By Ben DiDonato
The Navy’s current Large Unmanned Surface Vehicle (LUSV) concept has received heavy criticism on many fronts. To name but a few, Congress has raised concerns about concepts of operation and technology readiness, the Congressional Research Service has flagged the personnel implications and analytical basis of the design, and legal experts have raised alarm over the lack of an established framework for handling at-sea incidents involving unmanned vessels. An extensive discussion of these concerns and their implications would take too long, but in any case, criticism is certainly extensive, and the Navy must comply with Congress’s legal directives.
That said, the core issues with the current LUSV concept arise from one fundamental problem. It’s trying to perform two separate roles – a small surface combatant and an adjunct missile magazine – which have sharply conflicting requirements and require radically different hulls. A small surface combatant needs to minimize its profile, especially its freeboard, to better evade detection, needs a shallow draft for littoral operations, and must have not only a crew, but the necessary facilities for them to perform low-end security and partnership missions to provide presence. The adjunct missile magazine, on the other hand, must accommodate the height of the Mk 41 VLS which substantially increases the draft and/or freeboard, should not have a crew, and should avoid detection in peacetime to increase strategic ambiguity. Not only do these conflicts make it irrational to design one vessel to fulfill both missions, but they point to two entirely separate types of vessels since the adjunct missile magazine role should not be filled by a surface ship at all.
The Adjunct Missile Magazine
The adjunct missile magazine role is best filled by a Missile Magazine Unmanned Undersea Vessel (MMUUV). Sending this capability underwater immediately resolves many of the issues associated with a surface platform since it cannot be boarded, hacked, detected by most long-range sensors, or hit by anti-ship missiles, and so obviates most crew, security, and legal questions. The size required to carry a full-sized VLS also makes it highly resistant to capture since it should have a displacement on the order of 1,000 tons, far more than most nets can bring in, and it could also be designed with a self-destruct capability to detonate its magazine.
The cost should be similar to the current LUSV concept since it can dispense with surface ship survivability features like electronic warfare equipment and point defense weapons to offset the extra structural costs. Because it has no need to fight other submarines and would use standoff distance to mitigate ASW risks, it has no need for advanced quieting or sonar and could accept an extremely shallow dive depth. Even a 150-foot test depth would likely be sufficient for the threshold requirement of safe navigation, and anything past 200 feet would be a waste of money. These are World War One submarine depths. Furthermore, since it only needs to fire weapons and keep up with surface combatants while surfaced, a conventional Mk 41 VLS under a watertight hatch could be used instead of a more complex unit capable of firing while submerged. For additional savings, the MMUUV could be designed to be taken under tow for high-speed transits rather than propel itself to 30+ knots. A speed on the order of 5 knots would likely be sufficient for self-propelled transit, and it would only need long range, perhaps 15,000 nautical miles, to reach its loiter zone from a safe port without tying up underway replenishment assets. Since visualization is helpful for explaining novel concepts, the Naval Postgraduate School (NPS) design team produced a quick concept model to show what this platform might look like. In the spirit of minimizing cost at the expense of performance, and projecting that tugs could handle all port operations, all control surfaces are out of the water while surfaced to reduce maintenance costs.
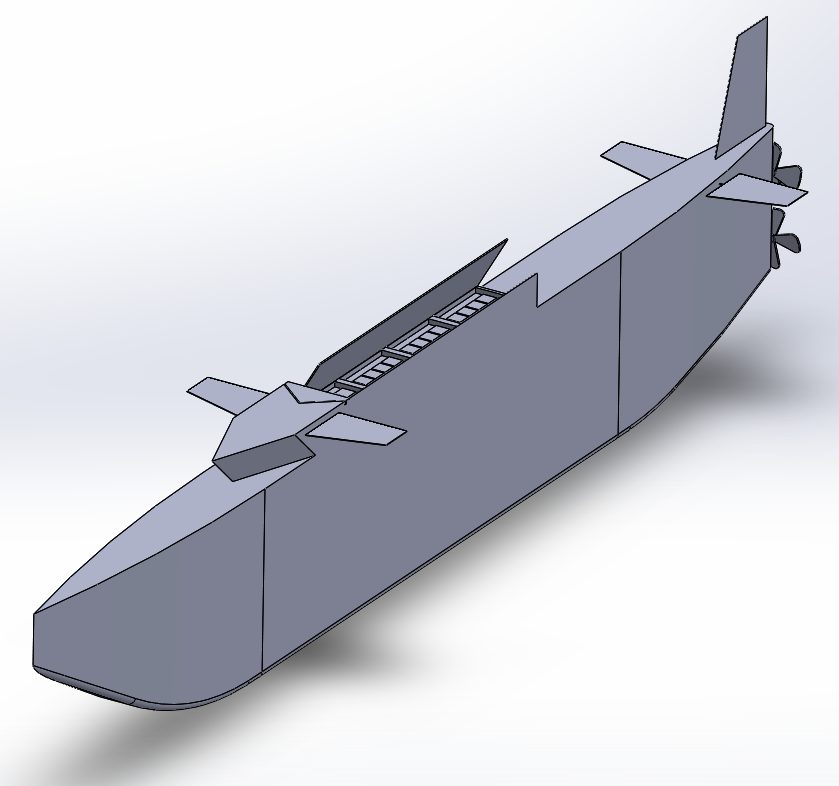
On the command-and-control front, the situation is greatly simplified by the fact that the MMUUV would spend most of its time underwater. In its normal operating mode, it would be dispatched to a pre-planned rendezvous point where it would wait for a one-time-use coded sonar ping from a traditional surface combatant commanding it to surface. It would then be taken under tow and fired under local control using a secure and reliable line-of-sight datalink to eliminate most of the concerns associated with an armed autonomous platform. A variation of this operating mode could also be used as a temporary band-aid for the looming SSGN retirement, since MMUUVs could be loaded with Tomahawks, prepositioned in likely conflict zones, and activated by any submarine or surface ship when needed to provide a similar, if less flexible and capable, concealed strike capability to provide strategic ambiguity. Finally, these platforms could be used as independent land attack platforms by pre-programming targets in port and dispatching them like submersible missiles with a flight time measured in weeks, instead of minutes or hours. Under this strike paradigm, a human would still have control and authorize weapon release, even if that decision and weapon release happens in port instead of at sea. This focus on local control also mitigates cybersecurity risks since the MMUUV would not rely on more vulnerable long-range datalinks for most operations and could perform the independent strike missions with absolutely zero at-sea communications, making cyberattack impossible.
As a novel concept, this interpretation of the adjunct missile magazine concept obviously has its share of limitations and unanswered questions, particularly in terms of reliability and control. Even so, these risks and concerns are much more manageable than the problems with the current LUSV concept, and so give the best possible chance of success. More comprehensive analysis may still find that this approach is inferior to simply building larger surface combatants to carry more missiles, but at least this more robust concept represents a proper due-diligence effort to more fully explore the design space.
The Small Surface Combatant
The other role LUSV is trying to fill is that of a small surface combatant. These ships take a variety of forms depending on the needs and means of their nation, but their role is always a balance of presence and deterrence to safeguard national interests at minimal cost. The US Navy has generally not operated large numbers of these types of ships in recent decades, but the current Cyclone class and retired Pegasus class fit into this category.
While limited information makes it difficult to fully assess the ability of the current LUSV concept to fill this role, what has been released does not paint a promising picture. The height of the VLS drives a very tall hull for a ship of this type which makes it easy to detect, and therefore vulnerable, a problem that is further compounded by limited stealth shaping and defensive systems. There also does not seem to be any real consideration given to other missions besides being an adjunct missile magazine, with virtually no launch capabilities or additional weapons discussed or shown. This inflexibility is further compounded by the Navy’s muddled manning concept, which involves shuffling crew around to kludge the manned surface combatant and unmanned missile magazine concepts together in a manner reminiscent of the failed LCS mission module swap-out plan. Finally, the published threshold range of 4,500 nautical miles, while likely not final, is far too short for Pacific operations without persistent oiler support.
The result is a vulnerable, inflexible ship unsuited to war in the Pacific, and thus incapable of deterring Chinese aggression. This may indicate the current LUSV concept is intended more as a technology demonstrator than an actual warship. However, because the U.S. Navy urgently needs new capabilities to deter what many experts see as a window of vulnerability to Chinese aggression, the current plan is unacceptable.
Fortunately, there is an alternative ready today. The Naval Postgraduate School has spent decades studying these small surface combatants and refining their design, and is ready to build relevant warships today. The latest iteration of small surface combatant design, the Lightly Manned Autonomous Combat Capability (LMACC), achieves the Navy’s autonomy goals while providing a far superior platform at a lower cost and shorter turnaround time. Where the LUSV design is large, unstealthy, and poorly defended, the LMACC has a very low profile, aggressive stealth shaping, SeaRAM, and a full-sized AN/SLQ-32 electronic warfare suite designed to defend destroyers, making it extremely difficult to identify, target, and hit. While the LUSV concept is armed with VLS cells, LMACC would carry the most lethal anti-ship missile in the world, LRASM, as well as a wide range of other weapons to let it fulfill diverse roles like anti-swarm and surface fire support, something that cannot be done with LUSV’s less diverse arsenal. To maximize its utility in the gray zone, the LMACC design boasts some of the best launch facilities in the world for a ship of its size.
On the manning front, LMACC has a clearly defined and legally unambiguous plan with a permanent crew of 15, who would partner with the ship’s USV-based autonomous capabilities and team with a variety of other unmanned platforms. This planned 15-person crew is complemented by 16 spare beds for detachments, command staff, special forces, or EABO Marines to maximize flexibility, and also hedges against the unexpected complications with automated systems which caused highly publicized problems for LCS.
LMACC was designed with the vast distances of the Pacific in mind, so it has the range needed for effective sorties from safe ports and provisions to carry additional fuel bladders when even more range is needed. Unlike the LUSV concept which Congress has rightly pushed back on, LMACC is a lethal, survivable, flexible, and conceptually sound design ready to meet our needs today.
The full details of the LMACC design were published last year and can be found in a prior piece, and since that time the engineering design work has been nearly completed. A rendering of the updated model, which shows all exterior details and reflects the floorplan, is below. Our more detailed estimating work, which has been published in the Naval Engineer’s Journal and further detailed in an internal report to our sponsor, Director, Surface Warfare (OPNAV N96), shows we only need $250-$300 million (the variation is primarily due to economic uncertainty) and two years to deliver the first ship with subsequent units costing a bit under $100 million each. The only remaining high-level engineering task is to finalize the hullform. This work could be performed by another Navy organization such as Naval Surface Warfare Center Carderock, a traditional warship design firm, one of the 30 alternative shipyards we have identified, an independent naval architecture firm, or a qualified volunteer, so we can jump immediately into a production contract or take a more measured approach based on need and funding.
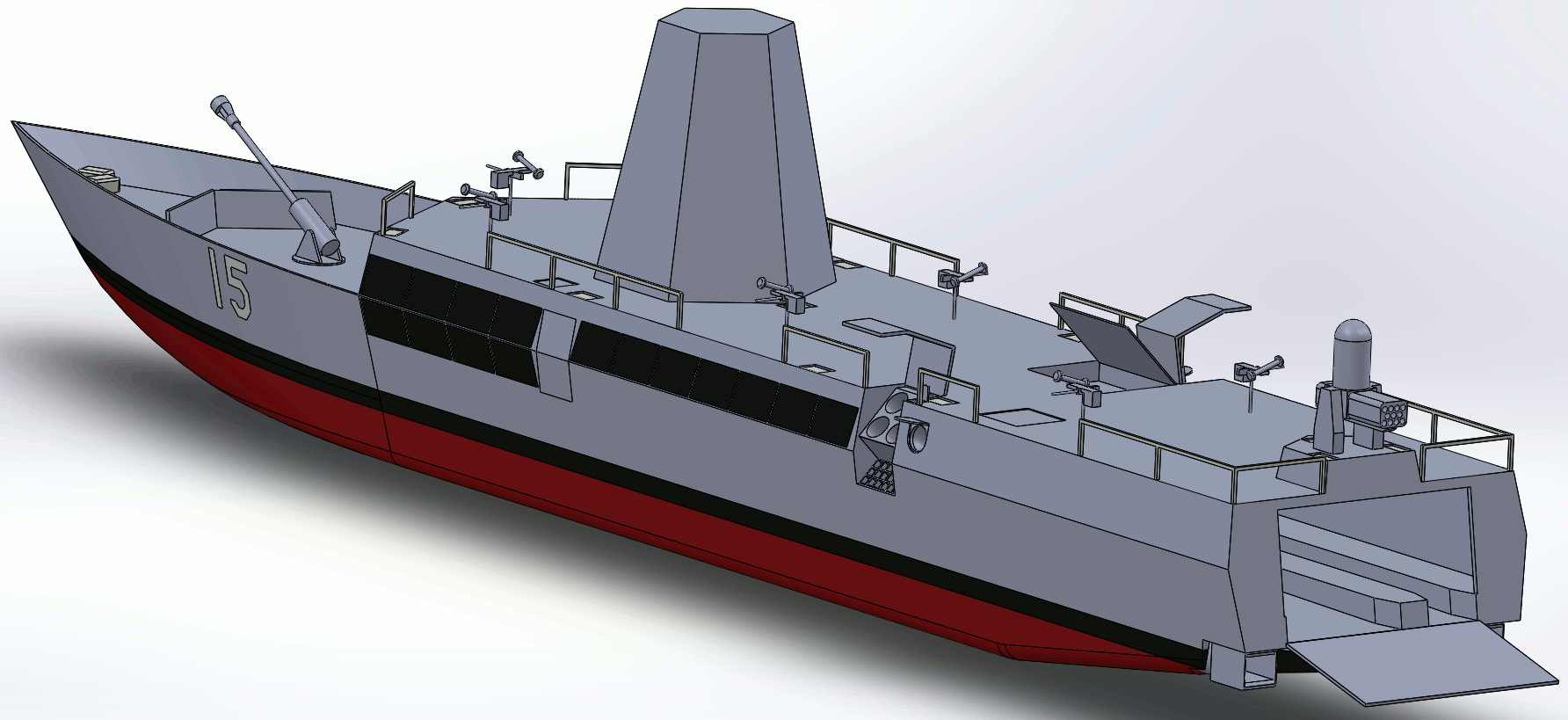
LMACC has also been the subject of extensive studies and wargaming, including the Warfare Innovation Continuum and several Joint Campaign Analysis courses at NPS. Not only have these studies repeatedly shown the value of LMACC when employed in its intended role teamed with MUSVs and EABO Marines, especially in gray zone operations where its flexibility is vital, but they have also revealed its advantage in a shooting war with China is so decisive that not even deliberately bad tactics stop it from outperforming our current platforms in a surface engagement. Finally, while our detailed studies have focused on China as the most pressing threat, LMACC’s flexibility also makes it ideally suited to pushing back on smaller aggressors like Iran and conducting peacetime operations, such as counterpiracy, to guarantee its continued utility in our ever-changing world.
Conclusion
While there are still some questions about the MMUUV concept which could justify taking a more measured approach with a few prototypes to work out capabilities, tactics, and design changes before committing to full-rate production, there is an extensive body of study, wargaming, and engineering behind LMACC which conclusively prove its value, establish its tactics, and position it for immediate procurement at any rate desired. If the Navy is serious about growing to meet the challenge of China in a timely manner, it should begin redirecting funding immediately to pivot away from the deeply flawed LUSV concept and ask Congress to authorize serial LMACC production as soon as possible. Splitting the LUSV program into two more coherent platforms as described in this article will allow the Navy to fully comply with Congress’s guidance on armed autonomy, aggressively advance the state of autonomous technology, and deliver useful combat capability by 2025.
Mr. DiDonato is a volunteer member of the NRP-funded LMACC team lead by Dr. Shelley Gallup. He originally created what would become the armament for LMACC’s baseline Shrike variant in collaboration with the Naval Postgraduate School in a prior role as a contract engineer for Lockheed Martin Missiles and Fire Control. He has provided systems and mechanical engineering support to organizations across the defense industry from the U.S. Army Communications-Electronics Research, Development and Engineering Center (CERDEC) to Spirit Aerosystems, working on projects for all branches of the armed forces. Feel free to contact him at Benjamin.didonato@nps.edu or 443-442-4254.
Additional points of contact:
The LMACC program is led by Shelley Gallup, Ph.D. Associate Professor of Research, Information Sciences Department, Naval Postgraduate School. Dr. Gallup is a retired surface warfare officer and is deeply involved in human-machine partnership research. Feel free to contact him at Spgallup@nps.edu or 831-392-6964.
Johnathan Mun, Ph.D. Research Professor, Information Sciences Department, Naval Postgraduate School. Dr. Mun is a leading expert and author of nearly a dozen books on total cost simulation and real-options analysis. Feel free to contact him at Jcmun@nps.edu or 925-998-5101.
Feature Image: Austal’s Large Unmanned Surface Vessel (LUSV) showing an optionally-manned bridge, VLS cells and engine funnels amidships, and plenty of free deck space with a tethered UAS at the rear. The LUSV is meant to be the U.S. Navy’s adjunct missile magazine. (Austal picture.)






