By Andrew Song
In the race against time, recent history demonstrates that technology remains limited for submarine search and rescue efforts. The November 2017 disappearance of the Argentinian Navy submarine, the ARA San Juan (S-42), highlights the particular hardship confronting submarine recovery. After completing a naval exercise near Tierra del Fuego, the diesel-electric submarine ARA San Juan (S-42) departed from the city of Ushuaia to return to its home port in Mar de Plata. The boat transmitted its last signal on November 15th, 2017 and its failure to report twice to its command the next day prompted an international search and rescue operation starting November 17th.1 This case study examines the limits of aquatic-based forensic methods along with institutional shortcomings that inhibited the investigation. It furthermore underlines how contemporary submarine search tools – for rescue, post-mishap investigation, or espionage – remain underdeveloped and require further attention.
Searching for the ARA San Juan (S-42)
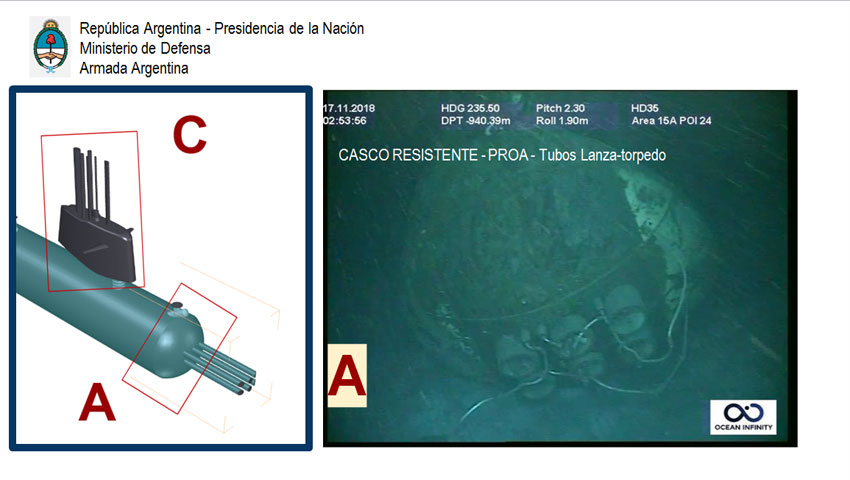
On its one-year anniversary of the San Juan’s disappearance, Ocean Infinity – an American private seabed explorer company contracted by Buenos Aires – located the missing submarine 270 nautical miles off Argentina’s nearest coastal city at a depth of 2,976 feet – roughly three times the nominal test depth.2 Photographs taken by Ocean Infinity’s ROVs portrayed a compromised hull with propellers and a bow section discernibly separated.3 Although presumed beforehand, the imagery eliminated any possibilities that there had been survivors on the ARA San Juan.
Revisiting the initial search operations on the 17th sheds light into the immediate challenges of the submarine search and rescue operations. Argentinian Navy helicopters, U.S Navy P-8A Poseidon, and NASA P-3 Orion aircraft began search efforts with sonobuoys that possessed limited range, but which could be rapidly and widely deployed. It became apparent that space and time disadvantaged the emergency responders: The initial search box was larger than the size of Iraq.4 The ARA San Juan only had a submerged oxygen supply of seven days, giving a five-day rescue window after the last communication. Moreover, the remoteness of the search area and the tardiness in support diminished the probability of success. Over 11 countries sent nine ships and 13 aircraft to the search area, but the additional manpower and vessels arrived by November 21st (T-3 rescue window), requiring aerial-deployed sonobuoys to spearhead localization efforts – not side-scan sonars. 5 These sonobuoys offered a medium to hear distress transmissions from submarine, including via active sonar, underwater telephone, echo sounder, emergency location beacons, and hull tapping.
Other obstacles included unfavorable weather conditions. In the rescue window, investigators battled swells that reached 10 meters and wind speeds in the South Atlantic recorded around 100km/h.6 Yet, the most disappointing element to the abrupt search operation was the abundance of false signatures. In the critical rescue window, multiple incidents hindered search progress by draining resources from follow-up investigations. Table 1 summarizes these sources of hope that were later met with frustration.7
Table 1: Summary of False Leads and Later Determined True Origin
Date Observed Incident Later Determined Cause Location
NOV 20 Satellite Calls on same frequency used by San Juan Commercial Vessel Unspecified
NOV 21 Faulty identification of possible banging on metal from passive sonar Biological Unspecified
NOV 21 Magnetic anomaly with heat signature Equipment 430km from coast
NOV 21 3 Flares seen in vicinity of last location Not Same Color Flares Unspecified
NOV 22 Object found near area of San Juan’s last signal Unrelated debris 270km from coast
The Argentinian Navy declared the rescue aspect of the search operation to be over on November 30th, 2017 after planners eliminated an extreme survival situation. At its height, the search operation constituted over 4,000 personnel from over 13 countries and surveyed over 200,000 square miles.8 On November 16th, 2018, a Houston-based hydrographic survey company, Ocean Infinity, used a Norwegian multipurpose ship to investigate a possible ping on the San Juan’s potential position in the middle of a sea canyon.9 Finally, Ocean Infinity confirmed discovery of the San Juan on November 17th, 2018 and handed over data and visual evidence of the wreckage for forensic investigators to determine cause. Ocean Infinity’s use of five autonomous undersea vehicles (AUVs) for exploring the wreck site suggested that extensive use of AUVs was integral to the mission’s success.


Forensic Shortcomings and New Questions
In the case of the San Juan’s disappearance, investigators must ask themselves about failures in the search phase and prescribe future procedures to avoid such pitfalls. The disappearance of the ARA San Juan disturbingly mirrors the loss of the Kursk in 2003, apart from the evidence that the Kursk had initial survivors post-implosion. First, the Comprehensive Nuclear Test Ban Treaty Organization (CTBTO) in Vienna did detect a hydro-acoustic anomaly from its Ascension Island and Crozet Island stations that seemed consistent with an underwater explosion on November 15th around 30 nautical miles from the San Juan’s last known bearing in the morning.10
Unfortunately, the CTBTO’s automatic processing algorithm used to detect nuclear explosions did not flag the registration of the two hydrophone station’s recording.47 In an effort to minimize false alarms, the CTBTO incidentally failed to exploit data that could have been used towards the calculation of a coverage ellipse for the San Juan. CTBTO could have directed their waveform analysts to immediately deploy their standard iterative dual correspondence (IDC) automatic localization algorithm to produce a spatial diagram of the detonation’s coordinates from iterative minimization of the origin time and azimuth residuals from the seismic data.
This had been done before as Koper details how four land-based seismometers detected the Kursk’s torpedo misfire on August 10th, 2000.11 Collation of the data in the Kursk case allowed for there to be a preliminary ellipse-shaped search parameter for the Kursk. The ARA San Juan’s implosion likely mimicked features of the Kursk’s explosion – compressive first motion, significant variation and high ratio of Sn to Lg, and shear wave generation in the seismic record. The oversight in the hydroacoustic anomaly, although eventually rectified through manual processing, caused the CTBTO to inform Argentina on November 22nd about a possible localization tardy in the search phase.12 Earlier consultation between Argentina and CTBTO and better automated processing for significant non-nuclear seismic events could have produced a more refined search box sooner.
State capabilities also hampered search execution. Ocean Infinity discovered the San Juan in a grid site that had a 90 percent probability of wreckage to be found – at the beginning of search planning.13 Argentinian officials defended themselves by stating that sub-canyons presented a hazard that its Navy could not outmaneuver. In other words, even if the crew was deemed to be alive, Argentina lacked methods and technology like a McCann Rescue Chamber or Deep Submergence Rescue Vehicle (DSRVs) required for a delicate retrieval operation. This deflection of blame, however, shared no merit as U.S operators from Undersea Rescue Command in San Diego arrived with Submarine Rescue Diving and Recompression System and a tethered Pressurized Rescue Module Remotely Operated Vehicle (ROV) in only two days.14

Lastly, the relegation and sidelining of side-scan sonar and UUVs contributed to inefficiency and lack of coverage. Tardiness in the arrival of logistical support signified that these methods could not be practically implemented so total blame could not be place on the planners. Absence in information regarding scenarios and hypotheses did not allow for Bayesian search strategies to be fully utilized, although submarine officers blame a short-circuit in the battery tray in the prow due to water intake from the submarine’s snorkel as a precedent event to the suspected implosion.
That being said, forensic investigators still confront distinct challenges irrelevant to traditional geophysical investigations. Unlike terrestrial-based forensics, pre-established knowledge of a local maritime environment is sparse. Scientists have mapped 1/5th of the sea floor to modern standards with 100m resolution, but that means almost 290 million square kilometers of seafloor – twice the surface area of Mars – has not yet been surveyed. The absence of existing charts, therefore, necessitates simultaneous 4-D mapping of the area.15 Submarine debris are unidentifiable in satellite and aerial images due to surface opacity and the extreme depth of wrecks. Stratification conceals wrecks and clearing sedimentary buildup becomes extremely complicated due to sheer volume. An onsite “walk-over” survey, as described by Fenning and Donnelly in their description of geophysical methodologies, is simply impossible in a marine environment.16 Acidity and pH levels of the water also influence rates of decomposition, and must be considered for a simulation in the casualty scenario. In the future, the undersea recovery field must overcome these variables in order to find any success in submarine search and rescue.

The loss of the ARA San Juan devastated the Argentinian public and had harmful repercussions on its naval service. Not only did Argentina lose 44 sailors, but one of the San Juan’s crewmembers was the first female submarine officer (Lieutenant Eliana Krawczyk) in Argentina’s history.17 Federal policemen raided the Navy’s headquarters for document requisition to piece together culpability and allocate responsibility. Argentina’s Minister of Defense unceremoniously fired Marcelo Srur, the Navy’s Chief of the General Staff, and the events surrounding the ARA San Juan’s mission — tracking British assets near the Falkland Islands — was publicly leaked by an Argentinian media source, further embarrassing the Navy.18
Conclusion
The task of finding lost submarines is an enigma complicated even further by the very reason these boats exist: to be undetectable assets for national security. Unlike their geologist peers, marine forensic investigators rely on robotics and invisible sound waves as surrogate sensors to hands and eyes. The development of side-scan sonar systems, and the consolidation of UUVs for search operations and site verification amalgamate the practice of maritime search into a forensic field heavily invested and intertwined with technological innovation. When establishing an inaugural search parameter, best practices in Bayesian search strategy call for officers and scientists to weigh qualitative hypotheses in order to allocate priorities to search boxes that will offer maximum efficiency.
The ARA San Juan represents a recent case, where these methods did not seem utilized to the fullest capacity. Prior success in the history of these methodologies being used for finding WWII vessels demonstrate that perhaps governments must rethink quick reaction plans to lost submarines. In order to save lives and honor the gravesites of individuals lost in times of conflict, advancement of these methods and a reevaluation of the ARA San Juan’s loss will be beneficial for the global submarine community and for navies around the world.
Ensign Andrew Song is a U.S. Navy submarine officer assigned to the USS San Francisco (MTS-711). His past publications have appeared in peer-reviewed military journals and outlets including Military Review, Journal of Indo-Pacific Affairs, USNI Proceedings, Yale Review for International Studies and the Wall Street Journal. He graduated from Yale University with a B.A. in Global Affairs.
Endnotes
1. Politi, Daniel; Londoño, Ernesto (30 November 2017). “Hope for Argentina Submarine Crew Fades”. The New York Times. Nov 30, 2017.
2. “First photos of submarine emerge as families implore Argentine government to recover wreck”. NewsComAu. 18 November 2018.
3. “ARA San Juan.” Ocean Infinity, June 16, 2020. https://oceaninfinity.com/projects/ara-san-juan/.
4. Kirby, John. “Argentine Navy Says Sounds Detected Aren’t from Missing Sub.” CNN. Cable News Network, November 21, 2017. http://edition.cnn.com/2017/11/20/americas/argentina-missing-submarine/index.html.
5. Ibid.
6. Pecoraro, Natalia. “El Fuerte Viento Demora El Operativo y Complica Las Tareas De Rescate.” La Nación, November 26, 2017. https://www.lanacion.com.ar/politica/el-fuerte-viento-demora-el-operativo-y-complica-las-tareas-de-rescate-nid2085829/.
7. “Avanza Un Operativo Donde Hace 8 Días Se Detectó Una ‘Anomalía Hidroacústica.’” Télam, November 23, 2017. https://www.telam.com.ar/notas/201711/225405-ara-san-juan-busqueda-armada-argentina-ruido-anomalia-hidroacustica.html (2) Goni, Uki. “Argentina’s Navy Says Fresh Noises Are Not from Missing Submarine.” The Guardian. Guardian News and Media, November 21, 2017. https://www.theguardian.com/world/2017/nov/20/missing-argentina-submarine-running-out-of-air-as-search-enters-critical-phase.
8. “San Juan Submarine: ‘Explosion’ Dashes Crew Survival Hopes.” BBC News. BBC, November 23, 2017. https://www.bbc.com/news/world-latin-america-42100620.
9. “ARA San Juan.” Ocean Infinity, June 16, 2020. https://oceaninfinity.com/projects/ara-san-juan/.
10. Nielsen, P.L., Zampolli, M., Le Bras, R. “CTBTO’s Data and Analysis Pertaining to the Search for the Missing Argentine Submarine ARA San Juan.” Pure Appl. Geophys. https://doi.org/10.1007/s00024-020-02445-9. January 31 2020.
11. Koper, K. D., et al., 2001. Forensic seismology and the sinking of the Kursk, Eos, 82, 45-46.
12. Politi, Daniel, and Mihir Zaveri. “Argentina Minister Says Country without Means to Rescue Submarine.” thestar.com, November 17, 2018. https://www.thestar.com/news/world/2018/11/17/missing-argentine-submarine-found-at-bottom-of-atlantic-one-year-after-disappearance.html.
13. Ibid.
14. “Argentina Missing Navy Submarine: Search Stepped Up.” BBC News. BBC, November 18, 2017. https://www.bbc.com/news/world-latin-america-42030560.
15. Amos, Jonathan. “One-Fifth of Earth’s Ocean Floor Is Now Mapped.” BBC News. BBC, June 20, 2020. https://www.bbc.com/news/science-environment-53119686.
16. Fenning, P. J., Donnelly, L. J., 2004. Geophysical techniques for forensic investigation. Geological Society of London Special Publications, 232, 11-20.
17. Argentina: Wreck of ARA San Juan Submarine Found after One Year . Al Jazeera English, 2018. https://www.youtube.com/watch?v=MxufaPwlTOA.
18. Gidget Fuentes, Special Correspondent. “Specialized Undersea Rescue Force on Call to Aid Submariners in Trouble.” Seapower, October 20, 2020. https://seapowermagazine.org/specialized-undersea-rescue-force-on-call-to-aid-submariners-in-trouble/.
Featured Image: The ARA San Juan of the Argentine Navy. (Argentine Navy photo)