By Lars H. Bergqvist
As a response to the 9/11 attacks, the International Ship and Port Security code (ISPS) came in to force 1st July 2004. Thus, 10 years have passed, since merchant ships in international trade and the ports they are calling, were required to be certified to a certain security standard.
Background
Most legislation in the maritime world is initiated by some kind of maritime disaster or accident. The Titanic catastrophe, where many passengers and crew members perished due to the fact that there were not enough lifeboats, gave birth to international safety regulations.(1) The MARPOL-convention came in to force a few years after a serious oil pollution, caused by the grounding of the tanker Torrey Canyon on rocks near the Isles of Scilly.(2) Further, despite proper rules and regulations, a very high number of accidents caused the International Maritime Organization (IMO) to implement the International Safety Management Code (ISM).(3)
Contrary to previous conventions and codes, the creation of the ISPS-code was caused by a disaster that happened ashore, when hijacked aircrafts on the 11th of September 2001 flew into the twin towers of the World Trade Center, destroyed part of Pentagon and crashed on a field in Pennsylvania.
In peace time, to facilitate trade, merchant ships have traditionally been entering territorial waters and ports without much hindrance. The embarkation of port authorities, with clearance and free pratique granted has occurred once the ship was alongside a berth or at a customary anchorage.
With such an easy access to seaports, security experts were of the opinion that merchant ships could be used as a tool by terrorists. Different scenarios were developed, where merchant ships were means of transportation of terrorists and their weapons, or that the ship in its own right was a weapon. An example given was the risk of gas ships being hijacked and blown up in busy seaports.
Urgently, legislation was needed to protect both merchant ships and seaports.
Implementation
At a Conference of Contracting Governments to the International Convention for the Safety of Life at Sea (SOLAS), held at IMO headquarters in December 2002, The International Ship and Port Facility Security Code was adopted.
A code written and adopted, just in little more than one year after 9/11, must have been some kind of record. The time period from adoption to enforcement was also very short, only 18 months had passed when the Code came into force on the 1st of July 2004.
During that one and a half year some 50,000 ships were certified, and hundreds of thousands of seafarers and office personnel were educated for their new roles as Ship Security Officers (SSO) and Company Security Officers (CSO). An equally daunting task, port facilities on all continents, with personnel, should be certified and educated.
However, extraordinary times demand extraordinary measures and with a concerted effort from all stake holders in the shipping industry, the ISPS-code was properly enforced.(4)
What is maritime security?
Maritime security has always been a part of commercial shipping. Piracy is as old as shipping itself and stowaways is hardly a new problem either. During wars, the merchant marine has been an integral part of the war effort, being a vital support line for warring nations in need of weapons, food, oil and other commodities.(5)
Thus, war, piracy and stowaways are threats that the shipping industry has been dealing with for a long time. Administrations and ship owners´ associations have for decades been issuing regulations and instructions in an attempt to assist seafarers to deal with the perils.
For example, during the cold war, all Swedish ships were by the Swedish Maritime Administration issued with an instruction about how to act during crisis and war.
Some 30 years ago, with the appearance of modern piracy, the International Maritime Organization(6) and the International Chamber of Shipping(7) issued guidelines.
In 1957, an international convention relating to stowaways was adopted, although not yet in force (8), and there are policies issued about how to deal with stowaways.(9)
However, any specific instructions, how to protect a ship against terrorists, prior to the ISPS-code, were never issued. The Convention for the Suppression of Unlawful Acts against the Safety of Maritime Navigation, which was agreed upon after the spectacular hijacking of Achille Lauro, was only addressing punishment of acts that could threaten the safety of maritime navigation.(10)
Maritime terrorism before ISPS-code (before 1 July 2004)
The Council for Security Cooperation in the Asia Pacific(11) has offered an extensive definition for maritime terrorism:
“…the undertaking of terrorist acts and activities within the maritime environment, using or against vessels or fixed platforms at sea or in port, or against any one of their passengers or personnel, against coastal facilities or settlements, including tourist resorts, port areas and port towns or cities.”
Similar to the ISPS-code, not only ships are considered as objects for maritime terrorism, but also port facilities.
Maritime terrorism is not rampant, nevertheless there have been a steady flow of incidents during the last 50 years. The Global Terrorism Database (GTD) at the University of Maryland(12) is an open-source database on global terrorist incidents (including maritime), covering events from 1970 through 2012.
From 11th June to 1970 to 1st July 2004, there were 212 maritime terrorism incidents. However, most of those incidents were on rather low level, like the incident with GTD ID: 200112120005; “12/12/2001: Members of People’s Revolutionary Army (ERP) set up an illegal checkpoint along the Cauca River near Magangue, Sucre, Colombia. The rebels stopped a canoe traveling along the river and abducted nine of the passengers. Three people were released the next day. Specific motive is unknown.”
Still there are some significant incidents that got an extensive media coverage.
– Santa Maria: The hijacking of the Portuguese passenger ship Santa Maria is considered to be first case of maritime terrorism. On January 22, 1961, 24 leftist Portuguese terrorists hijacked the luxury cruise liner. The ship was carrying 600 passengers and a crew of 300. The would-be hijackers embarked the vessel as passengers at the port of La Guairá in Venezuela and on the Dutch island of Curacao, with weapons hidden in their suitcases. The terrorists took over command of the vessel, but eventually surrendered when they were given political asylum in Brazil.(13)
– Sounion: A few years prior to the outbreak of the civil war in Lebanon, in March 1973 the Greek passenger ship Sounion sunk in the port of Beirut. A limpet mine was attached to the ship`s hull by Palestinian terrorists while ship was in dock, with the aim of blowing up the ship once at sea. Due to the interference of a Swedish undercover agent based in Lebanon, the departure was delayed, passengers could disembark and the ship sunk while still alongside the berth.(14)
– Shadow V; A fishing boat owned by the former First Sealord and last Viceroy of India, Lord Mountbatten. In September 1979, while onboard the boat in waters near his summer home on Ireland, a bomb planted by the Irish Republican Army exploded and killed him.
– Rainbow Warrior; A Greenpeace ship sunk by the French foreign intelligence service in the port of Auckland, New Zealand, July 1985. Not an act of terrorism as such, but two French secret service agents was found guilty and sentenced to ten years in prison by the New Zealand court of law.
– Achille Lauro; InOctober 1985,the passenger ship while on a cruise in the Mediterranean, was hijacked by four terrorists from Palestine Liberation Front, off the coast of Egypt. After only two days of negotiation, but after they had killed an elderly American passenger, the hijackers gave up when they were promised political asylum in Tunisia. However, justice was swift, as US warplanes forced the Egyptian airliner carrying the hijackers to land in Italy.
As a result of the hijacking, the Convention for the Suppression of Unlawful Acts against the Safety of Maritime Navigation (SUA) was developed and adopted.
– The Tanker War; With something that can be refer to as state terrorism, both sides attacked shipping in the Persian Gulf, mainly tankers, during the Iran-Iraq war between 1980 and 1988. According to sources more than 400 seamen were killed and 340 ships were attacked, during the conflict.(15),(16)
– The Tamil Tigers; During the civil war between the Sri Lankan government and the Liberation Tigers of Tamil Eelam, the latter was involved in maritime terrorism with its Sea Tigers brigade. The brigade was accused of hijacking several vessels in waters off the coast of Sri Lanka, including Irish Mona (in August 1995), Princess Wave (in August 1996), Athena (in May 1997), Misen (in July 1997), Morong Bong (in July 1997), MV Cordiality (in Sept 1997) and Princess Kash (in August 1998).(17) One spectacular act of maritime terrorism was the suicide attack on the tanker Silk Pride. (18)
– USS Cole; Although a warship, the modus operandi used by the attackers was kind of a harbinger, when in October 2000, a small craft laden with explosive commanded by Al Qaeda suicide bombers hit the US Navy destroyer. The attack killed 17 sailors and wounded another 42.
– M/T Limburg; In October 2002, the French owned crude oil carrier was attacked when approaching an offshore terminal off the coast of Yemen. An explosive-laden boat rammed the hull of the tanker, causing an explosion followed by fire.(19)
– Superferry 14; Regrettably, the ferries of the Philippines have a very bad safety record. Also, the maritime security record has been tarnished. The February 2004 terrorist attack on
Superferry 14 caused the death of 116 persons.(20) Suicide bombers from the Al Qaeda linked
Abu Sayyaf group, using a boat loaded with explosives, were the perpetrators.
Maritime terrorism after ISPS-code (after 1st July 2004)
Supporters of the ISPS-code may argue that the code has been successful since there have been no serious maritime terrorist attacks since the implementation.
Detractors may argue that the code did not help much in protecting seafarers against the menace of modern day piracy.
Whatever opinion someone may have, the code was developed to protect the international community against terrorism, and as such it has been a success. Piracy and terrorism are different crimes, needing different approaches. And, according to conventional wisdom, the link between terrorist and pirates is very weak.
Although a positive impact on the security situation by the Code, there have been some serious incidents.
– Don Ramon; The second maritime terrorist attack by Abu Sayyaf took place in August 2005 onboard the passenger ship Don Ramon in Filipino waters. Terrorist had placed a timed bomb beneath gas cylinders in the ship`s galley, causing the ship to sink and wounding 30 passengers.(21)
– M Star; In July 2010, the Japanese owned very large crude oil carrier experienced an explosion when transiting the Strait of Hormuz. Although no craft was sighted, the explosion made a large dent in the hull, parts of accommodation were slightly damaged and one crewmember was injured. After two days, the terrorist group Brigades of Abdullah Azzam claimed responsibility.(22)
– Yemen, level 3; In August 2013, due to a high level of activity by Al Qaeda affiliated groups in Yemen, the Government of United Kingdom raised the ISPS security level to level 3 for British flagged ships in Yemeni territorial waters. A serious situation indeed, since an elevation to level 3 was unprecedented since the ISPS code was introduced in 2004.(23)
– Cosco Asia; In September 2013, while on transit in the Suez Canal, the Chinese owned container vessel under the flag of Panama, was hit by a rocket propelled grenade. The ship sustained only minor damages, and there were no casualties. An Islamist group named Al-Furqan claimed responsibility for the attack.(24) Although a minor attack, it was of great concern for the Egyptian government, due to the economic importance of the Canal. To increase security, a protective wall along the Canal is in the process of being constructed.(25)
The future of the code
Like with all new regulations, ISPS-code was initially met with some skepticism from the end users, i.e. the seafarers. However, the code is now an accepted part of shipping, and the advantages are being appreciated.
Obviously, the code can be modified to the better, by catering more for the threat of piracy and stowaways that are much more of real threats than terrorism.
IMO has listed some of the remaining challenges; (26)
- Lack of national legislation/guidelines on ISPS code implementation.
- ISPS code as a mean to address all maritime security threats.
- Deciding on an appropriate risk assessments methodology.
- Dissemination of good practices on port facility security.
- Who audits the auditor?
- Ships` encountering difficulties after calling a high-risk port.
Lars H. Bergqvist is a Swedish master mariner and a reserve officer in the Royal Swedish Navy.
Footnotes
- http://www.imo.org/KnowledgeCentre/ReferencesAndArchives/HistoryofSOLAS/Pages/default.aspx
- http://www.imo.org/KnowledgeCentre/ReferencesAndArchives/HistoryofMARPOL/Pages/default.aspx
- http://www.admiraltylawguide.com/conven/ismcode1993.html
- http://www.imo.org/ourwork/security/instruments/pages/ispscode.aspx
- Sometimes referred to as “The Fourth Service”.
- Resolution A.545(13), “Measures to prevent acts of piracy and armed robbery against ships.” http://www.imo.org/blast/blastDataHelper.asp?data_id=22356&filename=A545(13).pdf
- International Shipping Federation/International Chamber of Shipping published in 1986 the first edition of “Pirates and Armed Robbers: A Master’s Guide.”
- International Convention Relating to Stowaways 1957 (“Brussels Convention”).
- http://www.itfseafarers.org/files/seealsodocs/453/Stowaways.pdf
- http://www.imo.org/About/Conventions/ListOfConventions/Pages/SUA-Treaties.aspx
- http://www.cscap.org/
- http://www.start.umd.edu/gtd/
- http://www.maritimeprofessional.com/Blogs/Maritime-Musings/December-2011/Hijacking-of-the-SS-Santa-Maria.aspx
- http://jcpa.org/article/mikael-tossavainen-on-theyll-die-anyway-ten-years-in-the-swedish-intelligence-service/
- war http://www.amazon.com/Tanker-Wars-Iran-Iraq-1980-1988-International/dp/186064032X
- http://csis.org/files/media/csis/pubs/9005lessonsiraniraqii-chap14.pdf
- Dr Vijay Sakhuja, South Asia Analysis group, SEA PIRACY IN SOUTH ASIA
- http://edition.cnn.com/2001/WORLD/asiapcf/south/10/30/slanka.tiger.attack/
- http://www.globalsecurity.org/security/profiles/limburg_oil_tanker_attacked.htm
- http://www.hrw.org/reports/2007/philippines0707/background/2.htm#_Toc168986107
- http://www.kcl.ac.uk/sspp/departments/dsd/research/researchgroups/corbett/corbettpaper8.pdf
- http://www.theguardian.com/world/2010/aug/06/japanese-oil-tanker-terrorist-explosives
- http://www.rederi.no/nrweb/cms.nsf/($all)/AE4BD4693E6CD476C1257BC00026E77C?OpenDocument&qnfl=Nrprint
- http://news.usni.org/2013/09/05/video-terrorists-rocket-commercial-ship-suez-canal
- http://www.skuld.com/topics/voyage–port-risks/port-news/africa/egypt-construction-of-security-wall-along-the-suez-canal/
- http://www.seasecurity.org/wp-content/uploads/IMO-Presentation-SAMI-PORT-SECURITY.pdf
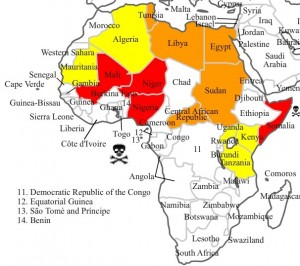

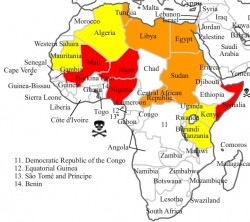

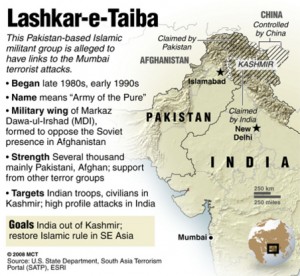




 One of the most vexing questions in international law is determining under what circumstances a state may lawfully use military force against another state or non-state actor. The U.N. Charter takes a very conservative approach: use of force, according to Article 51, is authorized “if an armed attack occurs against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security.”1 The international community has long since abandoned the notion that a state must wait until it is actually under attack before it can employ military force. Instead, the concept of “imminence” has been read into Article 51. Daniel Webster famously articulated this rule after the so-called Caroline case: preemptive force can be used only if there is “a necessity of self-defence, instant, overwhelming, leaving no choice of means, and no moment of deliberation.”2 But even this more deferential rule has proven unworkable in the age of modern warfare.
One of the most vexing questions in international law is determining under what circumstances a state may lawfully use military force against another state or non-state actor. The U.N. Charter takes a very conservative approach: use of force, according to Article 51, is authorized “if an armed attack occurs against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security.”1 The international community has long since abandoned the notion that a state must wait until it is actually under attack before it can employ military force. Instead, the concept of “imminence” has been read into Article 51. Daniel Webster famously articulated this rule after the so-called Caroline case: preemptive force can be used only if there is “a necessity of self-defence, instant, overwhelming, leaving no choice of means, and no moment of deliberation.”2 But even this more deferential rule has proven unworkable in the age of modern warfare.