Robin Geiss and Anna Petrig. Piracy and Armed Robbery at Sea: The Legal Framework for Counter-Piracy Operations in Somalia and the Gulf of Aden. Oxford University Press, 2011. 340 pp. $110
By Alex Calvo
The Law of Counter-Piracy Operations: From Hollywood films to some Chinese popular perceptions of their Eastern neighbors, piracy and pirates retain a powerful hold in contemporary culture. However, it is their most recent incarnation in areas like the Gulf of Guinea, the Malacca Straits, and the Horn of Africa, that is carefully followed by anybody involved in maritime affairs, from ship owners and operators to naval officers and international lawyers. Among other aspects of piracy, the legal regime of pirates and operations against them is of the foremost importance, and therefore any volume devoted to them proves a welcome addition to the literature on the sea and what Julius Caesar labeled as “hostis humani generis,” or the enemies of humankind. This is exactly what Piracy and Armed Robbery at Sea purports to be, and actually is: a single-volume treaty on the law applicable to counter-piracy operations, with a regional focus on Somalia and the Gulf of Aden. The book achieves the goals of providing a comprehensive approach to the subject, with plenty of primary sources, case law where applicable, and legal commentary on controversial or unclear aspects. While readers may note the absence of topics such as the rights of victims, the ransom industry, and non-Western legislation, this does not detract from the overall quality of the work, which furthermore contains a number of sources in its appendixes which can be very useful to the practitioner.
[otw_shortcode_button href=”https://cimsec.org/buying-cimsec-war-bonds/18115″ size=”medium” icon_position=”right” shape=”round” color_class=”otw-blue”]Donate to CIMSEC![/otw_shortcode_button]
As clear from the title, the subtitle, and introduction, this book seeks to provide the reader with a detailed explanation of the different legal regulations and principles under which piracy is fought in one of the corners of the world where it is most pervasive, and which, crisscrossed by myriad SLOCs (sea lanes of communication), no major power can ignore it. In connection to this, the first aspect of the text we should note is that this is indeed a law book, and perhaps more accurately a “black letter law” book, in the sense that it focuses on positive law, with just the minimum amount of social, economic, and other considerations provided in Chapter one and later interspersed in the text. When the authors delve outside the strict borders of the law, it is to better explain the rationale behind legal rules, a good example being their discussion of judicial and prison capacity in- countries like Kenya (p. 174-179) and the Seychelles, which supports and complements their explanation of the agreements signed between them and the European Union for the local trial and imprisonment of pirates. Having said that, they also discuss possible future developments of the law, such as specialized international tribunals to deal with piracy (p. 179-184).
A second important characteristic we may stress is the logical fashion in which the text is divided into parts, and then subdivided into chapters, which very much aids for the reader who wishes to go through the text from beginning to end, and those who prefer to go straight to one of the issues discussed in the volume. A third strong point is that, while focused on positive law, the authors stop to discuss areas where applicable rules may not be clear or even be controversial, providing a summary of arguments and their own views. An example is the practice of embarking law-enforcement personnel from one country on a naval (or state) ship of another, with the associated legal complexities.

The Book’s Strong Points: The text provides a comprehensive look at applicable legislation and extensive discussion of unclear aspects. As noted, the authors make an extensive effort to cover the different legal aspects of the fight against piracy, adding their commentary and summaries of other views where positive law is unclear or developing. Examples include three possible interpretations of Article 105 UNCLOS, providing universal or limited criminal jurisdiction, a conflict-of-law rule, or a reaffirmation “that prosecution is based on domestic criminal law and procedure” (p. 149-151), and a discussion of the differences between transfers and extradition, noting how generally speaking “in the piracy context, the change in custody is not brought about by the formal means of extradition” and “transfers in the piracy context do not fulfill the characteristics of deportations or exclusions.” (p. 192-194)
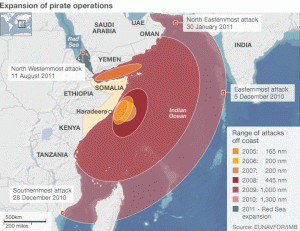
Three gaps: Non-Western Views, Piracy Victims, and the Ransom Industry and Middlemen
There are three aspects that, if incorporated in future editions of the book, may make this work even more complete. First of all, we should note a lack of Chinese, Indian, Japanese, Russian, and South Korean views, even though all these countries contribute to the struggle against piracy in the Horn of Africa. It would be interesting to find some legal commentary, domestic legislation, or actual cases, from these jurisdictions. Second, we cannot fail but note a complete and utter disregard for piracy victims, who are basically absent from the text. While the death penalty, torture, and the principle of “non-refoulement” are dealt with extensively (p. 210-220), there is no discussion of reparations for victims, and of their procedural standing other than when serving as a connection point for states to exercise jurisdiction.
The authors’ concern with the human rights of alleged and convicted pirates is commendable, and so is their extensive treatment of those rights in their book, but caring about the rights of the accused should not be seen as incompatible with at least providing some cursory explanation of those of the victims. Finally, another notable absence is that of the “middlemen” and more widely the “industry” managing ransoms, and their possible criminal liabilities. No look at the legal framework of the fight against piracy is complete without an examination of the rules and practice designed to strangle their finance, but despite the subject occasionally emerging in the pages of the book, there is no section specifically dealing with it. Is it perhaps too sensitive?
Conclusions: It is a useful and quite comprehensive study, though suffering from some gaps. We can thus conclude that this is a book that anybody interested in piracy and counter-piracy operations, the law of the sea, and more generally maritime and naval affairs, will find useful, both as a detailed introduction to the legal rules applicable to counter-piracy operations, and as a reference work. It is to be hoped, however, that future editions incorporate non-Western views, victims’ rights, and the law applicable to pirate financing.
Alex Calvo is a guest professor at Nagoya University (Japan) focusing on security and defence policy, international law, and military history in the Indian-Pacific Ocean. Region. A member of the Center for International Maritime Security (CIMSEC) and Taiwan’s South China Sea Think-Tank, he is currently writing a book about Asia’s role and contribution to the Allied victory in the Great War. He tweets @Alex__Calvo and his work can be found here.
[otw_shortcode_button href=”https://cimsec.org/buying-cimsec-war-bonds/18115″ size=”medium” icon_position=”right” shape=”round” color_class=”otw-blue”]Donate to CIMSEC![/otw_shortcode_button]





 One of the most vexing questions in international law is determining under what circumstances a state may lawfully use military force against another state or non-state actor. The U.N. Charter takes a very conservative approach: use of force, according to Article 51, is authorized “if an armed attack occurs against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security.”1 The international community has long since abandoned the notion that a state must wait until it is actually under attack before it can employ military force. Instead, the concept of “imminence” has been read into Article 51. Daniel Webster famously articulated this rule after the so-called Caroline case: preemptive force can be used only if there is “a necessity of self-defence, instant, overwhelming, leaving no choice of means, and no moment of deliberation.”2 But even this more deferential rule has proven unworkable in the age of modern warfare.
One of the most vexing questions in international law is determining under what circumstances a state may lawfully use military force against another state or non-state actor. The U.N. Charter takes a very conservative approach: use of force, according to Article 51, is authorized “if an armed attack occurs against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security.”1 The international community has long since abandoned the notion that a state must wait until it is actually under attack before it can employ military force. Instead, the concept of “imminence” has been read into Article 51. Daniel Webster famously articulated this rule after the so-called Caroline case: preemptive force can be used only if there is “a necessity of self-defence, instant, overwhelming, leaving no choice of means, and no moment of deliberation.”2 But even this more deferential rule has proven unworkable in the age of modern warfare. 