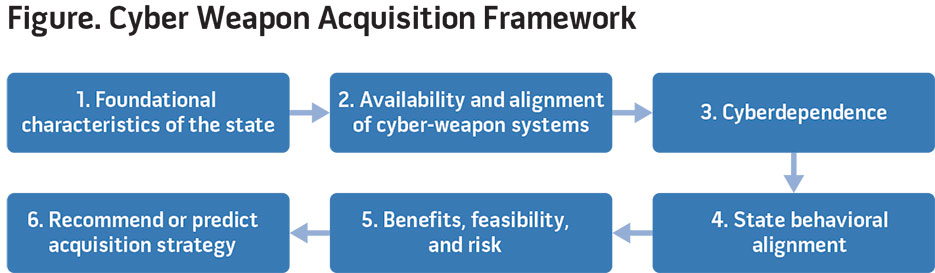
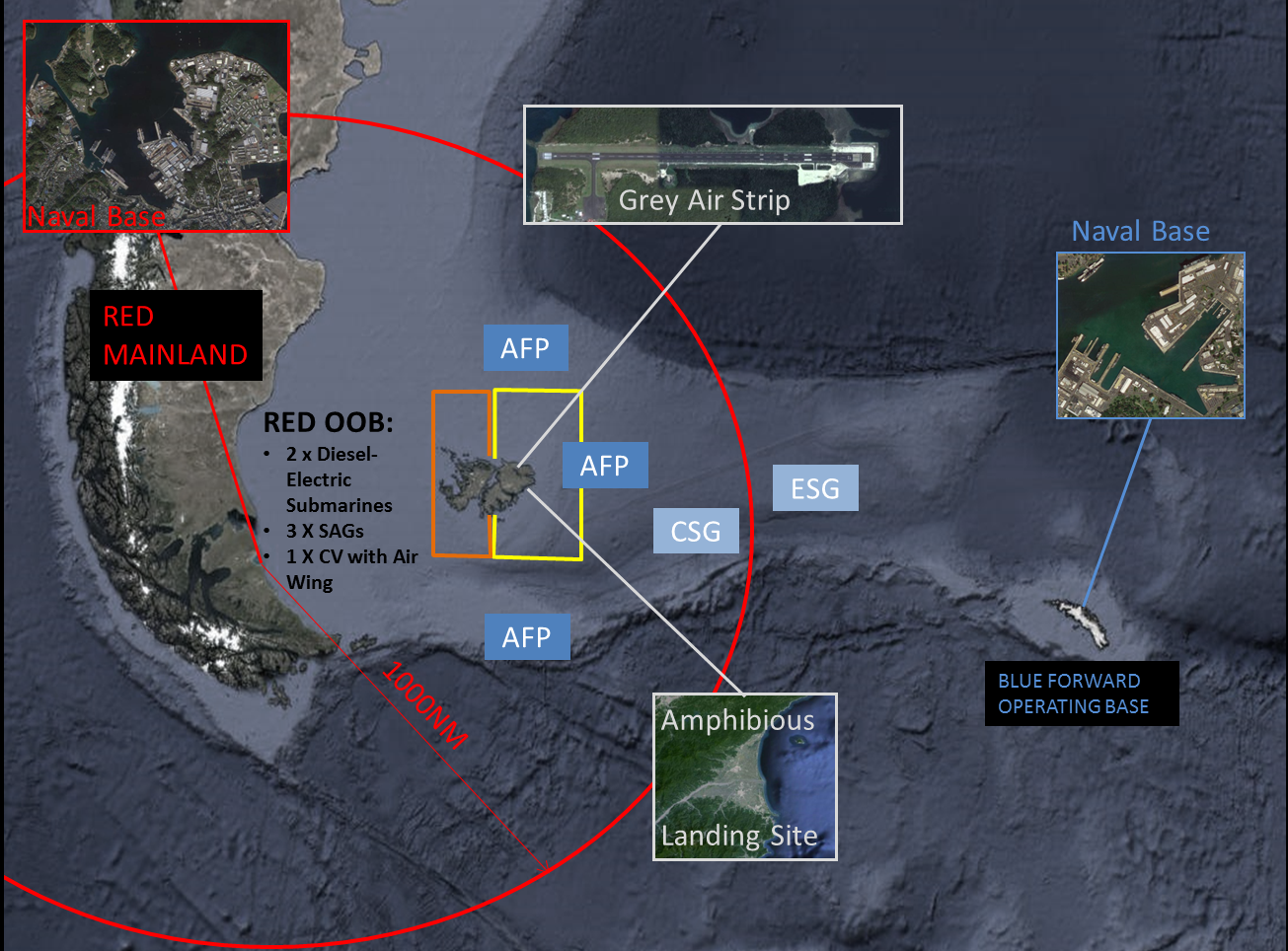
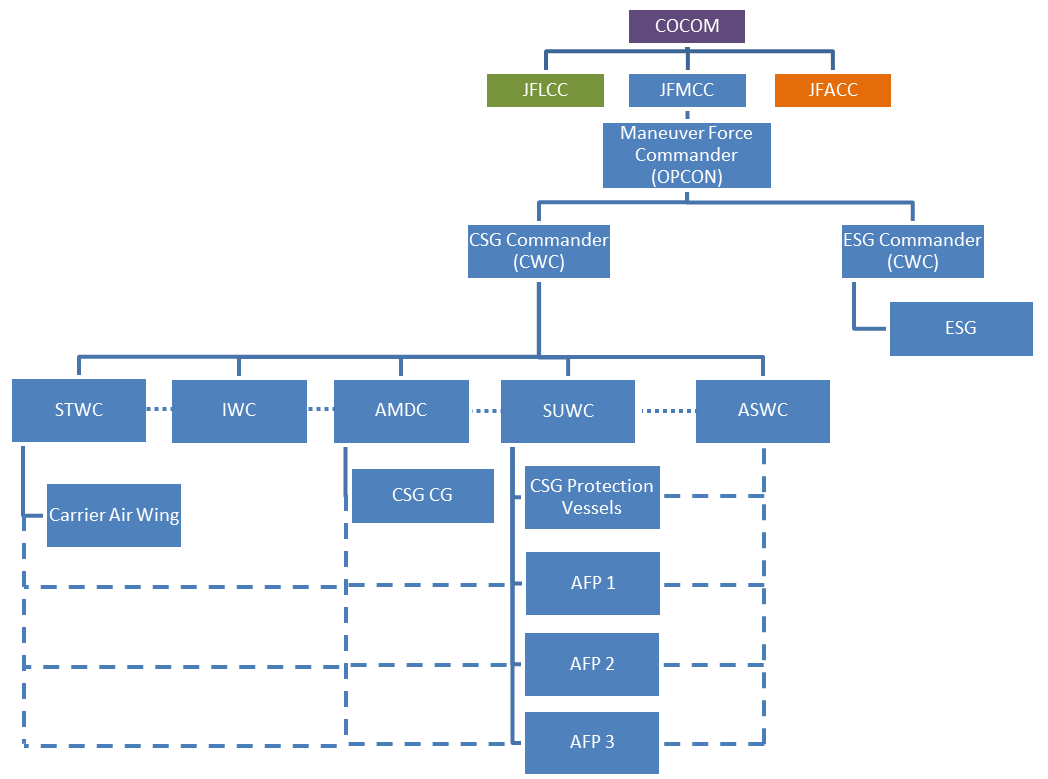
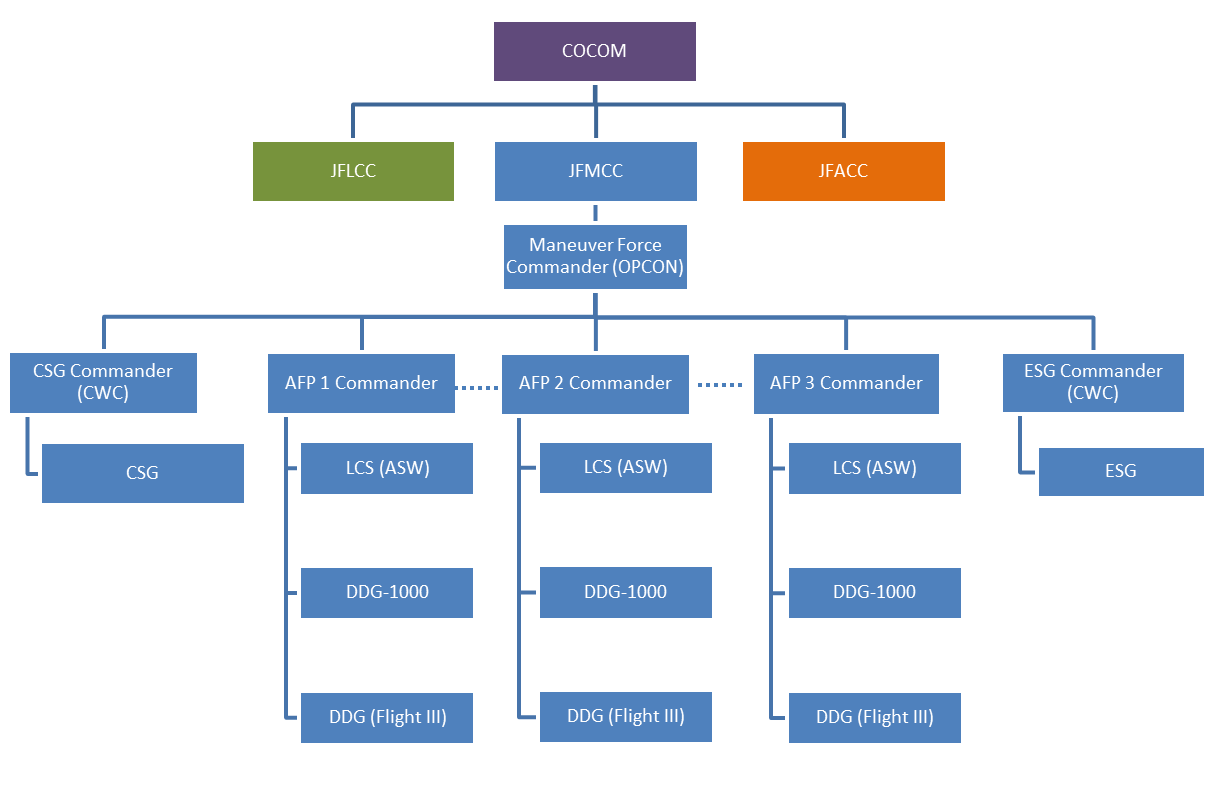
By Alex Calvo
Introduction
The third installment in our four-part series begins with Trident’s impact on British industry and the Scottish factor, very much in evidence in the run up to the 2014 referendum. We then move to examine British nuclear doctrine, asking ourselves whether a minimal posture is tenable, and looking in this connection at potential cyber and undersea unmanned threats to submarines, both of which have attracted public attention over the last few months. While in July this year the UK Parliament voted to renew the Trident fleet with the building of four new submarines, it is still interesting to discuss whether Trident’s cost may have been cut by reducing the number of boats. We then move to consider potential nuclear alternatives to the program, starting with long-range bombers and land-based missiles, leaving submarine and air-launched cruise missiles for the fourth and final installment in our series. Read Part One, Part Two.
Trident and British Industry
Any decisions on defense have an industrial component, leading to an uneasy conundrum. On the one hand, the acquisition of assets should be at least primarily motivated by the needs and priorities laid down in defense planning. On the other, because of the sums involved and the strong link between military and civilian research and development, it is impossible to view defense procurement separately from industrial and scientific policy. Thus, while the decision on the continuity of Trident taken in July this year by the UK Parliament should ideally not rest on the interests of the industrial actors involved, we cannot simply dismiss them when analyzing it. In particular, when pondering both nuclear and non-nuclear alternatives to Trident, it is likely that British authorities examined the resulting net effect on British defense and dual-use industries as a whole and on those companies involved in Trident.
We could say something similar when it comes to jobs, which should not have been the primary consideration, but are likely to have featured in this political decision. Some estimates say up to 15,000 jobs may have been lost had Trident not been renewed, but the net impact both in terms of figures and human capital depends on the alternatives should Trident been discontinued. BASIC notes how Trident’s base “supports some 6,700 jobs, expected to rise to 8,200 by 2022,” adding that “the UK submarine industry accounts for 3% of employment in the UK’s scientific and defense industrial base,” and that a “replacement as currently planned could employ up to 26,000 people at some point in the process.” This could at least partly explain the huge majority of 355 in a 650-strong chamber that voted for the program’s renewal with more than half of opposition Labour MPs voting aye in direct contradiction with their leader’s stance, and this after PM Theresa May had publicly made it clear she was ready to press the nuclear button if necessary. Furthemore, while Labour leader Jeremy Corbyn was later reelected by an increased majority of 62 percent, his shadow defense minister, Clive Lewis, stated that his party would remain committed to an independent, sea-based, British nuclear deterrent.
The Scottish Factor: Trident and the Union
The SNP and, more widely, Scottish Nationalists, have traditionally been hostile to Trident for a number of reasons. Among them we may note the party’s weak commitment to security and defense, little regard for collective security, hostility to the notion of the UK as a major world power, and willingness to outsource key policy areas to the European Union. At the tactical level, as seen in the 2014 referendum campaign, opposing Trident may enable the Nationalist camp to attract voters not strongly for or even opposed to independence but who fiercely reject nuclear weapons. Some of these voters may see a non-nuclear independent Scotland as a lesser evil. Others in this category may have seen a vote for independence or a vote for the SNP in future elections as a tactical move to force an end to the British nuclear deterrent. The July 2016 parliamentary vote on Trident was yet another opportunity for the SNP to underline its opposition to Trident, made even more visible by the vote in favor of a majority of opposition Labour MPs. Its 54 members of parliament voted against, and the party warned it would prompt a further push for independence, although opinion polls suggest a majority of Scots favor retaining the deterrent.
In connection to this matter, in the run-up to the referendum, there was speculation that the UK may relocate Trident to Devonport (Plymouth), with a report by RUSI estimating the additional cost at £3.5bn. The report concluded that “while the technical and financial challenges presented by Scottish independence would influence this discussion, they would not be severe enough to dictate it.”
British Nuclear Doctrine: Is a Minimal Posture Tenable?
If the UK’s move to a minimal deterrence posture had been followed by other nuclear states, or at least by negotiations with that purpose in mind, the country may have gone down in the annals of history as a pioneer in the noble pursuit of nuclear disarmament. Although the concept, also referred to as “deterrence lite,” has been extensively discussed in academic and government fora, such a move does not appear likely right now. Rather the contrary, with just to mention a few examples including worsening relations between Washington and Moscow, Pakistan developing a sea-based deterrent, and Japan increasingly pondering the convenience of at the very least retaining a powerful “latent” capability on the face of a resurgent China.

The UK is experiencing growing tensions with an established nuclear power, Russia, which shows no intention of relying on non-conventional weapons to a lesser extent in the near future. More precisely, Russian sources note how not until current military reforms reach a successful conclusion will the country be able to lessen her dependence on tactical nuclear weapons (seen as essential not only in a Euro-Atlantic context, but also in a Chinese one, although the latter is seldom publicly discussed). Even without taking into account other potential conflict scenarios, this provides a powerful incentive to retain Trident or some other form of nuclear deterrent, since otherwise the UK would not only be open to nuclear blackmail but the decision to forego the country’s nuclear status may be seen as a sign of weakness and lack of resolve.
Cyber and Undersea Unmanned Threats to the UK’s Minimal Posture
As already explained, the decision to build a sea-based deterrent rested on the assumption that it would be very difficult for a hostile power to detect and destroy submarines, thus ensuring a second-strike capability. This also allowed London to move to a minimal posture, with just one such submarine on patrol at any given time. Of course, it was noted that while “No sector of a superpower’s defense system is quite so invulnerable against a preemptive attack as its fleet of highly mobile, deep-diving, long-ranging missile-bearing submarines. These make possible a second-strike capability that acts as a forceful deterrent against aggression,” and, “this situation could become unbalanced through the development of effective techniques of strategic antisubmarine warfare (ASW).” In recent months, a public debate has emerged concerning two possible threats against British strategic nuclear submarines: cyber warfare and the advent of unmanned undersea systems (submarine drones).
In November 2015, Lord Browne of Ladyton, former British Defence Secretary from 2006 to 2008 and now vice-chair of pro-disarmament group Nuclear Threat Initiative, said: “The government … have an obligation to assure parliament that all of the systems of the nuclear deterrent have been assessed end-to-end against cyber attacks to understand possible weak spots and that those weak spots are protected against a high-tier cyber threat. If they are unable to do that then there is no guarantee that we will have a reliable deterrent or the prime minister will be able to use this system when he needs to reach for it.” Browne cited a January 2013 report by the Pentagon’s Defense Science Board to support his views. Just one week earlier, Chancellor George Osborne had announced an additional investment of £ 3.2 billion in cybersecurity over a five-year period, an amount coming “nowhere near the scale of the cyber-threat challenge” according to Browne.
Franklin Miller, a former U.S. defense official involved in nuclear policy between 1981 and 2001, refuted Browne’s arguments, saying that “If our nuclear command and control system depended upon the internet or went through the internet then the report by the defense science board would be quite an important warning. However, for those reasons it is a standalone system. It is air-gapped. It does not go through the internet.” Miller added that the 2013 report cited by Browne had been written in 2013 as a “shot across the bow” to members of the U.S. defense community thinking of having some elements of the next generation command and control system for the U.S. nuclear deterrent connected to the internet. He said “I am very comfortable saying that right now our command and control system is insulated from cyber-attack because it doesn’t go into any place that cyber would intrude.”
Concerning swarms of undersea drones, the concept is gaining traction as a possible threat to strategic submarines, even though the technology is still in its early stages. The U.S. Navy is already moving forward in this arena with plans to deploy unmanned underwater vehicles (UUVs) from Virginia-class attack submarines. In December 2015, Paul Ingram, BASIC’s chief executive, warned that progress in underwater drone technology threatened to make Trident submarines vulnerable, in line with other experts who have cautioned about “a revolution in underwater drones, as well as advances in sonar, satellite and other anti-submarine warfare systems” making “even totally silent submarines … likely to become detectable.” Ingram said that “There is a major transition taking place in the underwater battle space and it is far from clear how the new submarine will be able to evade detection from emerging sophisticated anti-submarine warfare capabilities.” Adding that this “raises serious questions about the wisdom of putting all your nuclear weapons on board a submarine,” Ingram called for a public debate on this impending vulnerability.
Despite much interest among major navies, underwater drones are being developed at a much slower pace than their aerial counterparts, an often cited reason being water’s much greater opacity to radio waves. According to Frank Herr, head of the Office of Naval Research’s ocean battlespace sensing department, “Underwater vehicles are much harder to do because of this inability for us to communicate robustly with the vehicles the way you can in the air. That means they are way behind in the development.” Chris Rawley, a surface warfare officer in the U.S. Navy Reserve, believes that “the premise that UUVs will make Tridents more detectable glosses over of the complexities of ASW. The physics of underwater sound propagation don’t change just because we take the man out of the loop. Unmanned systems can potentially put more persistent sensors in the water column, but I’d guess we’re at least two decades out from them making a significant impact on ASW.” Rawley discusses this in more detail in a 2015 interview with CIMSEC.
Could Trident’s Cost be Cut by Reducing the Number of Submarines?
In the run-up to the July 2016 parliamentary vote to renew Trident, some voices, including the Liberal Democrats (the Conservatives’ junior coalition partner in the previous administration) and Labour, the main opposition party, suggested or at least speculated on the possibility of reducing the cost of Trident by cutting down the number of boats from the current four. The Liberal Democrats, which open the section in their website on Trident with harsh words, calling it “out-dated and expensive. It is a relic of the Cold War and not up-to-date in 21st century Britain,” while arguing that “It would be extremely expensive and unnecessary to replace all four submarines, so we propose to replace some of the submarines instead. They would not be on constant patrol but could be deployed if the threat from a nuclear-armed country increased.” BASIC included the option of “irregular undisclosed patrolling patterns” in its 2015 “A Memo to the Next Prime Minister: Options Surrounding the Replacement of Trident,” estimating the potential yearly savings at up to 1 billion. Right now, as emphasized by the Royal Navy itself “One of the Navy’s four strategic submarines is always on patrol, ensuring a continuous at sea deterrent, 24/7/365, carrying the nation’s ultimate weapon somewhere in the Seven Seas.” It is very doubtful whether fewer than four submarines could achieve this objective. The need to keep four submarines has been emphasized by many observers, with for example Simon Michell writing for RUSI that “if the United Kingdom is to have a credible and assured nuclear deterrent based on the submarine-launched Trident missile, then four boats are required, not three.” Therefore, it is plausible, should the cost of Trident be considered to be excessive, to move to another kind of deterrent, for example air-based, rather than relying exclusively on a number of boats too small to ensure a consistent deterrent.
Having fewer than four nuclear boats may not only deliver smaller savings than straight arithmetic may suggest given factors such as economies of scale, but would result in gaps in the deterrent with no submarine patrolling at certain given times. This may be seen by a would-be aggressor as providing a window of opportunity. Furthermore, it could be destabilizing in many ways. For example, during a crisis at a time with no boats on patrol, the knowledge that one was soon to sail may be seen by the other side as providing an incentive to strike first. It may also be interpreted as a hostile move, a step in escalation designed to increase pressure. The Trident Alternatives Review, as an exercise in coalition politics, did not rule out this possibility, while failing to discuss in depth the possibility of a sudden unannounced nuclear attack, but nevertheless gave some clues as to why three boats, as opposed to four, would mean accepting a higher degree of risk that such an attack may take place. Where the Review was crystal clear was in explaining that “Over a 20 year period, a 3-boat fleet would risk multiple unplanned breaks in continuous covert patrolling as well as requiring regular planned breaks for maintenance and/or training. Experience to date with the Resolution-class and Vanguard-class SSBNs is that no such breaks have occurred or been required with a 4-boat fleet.” Thus, we can see how lacking the capacity for continuous patrols not only means the deterrent is not always available but also introduces a new factor in an adversary’s calculus during crisis, opening up different venues of speculation concerning the possible motivations for the start and end of deterrence patrols.
Nuclear Alternatives to Trident: Long-Range Bombers
The UK may remain a nuclear power while shifting to other vectors for the country’s warheads. This may result from different motivations, such as cost calculations, a changed perspective on submarine survivability, or the desire for greater strategic autonomy vis a vis the United States, among other few possibilities. Shifting to another delivery method would have a wide range of implications, not only in terms of range, survivability, domestic politics, credibility just to name a few, but for example, inter-service considerations. Trident underscores the Royal Navy’s status as the senior service, which any non-naval alternative would not support in the same way.
Air delivery systems may consist of either missiles launched by aircraft, or gravity bombs dropped by them. An air-dropped alternative to Trident was suggested last year by think-tank Centre Forum. In its report, this organization argues that a minimum nuclear deterrent should be able to destroy “ten or more … major urban areas” of a nuclear adversary (it should be noted that British nuclear doctrine does not provide any explicit assurance to non-nuclear weapons states) and that the UK should therefore be able of delivering 30 warheads.” It goes on to say that “This requires a considerably lower level of capability than” that provided by Trident, meaning that “the UK can achieve deterrence with a considerably less capable nuclear weapons system, saving money and contributing to long-term multilateral nuclear disarmament.” Based on this and other considerations, the report suggests that the UK “move to a free-fall nuclear capability based on Lockheed Martin F-35 Lightning II / Joint Strike Fighter (JSF) that the UK is currently procuring and the forthcoming U.S. B61 Mod 12 (B61-12) bombs that will arm NATO nuclear Dual-Capable Aircraft (DCA) from 2020.” It estimates the capital cost of “100 anglicised B61-12s” at “approximately £16.7bn,” a figure that would include a number of additions to current planned capabilities, among them enabling the Queen Elizabeth-class carriers to operate catapult-launched, arrested-landing aircraft (with a wider range than the vertical takeoff variant currently planned) and extra naval assets such as five attack submarines and four type 26 frigates. The text presents this alternative as a compromise bringing about costs savings while enhancing conventional capabilities, preserving the submarine industrial base, and “a concrete step down the nuclear ladder and towards future nuclear disarmament as the international situation allows in accordance with the UK’s nuclear Non-Proliferation Treaty obligations.”
Given the UK’s global role and the duty to protect British Overseas Territories, any nuclear alternative to Trident should have an equivalent range. This may be a challenge for nuclear bombers, less so for submarine-launched cruise missiles, and would not apply to land-based ICBMs (intercontinental ballistic missiles). The travails of strategic bombers when targets are far from bases were already illustrated in the Falklands War, where the strike against Port Stanley’s airport required the complex coordination of a very large number of aircraft operating from Asuncion Island. The Centre Forum document argues that a combination of existing overseas bases and “Air-to-Air Refueling (AAR) support from RAF Voyager KC2/KC3 tankers covers all of Africa, Europe, the Middle East and South America, along with the Indian subcontinent and most of former Soviet Central Asia.” Leaving aside the fact that this would not cover all existing nuclear weapons states, the sheer complexity of the necessary AAR operations to reach some corners of the world may put a dent on the deterrent’s credibility, tempting a would-be aggressor into thinking it may not ensure a British response. This was noted by a commentator, who wrote “Where the credibility gets shaky is in the delivery. A Voyager tanker can trail 4 fighter jets for 2800 miles in a transfer flight, but an actual strike mission, especially if a return to base is at least envisaged, is a whole different matter. Even bringing all 14 tankers in service (instead of just 8 + 1 transport only and 5 tankers “on demand” at 90 days notice) and fitting them with booms and receptacles so they can juggle fuel between themselves and work cooperatively, it remains dubious that it would be possible to trail a real strike package over the great distances likely to be involved. Particularly because, in order to deliver the strike with gravity-fall bombs with a stand-off reach of 40 kilometers in the very, very best case, you need a large attack squadron, knowing that many aircraft are likely not to make it to the target, even with the F-35’s stealth.”

This text also questions whether it is realistic to expect the UK to sport 72 ready-to-strike nuclear bombers at any one time, as the Centre Forum defends when it states that “Using the 18 airfields shown in Figure 5 today, this would translate into 72 nuclear-armed F-35Cs and their accompanying Airbus Voyager KC2 / KC3 tankers safely airborne before a surprise attack could destroy them on the ground.” Furthermore, it argues that if that number was indeed available it would put such a dent on conventional capabilities as to make the whole exercise self-defeating. These unrealistic assumptions cast a shadow of doubt over the Centre Forum’s proposal, and prompt suspicions that it may have been designed, or at least have been liable to being employed, to underpin a tactical deal between those opposed to British national sovereignty and the country’s independent deterrent on the one hand, and those concerned about continued conventional defense cuts, on the other. By offering the acquisition of additional conventional assets as part of a package deal involving the replacement of Trident by a less able system, the former may have hoped to achieve the necessary political momentum against Trident, assembling a coalition with the latter and perhaps also other actors like the SNP. At a later stage, with Trident out of the way, the door would have been open to further conventional cuts degrading an already less than credible deterrent, thus achieving unilateral nuclear disarmament through the back door.
Other disadvantages of a naval aircraft-based deterrent are, in the words of an undisclosed naval analyst, that “a ship is ALWAYS more vulnerable than a submarine” and a “plane can also be downed,” plus the fact that adding a further role to a carrier means an additional concentration of risk and incentives for the enemy to try to sink her. Operations by HMS Hermes and HMS Invincible off the Falklands, at a time when anti-access weapons were much more primitive (Argentine forces improvised a shore-launched Exocet missile, hitting HMS Glamorgan, but it was not available until very late in the war), illustrate the complications of sailing near a hostile shore, which would have been even greater had the British deterrent been based on those same two light carriers. At the end of the day, considering all these aspects, it is difficult not to see that moving from submarines to carrier-based planes would mean a significant downsizing of the British deterrent, with the corresponding negative impact on national security. In the words of another author, “A nuclear deterrent based on the B61-12 would be much less capable than Trident, this is definite. The key issue is not the power of the warhead, but the certainty that an enemy anywhere in the world can be reliably hit. Any possible existential enemy of the UK must be keenly aware that there is a credible deterrent which is unquestionably able to strike back and make him pay a price which cannot be possibly accepted.”
As noted later when discussing air-launched cruise missiles but equally applicable here, “The UK would be faced with the choice of having to keep nuclear-armed aircraft permanently in the air (where they would still be visible) or risk having the air base – and its neighbouring community – as the target for a nuclear strike by a potential adversary.”
Things may be different if a long-range bomber powered by Reaction Engines’ SABRE (Synthetic Air-Breathing Rocket Engine) is developed in the future, since such aircraft would be able to strike at any target without aerial refueling. It must be noted, though, that any such dual-capable (nuclear and conventional) bomber may prompt the same concerns over strategic instability which have pushed Washington to withdraw nuclear Tomahawk cruise missiles from service, which we discuss in this series’ final part.

Nuclear Alternatives to Trident: Land-Based Missiles
The deployment of land-based missiles involves at least two problems. First, they are considered to be the most vulnerable asset in the nuclear triad, given their fixed location. To overcome this vulnerability, an alternative may be to deploy missiles on either trucks or trains, ideally camouflaged as ordinary vehicles, but since this alternative has not featured in the debate on the replacement of Trident (in contrast with Russian work in this area) we shall not examine it in detail here.
Second, the construction of the necessary infrastructure may pose legal (land planning) and political complications. As noted in the 2015 RUSI conference on missile defense, it is precisely these legal and political difficulties involved in deploying certain land-based assets that make a naval missile shield the most realistic alternative for British plans on national BMD (ballistic missile defense). Additionally, as discussed when dealing with cruise missiles, developing a new vector would involve significant time and treasure.
In our next and final installment in this series, we will look at other possible alternatives to trident, including both air and submarine-launched cruise missiles. This will include an examination of their technical aspects, as well as wider economic and policy issues. In the case of submarine-launched nuclear missiles, this includes the risk of confusion with their conventional brethen. Last, we will examine a very different scenario, namely the UK as a Japanese-syle ‘latent’ nuclear power. Stay tuned!
Alex Calvo, a former guest professor at Nagoya University (Japan), focuses on security and defence policy, international law, and military history, in the Indian-Pacific Ocean Region. He tweets at Alex__Calvo and his papers can be found at https://nagoya-u.academia.edu/AlexCalvo Previous work on British nuclear policy includes A. Calvo and O. Olsen, “Defending the Falklands: A role for nuclear weapons?” Strife Blog, 29 July 2014.
Featured Image: The Trident nuclear submarine HMS Victorious is pictured near Faslane in Scotland. (UK Ministry of Defence)