By Marjorie Greene
In our current information age, there appear to be many trends that are reshaping the naval approach to operations in support of HA/DR. Among them are the following:
- The extremely broad availability of advanced information and communications technologies that place unprecedented powers of information creation, processing, and distribution in the hands of almost anyone who wants them – friend and foe alike;
- The increasing complexity of missions as naval forces increasingly form partnerships with various civilian agencies and nongovernmental organizations;
- The rising importance of decentralized operations;
- The data deluge – the unprecedented volume of raw and processed information with which humans must contend.
All of these trends are reinforced by the rapid rise of social media. Many naval analysts are conducting research that will give insight into how social networks can be exploited, especially during HA/DR operations.
Deeper Civil-Naval Integration Will Be Needed for HA/DR
To help frame and inform studies about the true value of “soft power” missions in the future, CSIS conducted a study in March, 2013 of “U.S. Navy Humanitarian Assistance in an Era of Austerity.” Chaired by Admiral Gary Roughead (USN Ret.), formerly Chief of Naval Operations, the study discusses the emergence of proactive humanitarian assistance and the need for deeper civil-military integration. This will be a challenge unless the military has the cultural knowledge to know whom to communicate with during these missions.
There are still major barriers to using social media for naval operations when warfighters respond to crises. For example, how can we use social networks for theater operations in such a way that the data can be combined with traditional command and control tools (usually classified) for naval operations? How can we overcome the considerable challenge posed by information overload? How can we reconcile the traditional decision-making of hierarchically oriented commanders with that of the civilian sector which is currently cooperative and collaborative?
Until recently, most basic research has focused on developing technical solutions to filter signals from noise in online social media. But this is starting to change. There is less emphasis on techniques such as keywords to filter or classify social network data into meaningful elements and more emphasis on introducing new methodologies to come to a conclusion about the importance, utility, and meaning of the data.
I have also been looking for alternative methodologies to evaluate the impact of incorporating information from social media streams in HA/DR operations. Analyses have shown that naval officers often lack the regional cultural knowledge to know whom to communicate with in HR/DR missions and must build working relationships with new groups of stakeholders and responders for each mission. Naval officers are required to develop the cultural connections to conduct the mission and the operational data shows that this process often takes too long. It may be that social media can facilitate these bonds and relationships.
Social media is changing the way information is diffused and decisions are made, especially for HA/DR missions when there is increased emphasis on commands to share critical information with government and nongovernmental organizations. As the community of interest grows during a crisis, it will be important to ensure that information is shared with appropriate organizations for different aspects of the mission such as evacuation procedures, hospital sites, location of seaports and airports, and other relevant topics. Social media can increase interoperability with non-military organizations and create a faster decision cycle. For example, studies have shown that even using traditional messaging, in the first 14 days of the U.S. Southern Command’s Haiti HA/DR mission, the community of interest grew to more than 1,900 users!

Operational conditions vary considerably among incidents and coordination between different groups is often set up in an ad hoc manner. What is needed is a methodology that will help to find appropriate people with whom to share information for particular aspects of the mission during a wide range of events. A potential methodology might be to pro-actively establish relationships before a crisis occurs and a model for doing this is presented below. The model mimics the famous experiment of social psychologist Stanley Milgram, who provided the first empirical evidence of “six degrees of separation” when constructing paths from friend to friend as in a social network.
The Stanley Milgram Experiments
In his famous series of experiments in the 1960’s, Stanley Milgram hypothesized that short paths can be found to quickly reach a target destination when an individual mails a letter to someone he or she knows on a first-name basis with the instructions to forward it on in this way toward the target as quickly as possible. The letter eventually moved from friend to friend, with the successful letters making the target in a median of six steps. This kind of experiment – constructing paths through social networks to distant target individuals – has been repeated by a number of other groups in subsequent decades.
The Model
In an approach similar to the Milgram experiments, I propose to use a unique message addressing rule which constructs social networks as events occur. It is an approach to intelligent agent-based computations that builds on behavioral models of animal colonies. These animal models show how colonies can detect and respond to unanticipated environmental changes without a centralized communications and control system. For example, the ant routing algorithm tells us that when an ant forages for food, it lays pheromones on a trail from source to destination. When it arrives at its destination, it returns to the source following the same path it came from. If other ants have travelled the same path, the pheromone level is higher. Similarly, if other ants have not travelled along the path, the pheromone level is lower. If every ant tries to choose the trail that has higher pheromone concentration, eventually the pheromones accumulate when multiple ants use the same path and evaporate when no ant passes.
Just as an ant leaves a chemical trace of its movement along a path, this simulated agent attaches traces of previous contacts by means of “digital pheromones” to each message that it sends. This is done by ensuring that all communicators along a path are kept aware of all previous communicators in the path. Suppose, for example, “A”, “B”, and “C” represent three naval warfighters using a social network. “A” starts a path on a particular topic by sending a message to “B”. “B”, in turn, decides to send a message to “C” on the same topic. Thus far, this is similar to the Milgram experiment, in which a “path” was created as a letter was forwarded from friend to friend until it reached a designated “target” in the network. However, in this case the target “emerges” from the interaction of A, B, and C. Another major difference is that a simple message addressing rule is used that asks each communicator to “copy” all previous communicators on a topic when it chooses to send a message on that topic.
The diagram below illustrates an analysis of an actual event in which A, B, C, D, and E (who are commands represented on the Y-axis) communicated using traditional messaging during a humanitarian assistance operation. The diagram shows that 7 messages were sent between the commands for this event. (An arrow from A to B means “A sent a message to B”.) So, for example, message 1 is from command A to his subordinate Command B at 0021 and starts the message path asking for supplies to be sent to the area. (Command A also sent this message to B’s subordinates “for information”.) In message 2, Command B addressed his own subordinate Command D, as well as Command E, a non-government organization, who ultimately sent the supplies.
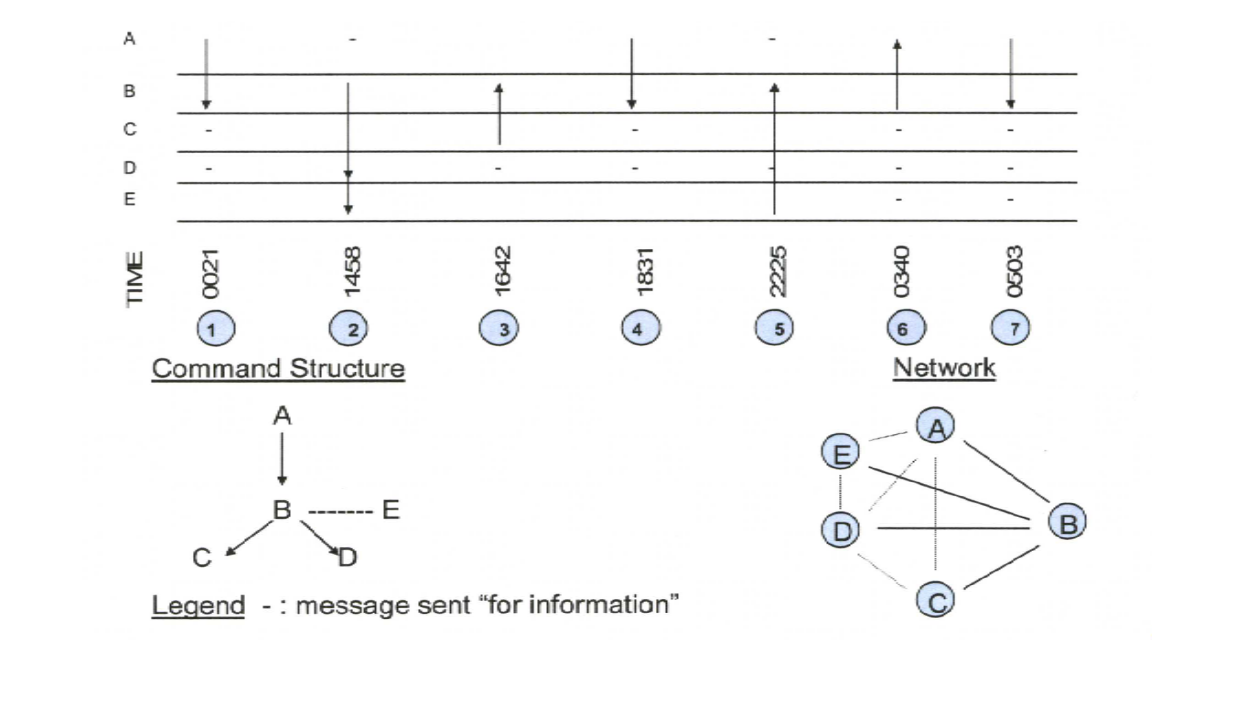
In the event illustrated above, the third message from C to B asks the status of supplies. Because C was addressed in the first message, he knew of the request for supplies. However, Command C was not copied in the 2nd message from B and did not know about this message. This is why I suggest that a message-addressing rule will be very important in the future use of social media. It will achieve two major objectives:
- It will guarantee that all warfighters along the path are automatically kept informed of previous communicators in the path on the topic. This provides the important feedback that socio-technologists have shown to be very important in the control of large-scale coordination during evolving operations;
- It avoids keywords by defining a topic through communication that represents a path in a social network. This provides a way to deal with changing topics and an uncertain organizational structure in an evolving crisis.
Conclusion
I have developed an approach to coordinate activities during HA/DR missions as naval warfighters continue to see greater use of nonhierarchical communications for complex interactions. Collaboration with external partners is expected to grow when conducting HA/DR missions. If a social network of trusted coordinators were established before a crisis occurred, military and civilian commanders would already have working relationships with each other and could plan HA/DR missions in advance. Deeper integration could be achieved using social media to exchange information and the right group of trusted collaborators would be pro-actively defined. Such an approach would assist in sustaining planned assistance in an era of global austerity.
Marjorie Greene is a research analyst at CNA. She has more than 25 years of management experience in both government and commercial organizations and has recently specialized in finding S&T solutions for the U.S. Marine Corps. She is active in both the Military Operations Research Society and IEEE, where she serves on the Medical Technology Policy Committee and the Bioterrorism Working Group.
Featured Image Source: Open DNS Security Labs Visualization of Canada’s Internet Infrastructure