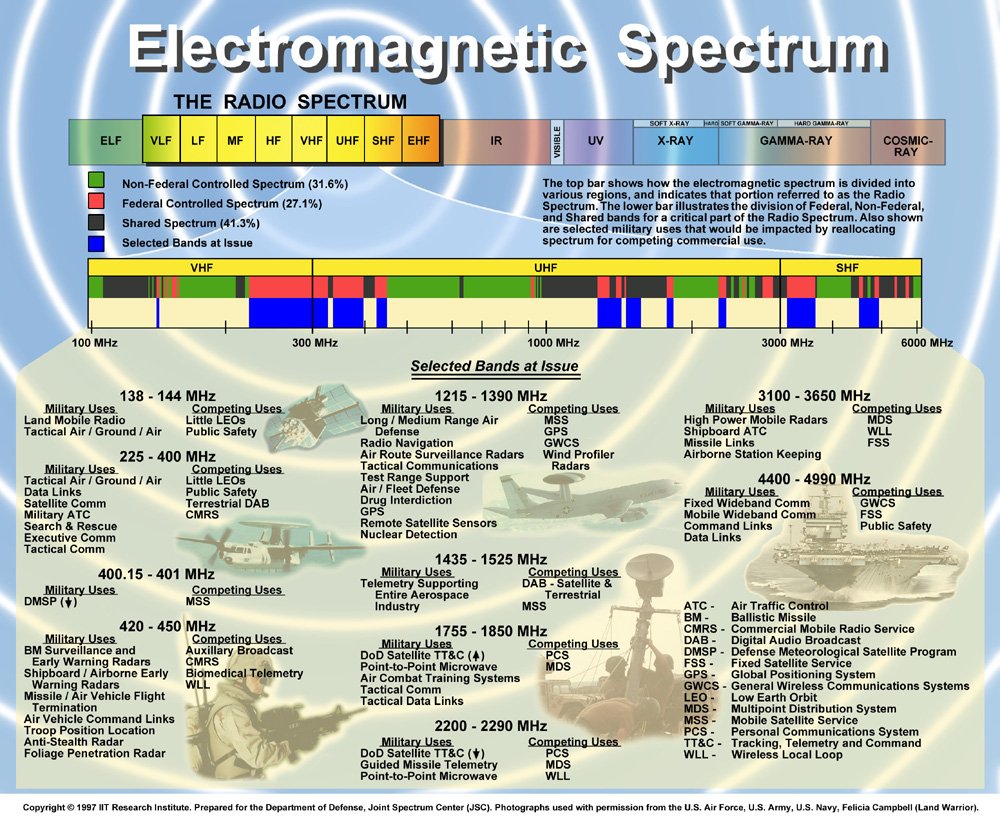
At the same time, emerging cyberspace communication networks place entirely new pressures on maritime cryptology. Modern communication, command, control and information sharing are a “network of networks,” an “Internet of things” that require new skill sets and new acquisition and exploitation technologies. Yet the complexity of data systems and volume of data being passed is growing exponentially, outpacing our acquisition and procurement capability. The Navy has tried to mitigate this by relying on commercial off-the-shelf technology (COTS) but this entails its own set of problems. COTS technology must be compatible with legacy systems – some more than twenty years old and built on architecture and code from the late 1980s and early 1990s – and it relies on bandwidth levels that are not always available and reliable. We often find out the hard way that equipment which works well in the sterile lab environment is not up to the task of performing reliably at sea under arduous conditions.
Maritime cryptology is at a cross roads. We must return to the fundamentals of signal intelligence at the same time we are trying to realize the potential of cyberspace operations at sea. This will require a renewed commitment to recruitment and training, and for many middle grade and senior enlisted cryptologic technicians and officers, it means new formal training. Right now, senior enlisted and officers are being asked to take leadership roles in an emerging cyberspace operations field for which they are receiving inadequate or no formal training. We must reconsider recruitment of new junior Sailors and officers who have the background skills, education and knowledge and provide them a career path that emphasizes cryptologic expertise across the spectrum, from “traditional” signals intelligence to modern wireless exploitation. This career path must be grounded in recognizing that maritime cryptology is more art than science, and to become proficient and experienced, one must practice.
The author would like to thank CDR Kevin Ernest who kindly provided his thoughts on the challenges of modern maritime cryptology.
LT Robert “Jake” Bebber is an information warfare officer assigned to the staff of U.S. Cyber Command. The views expressed here are his own and do not represent those of the Department of Defense, the Department of the Navy or U.S. Cyber Command. He welcomes your comments at jbebber@gmail.com.
[i] http://www.navy.mil/midway/how.html
[ii] http://www.history.co.uk/study-topics/history-of-ww2/code-breaking
[iii] http://en.wikipedia.org/wiki/Enigma_machine#cite_note-9
[iv] http://blogs.scientificamerican.com/guest-blog/2012/11/20/quantum-cryptography-at-the-end-of-your-road/






 This week, Sea Control Asia Pacific looks at cyber security in the region.
This week, Sea Control Asia Pacific looks at cyber security in the region.