Maritime Cybersecurity Topic Week
By Mark McIntyre and Joe DiPietro
Technology Disruption
Just as the sextant enabled celestial navigation of ships far from shore, and signal flags and lights allowed ships to communicate with one another more effectively, the adoption of digital technology has allowed sailors to shoot, move, and communicate even more rapidly. While this technology allows seafarers to navigate more precisely and communicate and coordinate with others more easily, it introduces new vulnerabilities to modern warships. Just as these systems assist personnel onboard ships, they potentially offer nefarious actors an attack vector to introduce malicious code into these systems.
Cyber is the ultimate domain for threat actors, providing strategic and regional adversaries alike with an effective way to target otherwise formidable platforms. We should expect to see more activity in the coming years from aspiring regional actors who aspire to project power, elevate their geopolitical stature – and perhaps make some money while they are at it – without incurring the major expenses of maintaining or surging military forces and materiel.
Advanced threat actors have proven their ability to take advantage of domestic and international supply chain complexities and dependencies, exploiting governments’ troubling dependencies on legacy information technology infrastructure and bureaucratic inefficiencies. In short, attackers will remain quicker and more adaptable than defenders for the foreseeable future. While we have traditionally envisioned naval engagements with ships, planes, and missiles interacting with one another, we need to expand our aperture to anticipate adversary efforts to attack our shipboard systems through cyber operations.
Data Explosion and the Future of IoT
A core mission of most western navies is to protect shipping lanes for energy and commerce. Given global commerce’s increasing reliance on digital technology, then surely navies will see their mission set expand to include protecting—or exploiting—global digital transmissions and understanding what all that data means. Further, with information and operational technologies converging rapidly, the United States and its allies must rethink traditional mindsets that separate investments in physical infrastructure and fleets from the underlying technologies that will increasingly power and manage them, and the associated mission systems on board. With the need to forward-deploy computing power and infrastructure around the world, often on short notice, vessels may in the future be better characterized as floating datacenters that happen to hold traditional weapons systems. As maritime operations evolve around technology futures that increasingly rely on computing systems and data, and as long as data remains attractive to adversaries, the need for cybersecurity defenders will only grow.
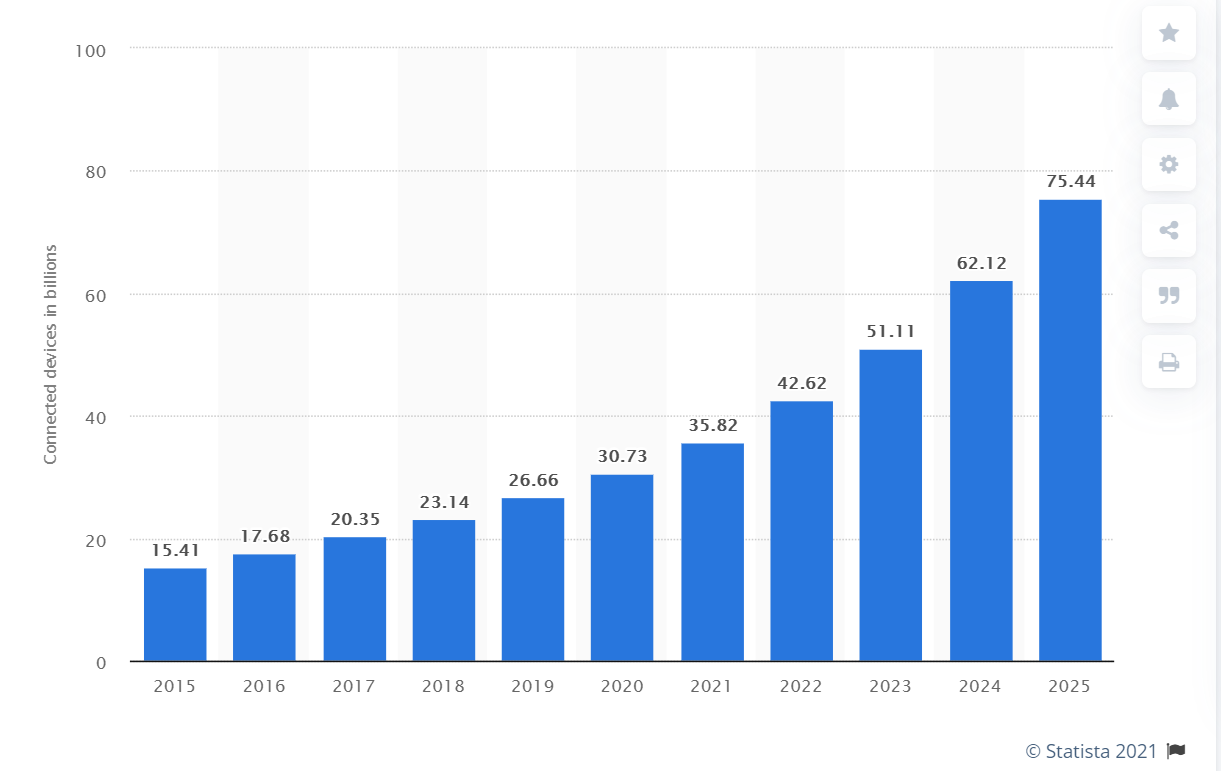
Data, as we hear, is the ‘new oil.’ Over 90 percent of the world’s data has been created in the last five years. We are using terms like ‘zettabytes’ now, and organizations are creating ‘chief data officer’ roles and data-specific enterprise strategies. Depending on the specific study, the growth rate for Internet of Things (IoT) devices is far exceeding that of traditional laptops, cell phones, and tablets. Over 30 billion devices are projected to be deployed by the end of 2021. IoT devices are used for specific applications that span many industry segments. As we look for the public sector application, a vast majority are in the “Industrial IoT” device segment below. There are many reasons for this growth, but the cloud increases application-specific value at a tremendous rate. There are other terms like Digitalization, Industry 4.0, and the Fourth Industrial Revolution, but they all embody the following characteristics that digitalization is creating:
- more complex systems to support the growing efficiencies needed to protect critical infrastructure through automation
- the ability to respond much quicker, and with greater accuracy, to operational threats
We are already seeing the introduction of autonomous drones, body-worn devices such as HoloLens augmented reality headsets, predictive maintenance sensors on engines or manufacturing devices, physical security and life control devices, and even connected installations. It is not science fiction to envision an operating environment where everything is connected and where all data contains hidden meaning that, left uncollected, constitutes an intelligence or mission failure. It is already happening.
The Cyber Workforce
Success or failure in leveraging data and devices will depend upon humans, especially our information technology and cybersecurity defender teams. Because humans maintain and interact with these systems, we will long remain the primary target of adversaries. It is imperative that future technology adoption begins with recognizing the foundational importance of workforce readiness.
Commercial enterprises and governments alike are struggling to properly prepare their cyber defender workforce to adapt to new threats and take advantage of new security technologies. Many cyber defense teams grew up in an exclusively on-premises environment and are only now developing the beginnings of a cloud-native skillset. In addition, and of greater concern, we are not positioned to close the talent shortage in cybersecurity which some analysts estimate to be between two and three million unfilled positions. Technology providers are making impressive advances in creating cyber tools and solutions, but in doing so we have created what Gartner calls a “digital dexterity gap” where we are innovating at a much faster rate than customers—especially governments and warfighters—can absorb.
There is also an inverse relationship in play, according to one global CISO (Chief Information Security Officer) survey, where humans account for 95 percent of data loss incidents, while only around 1.5 percent of CIO (Chief Information Office) budgets is allocated to workforce cybersecurity readiness. We simply are not investing enough in teaching the workforce—from leadership to the newest recruit—how to operate safely online. Role-based readiness is critical to help users fully understand the risks of phishing and other attacker activities.
We are also dealing with the troubling signs of analyst fatigue where cyber defenders are simply burning out. If we see the future of maritime operations and cybersecurity as built around cloud-powered big-data systems and ubiquitous computing, then we must do better at providing the right proactive learning and onboarding experiences to give our people, especially cyber defenders, a fighting chance.
The future of maritime operations, much like other public sector and commercial endeavors, is where information technology, data, and devices converge. We should expect continued cyber-attacks against national infrastructure and military platforms. This will be happening amidst continual technological innovation designed to capture and make use of massive amounts of data, which will be protected by outnumbered and beleaguered security practitioners who will often not be properly trained to employ emerging technologies to counter threats.
Gamified Learning
Due to a variety of factors, including perceptions of slow technology adoption and the spartan demands of military service, defense ecosystems are particularly vulnerable to the cyber workforce talent shortage and readiness challenge. Building tomorrow’s cyber workforce is a fundamental societal challenge that requires governments, industry, academia, and communities to work together to attract and prepare individuals for cybersecurity careers.
One potential solution to this challenge lies in taking advantage of cloud-hosted cyber ranges. Providers in this sector are currently ahead of the market, but they are on to something that will be increasingly critical for military cyber defenders: force-on-force training in a gamified learning environment.
A cloud-based cyber-range provides an immersive, scenario-driven training environment that mimics real-life threats, responses and has proven applicability to Red and Blue team training, security awareness training, certification-path training, and proficiency examination. This learn-by-doing approach offers students a realistic experience to think like attackers while competing against one another in a gamified cyberspace environment. Simulated breach environments, sandboxed from operational enclaves but modeled to resemble real environments, help prepare an enterprise’s workforce for the stress, panic, and communication barriers they will face during a real cyberattack.
This sort of gamified learning introduces interactive, video game-like experiences that naturally attract younger talent and competitive personalities, and this approach has already been shown to improve student retention compared to traditional classroom learning. Intuitively, this is obvious: we must make learning fun and competitive. Independent studies reveal that students retain only around 10 percent of what they learn in a traditional classroom. After one month, by contrast, gamified learning flips that number, with retention at around 80-90 percent.
For defense organizations that may struggle to attract and retain talent, these cyber ranges demonstrate a commitment to investing in employee education and career advancement and meeting younger people where they live—online, using devices. Since future force development will require some level of IT acumen, this is an excellent chance to address hiring profiles and optimize recruitment pipelines. Cloud-based cyber range platforms are also highly scalable and will allow defense organizations to reach many more personnel globally than what can be done with traditional learning programs and exercises
Workforce Readiness for Tomorrow’s Defenders
Modern cyber-range platforms are designed to support a broad range of scenarios that may range in user experience from a walkthrough, ‘choose your own adventure’ scenario to ‘open world’ exploration. Naval organizations can create and map skills development themes to operational and IT focus areas to nurture employee interest, gauge readiness, and advance career paths in areas with critical skillset shortages such as:
- Threat hunting
- Capture-the-flag
- Incident investigation
- ‘Live’ incident response and containment
- Failure analysis and cloud troubleshooting
- Malware and memory forensics
- Red-teaming and penetration testing
In addition to practical cybersecurity learning, cloud-based gamified learning can also address more specific naval warfighting and maritime use-cases:
- Wargaming and engagement simulation: run through many different variables and scenarios at much quicker speeds and with more predictive capabilities based on data inputs
- Combat Information Center drills: improve analysis of incoming datapoints and communications
- Systems deployment and maintenance: allowing technicians and other personnel to learn and practice tasks with equipment before actual installation and servicing
- Virtual technology evaluation: accelerating product security evaluations and efficacy for IT and operational teams.
Gamified learning can just as easily be tailored to general IT users and leadership teams, for example with phishing, online safety, and command and control exercises. Everyone can find a role to play. Some cyber range companies are developing very promising avatar or concierge features where advances in ML (Machine Learning) and AI (Artificial Intelligence) provide new employees and seasoned veterans alike with a virtual assistant to help personnel make the right decisions.
Cloud computing offers significant cost and performance advantages for gamified learning. Currently, most training environments are on-premises, requiring significant up-front capital investments in infrastructure and servicing, sometimes over $500k/month for an exercise; and they do not easily scale. Moving range infrastructure to the cloud will allow range providers to focus less on maintaining IT systems and more on providing the actual cyber learning, flipping training budgets from capital investments toward operational investments. Range providers need to get out of managing training infrastructure and environments and focus on providing high-quality, dynamic simulations.
Cloud-based cyber range technology platforms bring scenario-based immersive training and skills development experiences. Developer and IT teams will be able to focus on creating actual learning scenarios that are specific to attacker activities or user-defined use-cases and advance employees’ professional development.
Tomorrow’s Security Operations
The Department of Defense has spent the better part of the last year endorsing and directing components to start adopting Zero Trust architectures as part of a larger fundamental redesign of its networks to better handle modern collaboration demands, such as SaaS applications. This welcome development implicitly acknowledges a pragmatic ‘assume compromise’ posture that managing the usage of technology is inherently a risk management exercise. Zero Trust architecture allows an organization to implement proactive and centralized controls over users, devices, applications, infrastructure, and networks, all with the goal of protecting the most critical asset—data.
When incidents occur, Zero Trust helps minimize the ‘blast radius’ by containing attackers before they can compromise more of the environment. This topology is like a naval vessel, where one will house specific operations in certain compartments and limit access to those by role. Conversely, one can limit the spread of damage to other parts of the ship by sealing access to compartments during emergencies.
Due to the central role that IT will continue to play in a modern warfighting or workplace environment, staying offline is not tenable. In fact, the trends are clearly moving in the opposite direction: more devices, more data, more flexibility, particularly for younger individuals whom constant access to technology is an expectation and therefore a recruitment and retention issue. This is particularly relevant when some analysts suggest that 99 percent of usable intelligence collection will be OSINT, coming from commercial providers.
Cloud-First Platforms
The U.S. Navy’s rapid move toward adapting Zero Trust architecture is encouraging, particularly as it may serve as sort of a reference architecture for maritime partners and allies. It is even more opportune when we factor in the convergence of IT and operational technologies. Most net-new devices that will be deployed in the coming years will not be personal or organizational cellphones or other hand-held devices: they will be operational devices, part of the larger internet of things ecosystem, which will expand into billions of connected devices, all constituting points of intelligence and vulnerability.
From a cybersecurity perspective these devices must be protected, and we must control how we interact with these devices and how they interact with each other. These are already forcing a modernization of traditional security, incident, and event management (SIEM) and security orchestration, automation, and response (SOAR) platforms. Traditional on-premises SIEM/SOAR systems will not be fast or flexible enough to process and analyze incoming data with the exponential increase of data that is already occurring, and which will only accelerate. Technology providers are already moving security appliances to the cloud, and companies like ours—Microsoft—are rapidly deploying cloud-first SIEM/SOAR capabilities. The sooner a user adopts these, the better able they will be to get ahead of the curve on securing and monitoring their data estate. The ML/AI-backed automation built into these platforms will be a huge force multiplier for cyber defenders, taking more mundane tasks off their hands, and allowing analysts to focus more on the alerts and events that really matter.
Supply Chain Futures and Vulnerabilities
The Solorigate incident is a reminder that we as an ecosystem are collectively vulnerable to supply chain compromises. Defense organizations are at particular risk due to the vast networks of suppliers and subcontractors, and because of the long development and operational lifecycles of weapons and other systems, including fleet assets. While we are seeing promising investments in this area, for example around rapid development lifecycles such as ‘comply to connect’ and steady adoption of Platform-as-a-Service software-defined weapons system development, addressing and remediating supply chain dependencies will take years, and will require more flexible attitudes from procurement and contracting.
From a cybersecurity perspective, CISOs are increasingly focused on reducing complexity within their environments, for example by making specific commitments to corporate boards or management committees to standardize more of their security budgets around a core set of (cloud-native) technologies. Complexity is inimical to cybersecurity, meaning legacy and one-off cybersecurity providers will better serve their customers by aligning to large cloud providers’ multibillion-dollar investment strategies. Standardizing around these platforms and deprecating older and more customized tools will also ease the burden on cyber defenders.
Conclusions
Technology and data are agnostic: we use technology to advance mission objectives and we find meaning in ones and zeroes to advance our missions. We are already experiencing fundamental change in how we interact with data and devices, with existential implications for global security and international commerce. We in industry must and will continue to ‘shift left’ and build more cloud-powered and automated cybersecurity capabilities into our larger platforms and ensure that they are interoperable so that allied forces can properly communicate globally. These technologies must also be intuitive and usable so that they enable security operations and not add to the workload.
At the same time, we must work harder and more creatively to attract tomorrow’s cybersecurity talent who we will ultimately rely on to protect the confidentiality, integrity, and availability of national security systems and data. Fortunately, we can harness the same technologies that we will rely on to advance our missions to create more experiential learning that we will need to prepare tomorrow’s cyber workforce.
Mark McIntyre is a Chief Security Advisor in Microsoft’s Security Solutions Area, where he advises US government CISO teams on moving securely to the Cloud and cybersecurity modernization, focusing on areas like Zero Trust, modern identity, and modern security operations. Mark helps CISOs understand Microsoft’s perspectives on the evolving cyber threat landscape and how Microsoft defends its enterprise, employees, and users around the world.
Joe DiPietro has more than 25 years of leadership and hands-on experience with enterprise security leaders including Microsoft, CyberX, IBM, Guardium, and Check Point Software. Within Microsoft, he leads the Global Black Belt team for IoT Security. At CyberX, he was the VP of Customer Success and included both presales and post sales responsibilities.
The opinions in this paper are entirely those of the authors and should not be construed as official Microsoft positions, assessments, or recommendations. Customers are wholly responsible for ensuring their own compliance with all applicable laws and regulations. Information provided in this post does not constitute legal advice, and customers should consult their legal advisors for any questions regarding regulatory compliance.
Featured Image: Sailors stand watch in the Fleet Operations Center at the headquarters of U.S. Fleet Cyber Command/U.S. 10th Fleet at Maryland’s Fort Meade. (Photo by Mass Communication Specialist 1st Class Samuel Souvannason/U.S. Navy photo)

